| Memo | Issued To | Subject | Date Issued / Revised |
| All State-Chartered Banks, Foreign Bank Agencies, Electronic Data Processors | Rating Systems for Commercial Banks, Trust Departments, Foreign Bank Agencies, and Electronic Data Processing Operations Supervised by the Department of Banking | 05-12-10 | |
| All State-Chartered Trust Companies | Trust Company Rating System | 12-31-98 | |
| All State-Chartered Banks | Examination Frequency for State-chartered Banks | 04-11-24 | |
| All State-Chartered Trust Companies | Examination Frequency for Trust Companies | 04-11-24 | |
| All State-Chartered Banks | Policy on Enforcement Actions for State-Chartered Banks | 10-25-23 | |
| All Institutions Regulated by the Texas Department of Banking | Request for Reconsideration of Examination Finding (REF) | 09-07-23 | |
| All State-Chartered Banks, | Policies Regarding Investment Securities | 03-06-15 | |
| All State-Chartered Banks | Policy for Other Real Estate Owned (OREO) | 10/01/20 | |
| All State-Chartered Banks and Trust Companies | Business Plans and Strategic Planning | 04-03-14 | |
| All State-Chartered Banks | Bank Owned Life Insurance (BOLI) | 03-01-17 | |
| All State-Chartered Banks | Policy for Temporary Mortgage Purchase Programs | 07-31-96 | |
| All State-Chartered Banks and Trust Companies | Communication with External Auditors | 07-31-96 | |
| All Texas State-Chartered Banks | Providing Consumer Complaint Notices | 05-03-16 | |
| All State-Chartered Banks, Trust Companies, | Information Technology Examination Frequency and Ratings | 04-11-24 | |
| 1025 | Rescinded 2-7-24 |
| 02-07-24 |
| Chief Executive Officers of State-Chartered Banks | Risk Management of Account Takeovers | 09-30-19 | |
| Chief Executive Officers of State-Chartered Trust Companies | Policy on Enforcement Actions for State-Chartered Trust Companies | 10-25-23 | |
| All State-Chartered Trust Companies | Policy for Other Real Estate Owned (OREO) for State-Chartered Trust Companies | 11-01-21 | |
| 1033 | Rescinded 4-11-24 |
| 04-11-24 |
| 1034 | Rescinded 12-01-16 |
| 12-01-16 |
| All State-Chartered Banks | Bargain Purchases and Assisted Acquisitions | 05-11-15 | |
| All Institutions Regulated by the Texas Department of Banking | Effect of Criminal Convictions on Licensing | 07-17-24 | |
| All State-Chartered Banks and Trust Companies and | Permissible Uses of “Bank” and Related Terms in Marketing and Other Limits Related to Marketing Regulated Financial Services | 07-17-24 |
May 12, 2010 (rev)
| TO: | All State-Chartered Banks, Foreign Bank Agencies, and |
| FROM: | Charles G. Cooper, Commissioner |
| SUBJECT: | Rating Systems for Commercial Banks, Trust Departments, |
Background
Supervisory Memorandum 1001 was previously modified on 3/20/97 and 12/31/98 to adopt revised federal rating systems for financial institutions, trust departments, and information technology systems. This revision further clarifies the rating system for trust departments.
Overview
This Memorandum communicates the rating systems used by the Department to evaluate the condition of entities under its supervision, including state-chartered commercial banks and their trust and electronic data processing (EDP) departments, foreign bank agencies licensed in Texas, and independent EDP providers servicing entities supervised by the Department. The Department also supervises state-chartered trust companies; however, the rating system for these entities is communicated separately in Supervisory Memorandum - 1002. This Memorandum also addresses the Department's policy regarding the disclosure of ratings.
Rating Policy
The rating systems utilized by the Department, and entities to which they are applicable, are reflected in the following table. The text of the rating systems is attached to this Memorandum.
|
Disclosure Policy
The rating systems assign a component rating to each area of evaluation, as well as a composite rating for the overall institution. It is the policy of this Department to advise boards of directors of regulated entities of all of the ratings assigned by this agency, pursuant to either an independent examination, or a joint or concurrent examination with federal regulators. By disclosing all component or performance ratings, we believe the directors will be more fully informed of the condition of the entities and, therefore, be better equipped to address all financial and operational deficiencies.
While the ratings assigned by the Department may be the same as those assigned by the respective federal agency, some differences in component and/or composite ratings may exist. It is the Department's policy to only disclose the ratings directly assigned by the Department.
The board of directors of each entity will be advised of the ratings assigned by the Department of Banking in a separate, confidential letter addressed to the board. The ratings will not be a matter of public information. It is important to note that the overall composite rating is not an arithmetic average of the individual component or performance ratings, but the composite rating should be consistent with the individual component or performance ratings.
Attachments
UNIFORM FINANCIAL
INSTITUTIONS RATING SYSTEM1
INTRODUCTION
The Uniform Financial Institutions Rating System (UFIRS) was adopted by the Federal Financial Institutions Examination Council (FFIEC) on November 13, 1979. Over the years, the UFIRS has proven to be an effective internal supervisory tool for evaluating the soundness of financial institutions on a uniform basis and for identifying those institutions requiring special attention or concern. A number of changes, however, have occurred in the banking industry and in the Federal supervisory agencies' policies and procedures which have prompted a review and revision of the 1979 rating system. The revisions to UFIRS include the addition of a sixth component addressing sensitivity to market risks, the explicit reference to the quality of risk management processes in the management component, and the identification of risk elements within the composite and component rating descriptions.
The revisions to UFIRS are not intended to add to the regulatory burden of institutions or require additional policies or processes. The revisions are intended to promote and complement efficient examination processes. The revisions have been made to update the rating system, while retaining the basic framework of the original rating system.
The UFIRS takes into consideration certain financial, managerial, and compliance factors that are common to all institutions. Under this system, the supervisory agencies endeavor to ensure that all financial institutions are evaluated in a comprehensive and uniform manner, and that supervisory attention is appropriately focused on the financial institutions exhibiting financial and operational weaknesses or adverse trends.
The UFIRS also serves as a useful vehicle for identifying problem or deteriorating financial institutions, as well as for categorizing institutions with deficiencies in particular component areas. Further, the rating system assists Congress in following safety and soundness trends and in assessing the aggregate strength and soundness of the financial industry. As such, the UFIRS assists the agencies in fulfilling their collective mission of maintaining stability and public confidence in the nation's financial system.
OVERVIEW
Under the UFIRS, each financial institution is assigned a composite rating based on an evaluation and rating of six essential components of an institution's financial condition and operations. These component factors address the adequacy of capital, the quality of assets, the capability of management, the quality and level of earnings, the adequacy of liquidity, and the sensitivity to market risk. Evaluations of the components take into consideration the institution's size and sophistication, the nature and complexity of its activities, and its risk profile.
Composite and component ratings are assigned based on a 1 to 5 numerical scale. A 1 indicates the highest rating, strongest performance and risk management practices, and least degree of supervisory concern, while a 5 indicates the lowest rating, weakest performance, inadequate risk management practices and, therefore, the highest degree of supervisory concern.
The composite rating generally bears a close relationship to the component ratings assigned. However, the composite rating is not derived by computing an arithmetic average of the component ratings. Each component rating is based on a qualitative analysis of the factors comprising that component and its interrelationship with the other components. When assigning a composite rating, some components may be given more weight than others depending on the situation at the institution. In general, assignment of a composite rating may incorporate any factor that bears significantly on the overall condition and soundness of the financial institution. Assigned composite and component ratings are disclosed to the institution's board of directors and senior management.
The ability of management to respond to changing circumstances and to address the risks that may arise from changing business conditions, or the initiation of new activities or products, is an important factor in evaluating a financial institution's overall risk profile and the level of supervisory attention warranted. For this reason, the management component is given special consideration when assigning a composite rating.
The ability of management to identify, measure, monitor, and control the risks of its operations is also taken into account when assigning each component rating. It is recognized, however, that appropriate management practices vary considerably among financial institutions, depending on their size, complexity, and risk profile. For less complex institutions engaged solely in traditional banking activities and whose directors and senior managers, in their respective roles, are actively involved in the oversight and management of day-to-day operations, relatively basic management systems and controls may be adequate. At more complex institutions, on the other hand, detailed and formal management systems and controls are needed to address their broader range of financial activities and to provide senior managers and directors, in their respective roles, with the information they need to monitor and direct day-to-day activities. All institutions are expected to properly manage their risks. For less complex institutions engaging in less sophisticated risk taking activities, detailed or highly formalized management systems and controls are not required to receive strong or satisfactory component or composite ratings.
Foreign Branch and specialty examination findings and the ratings assigned to those areas are taken into consideration, as appropriate, when assigning component and composite ratings under UFIRS. The specialty examination areas include: Compliance, Community Reinvestment, Government Security Dealers, Information Systems, Municipal Security Dealers, Transfer Agent, and Trust.
The following two sections contain the composite rating definitions, and the descriptions and definitions for the six component ratings.
COMPOSITE RATINGS
Composite ratings are based on a careful evaluation of an institution's managerial, operational, financial, and compliance performance. The six key components used to assess an institution's financial condition and operations are: capital adequacy, asset quality, management capability, earnings quantity and quality, the adequacy of liquidity, and sensitivity to market risk. The rating scale ranges from 1 to 5, with a rating of 1 indicating: the strongest performance and risk management practices relative to the institution's size, complexity, and risk profile; and the level of least supervisory concern. A 5 rating indicates: the most critically deficient level of performance; inadequate risk management practices relative to the institution's size, complexity, and risk profile; and the greatest supervisory concern. The composite ratings are defined as follows:
Composite 1
Financial institutions in this group are sound in every respect and generally have components rated 1 or 2. Any weaknesses are minor and can be handled in a routine manner by the board of directors and management. These financial institutions are the most capable of withstanding the vagaries of business conditions and are resistant to outside influences such as economic instability in their trade area. These financial institutions are in substantial compliance with laws and regulations. As a result, these financial institutions exhibit the strongest performance and risk management practices relative to the institution's size, complexity, and risk profile, and give no cause for supervisory concern.
Composite 2
Financial institutions in this group are fundamentally sound. For a financial institution to receive this rating, generally no component rating should be more severe than 3. Only moderate weaknesses are present and are well within the board of directors' and management's capabilities and willingness to correct. These financial institutions are stable and are capable of withstanding business fluctuations. These financial institutions are in substantial compliance with laws and regulations. Overall risk management practices are satisfactory relative to the institution's size, complexity, and risk profile. There are no material supervisory concerns and, as a result, the supervisory response is informal and limited.
Composite 3
Financial institutions in this group exhibit some degree of supervisory concern in one or more of the component areas. These financial institutions exhibit a combination of weaknesses that may range from moderate to severe; however, the magnitude of the deficiencies generally will not cause a component to be rated more severely than 4. Management may lack the ability or willingness to effectively address weaknesses within appropriate time frames. Financial institutions in this group generally are less capable of withstanding business fluctuations and are more vulnerable to outside influences than those institutions rated a composite 1 or 2. Additionally, these financial institutions may be in significant noncompliance with laws and regulations. Risk management practices may be less than satisfactory relative to the institution's size, complexity, and risk profile. These financial institutions require more than normal supervision, which may include formal or informal enforcement actions. Failure appears unlikely, however, given the overall strength and financial capacity of these institutions.
Composite 4
Financial institutions in this group generally exhibit unsafe and unsound practices or conditions. There are serious financial or managerial deficiencies that result in unsatisfactory performance. The problems range from severe to critically deficient. The weaknesses and problems are not being satisfactorily addressed or resolved by the board of directors and management. Financial institutions in this group generally are not capable of withstanding business fluctuations. There may be significant noncompliance with laws and regulations. Risk management practices are generally unacceptable relative to the institution's size, complexity, and risk profile. Close supervisory attention is required, which means, in most cases, formal enforcement action is necessary to address the problems. Institutions in this group pose a risk to the deposit insurance fund. Failure is a distinct possibility if the problems and weaknesses are not satisfactorily addressed and resolved.
Composite 5
Financial institutions in this group exhibit extremely unsafe and unsound practices or conditions; exhibit a critically deficient performance; often contain inadequate risk management practices relative to the institution's size, complexity, and risk profile; and are of the greatest supervisory concern. The volume and severity of problems are beyond management's ability or willingness to control or correct. Immediate outside financial or other assistance is needed in order for the financial institution to be viable. Ongoing supervisory attention is necessary. Institutions in this group pose a significant risk to the deposit insurance fund and failure is highly probable.
COMPONENT RATINGS
Each of the component rating descriptions is divided into three sections: an introductory paragraph; a list of the principal evaluation factors that relate to that component; and a brief description of each numerical rating for that component. Some of the evaluation factors are reiterated under one or more of the other components to reinforce the interrelationship between components. The listing of evaluation factors for each component rating is in no particular order of importance.
Capital Adequacy
A financial institution is expected to maintain capital commensurate with the nature and extent of risks to the institution and the ability of management to identify, measure, monitor, and control these risks. The effect of credit, market, and other risks on the institution's financial condition should be considered when evaluating the adequacy of capital. The types and quantity of risk inherent in an institution's activities will determine the extent to which it may be necessary to maintain capital at levels above required regulatory minimums to properly reflect the potentially adverse consequences that these risks may have on the institution's capital.
The capital adequacy of an institution is rated based upon, but not limited to, an assessment of the following evaluation factors:
• The level and quality of capital and the overall financial condition of the institution.
• The ability of management to address emerging needs for additional capital.
• The nature, trend, and volume of problem assets, and the adequacy of allowances for loan and lease losses and other valuation reserves.
• Balance sheet composition, including the nature and amount of intangible assets, market risk, concentration risk, and risks associated with nontraditional activities.
• Risk exposure represented by off-balance sheet activities.
• The quality and strength of earnings, and the reasonableness of dividends.
• Prospects and plans for growth, as well as past experience in managing growth.
• Access to capital markets and other sources of capital, including support provided by a parent holding company.
Capital Adequacy Ratings
1 A rating of 1 indicates a strong capital level relative to the institution's risk profile.
2 A rating of 2 indicates a satisfactory capital level relative to the financial institution's risk profile.
3 A rating of 3 indicates a less than satisfactory level of capital that does not fully support the institution's risk profile. The rating indicates a need for improvement, even if the institution's capital level exceeds minimum regulatory and statutory requirements.
4 A rating of 4 indicates a deficient level of capital. In light of the institution's risk profile, viability of the institution may be threatened. Assistance from shareholders or other external sources of financial support may be required.
5 A rating of 5 indicates a critically deficient level of capital such that the institution's viability is threatened. Immediate assistance from shareholders or other external sources of financial support is required.
Asset Quality
The asset quality rating reflects the quantity of existing and potential credit risk associated with the loan and investment portfolios, other real estate owned, and other assets, as well as off-balance sheet transactions. The ability of management to identify, measure, monitor, and control credit risk is also reflected here. The evaluation of asset quality should consider the adequacy of the allowance for loan and lease losses and weigh the exposure to counterparty, issuer, or borrower default under actual or implied contractual agreements. All other risks that may affect the value or marketability of an institution's assets, including, but not limited to, operating, market, reputation, strategic, or compliance risks, should also be considered.
The asset quality of a financial institution is rated based upon, but not limited to, an assessment of the following evaluation factors:
• The adequacy of underwriting standards, soundness of credit administration practices, and appropriateness of risk identification practices.
• The level, distribution, severity, and trend of problem, classified, nonaccrual, restructured, delinquent, and nonperforming assets for both on- and off-balance sheet transactions.
• The adequacy of the allowance for loan and lease losses and other asset valuation reserves.
• The credit risk arising from or reduced by off-balance sheet transactions, such as unfunded commitments, credit derivatives, commercial and standby letters of credit, and lines of credit.
• The diversification and quality of the loan and investment portfolios.
• The extent of securities underwriting activities and exposure to counterparties in trading activities.
• The existence of asset concentrations.
• The adequacy of loan and investment policies, procedures, and practices.
• The ability of management to properly administer its assets, including the timely identification and collection of problem assets.
• The adequacy of internal controls and management information systems.
• The volume and nature of credit documentation exceptions.
Asset Quality Ratings
1 A rating of 1 indicates strong asset quality and credit administration practices. Identified weaknesses are minor in nature and risk exposure is modest in relation to capital protection and management's abilities. Asset quality in such institutions is of minimal supervisory concern.
2 A rating of 2 indicates satisfactory asset quality and credit administration practices. The level and severity of classifications and other weaknesses warrant a limited level of supervisory attention. Risk exposure is commensurate with capital protection and management's abilities.
3 A rating of 3 is assigned when asset quality or credit administration practices are less than satisfactory. Trends may be stable or indicate deterioration in asset quality or an increase in risk exposure. The level and severity of classified assets, other weaknesses, and risks require an elevated level of supervisory concern. There is generally a need to improve credit administration and risk management practices.
4 A rating of 4 is assigned to financial institutions with deficient asset quality or credit administration practices. The levels of risk and problem assets are significant, inadequately controlled, and subject the financial institution to potential losses that, if left unchecked, may threaten its viability.
5 A rating of 5 represents critically deficient asset quality or credit administration practices that present an imminent threat to the institution's viability.
Management
The capability of the board of directors and management, in their respective roles, to identify, measure, monitor, and control the risks of an institution's activities and to ensure a financial institution's safe, sound, and efficient operation in compliance with applicable laws and regulations is reflected in this rating. Generally, directors need not be actively involved in day-to-day operations; however, they must provide clear guidance regarding acceptable risk exposure levels and ensure that appropriate policies, procedures, and practices have been established. Senior management is responsible for developing and implementing policies, procedures, and practices that translate the board's goals, objectives, and risk limits into prudent operating standards.
Depending on the nature and scope of an institution's activities, management practices may need to address some or all of the following risks: credit, market, operating or transaction, reputation, strategic, compliance, legal, liquidity, and other risks. Sound management practices are demonstrated by: active oversight by the board of directors and management; competent personnel; adequate policies, processes, and controls taking into consideration the size and sophistication of the institution; maintenance of an appropriate audit program and internal control environment; and effective risk monitoring and management information systems. This rating should reflect the board's and management's ability as it applies to all aspects of banking operations as well as other financial service activities in which the institution is involved.
The capability and performance of management and the board of directors is rated based upon, but not limited to, an assessment of the following evaluation factors:
• The level and quality of oversight and support of all institution activities by the board of directors and management.
• The ability of the board of directors and management, in their respective roles, to plan for, and respond to, risks that may arise from changing business conditions or the initiation of new activities or products.
• The adequacy of, and conformance with, appropriate internal policies and controls addressing the operations and risks of significant activities.
• The accuracy, timeliness, and effectiveness of management information and risk monitoring systems appropriate for the institution's size, complexity, and risk profile.
• The adequacy of audits and internal controls to: promote effective operations and reliable financial and regulatory reporting; safeguard assets; and ensure compliance with laws, regulations, and internal policies.
• Compliance with laws and regulations. Responsiveness to recommendations from auditors and supervisory authorities.
• Management depth and succession.
• The extent that the board of directors and management is affected by, or susceptible to, dominant influence or concentration of authority.
• Reasonableness of compensation policies and avoidance of self-dealing.
• Demonstrated willingness to serve the legitimate banking needs of the community.
• The overall performance of the institution and its risk profile.
Management Ratings
1 A rating of 1 indicates strong performance by management and the board of directors and strong risk management practices relative to the institution's size, complexity, and risk profile. All significant risks are consistently and effectively identified, measured, monitored, and controlled. Management and the board have demonstrated the ability to promptly and successfully address existing and potential problems and risks.
2 A rating of 2 indicates satisfactory management and board performance and risk management practices relative to the institution's size, complexity, and risk profile. Minor weaknesses may exist, but are not material to the safety and soundness of the institution and are being addressed. In general, significant risks and problems are effectively identified, measured, monitored, and controlled.
3 A rating of 3 indicates management and board performance that need improvement or risk management practices that are less than satisfactory given the nature of the institution's activities. The capabilities of management or the board of directors may be insufficient for the type, size, or condition of the institution. Problems and significant risks may be inadequately identified, measured, monitored, or controlled.
4 A rating of 4 indicates deficient management and board performance or risk management practices that are inadequate considering the nature of an institution's activities. The level of problems and risk exposure is excessive. Problems and significant risks are inadequately identified, measured, monitored, or controlled and require immediate action by the board and management to preserve the soundness of the institution. Replacing or strengthening management or the board may be necessary.
5 A rating of 5 indicates critically deficient management and board performance or risk management practices. Management and the board of directors have not demonstrated the ability to correct problems and implement appropriate risk management practices. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the continued viability of the institution. Replacing or strengthening management or the board of directors is necessary.
Earnings
This rating reflects not only the quantity and trend of earnings, but also factors that may affect the sustainability or quality of earnings. The quantity as well as the quality of earnings can be affected by excessive or inadequately managed credit risk that may result in loan losses and require additions to the allowance for loan and lease losses, or by high levels of market risk that may unduly expose an institution's earnings to volatility in interest rates. The quality of earnings may also be diminished by undue reliance on extraordinary gains, nonrecurring events, or favorable tax effects. Future earnings may be adversely affected by an inability to forecast or control funding and operating expenses, improperly executed or ill-advised business strategies, or poorly managed or uncontrolled exposure to other risks.
The rating of an institution's earnings is based upon, but not limited to, an assessment of the following evaluation factors:
• The level of earnings, including trends and stability.
• The ability to provide for adequate capital through retained earnings.
• The quality and sources of earnings.
• The level of expenses in relation to operations.
• The adequacy of the budgeting systems, forecasting processes, and management information systems in general.
• The adequacy of provisions to maintain the allowance for loan and lease losses and other valuation allowance accounts.
• The earnings exposure to market risk such as interest rate, foreign exchange, and price risks.
Earnings Ratings
1 A rating of 1 indicates earnings that are strong. Earnings are more than sufficient to support operations and maintain adequate capital and allowance levels after consideration is given to asset quality, growth, and other factors affecting the quality, quantity, and trend of earnings.
2 A rating of 2 indicates earnings that are satisfactory. Earnings are sufficient to support operations and maintain adequate capital and allowance levels after consideration is given to asset quality, growth, and other factors affecting the quality, quantity, and trend of earnings. Earnings that are relatively static, or even experiencing a slight decline, may receive a 2 rating provided the institution's level of earnings is adequate in view of the assessment factors listed above.
3 A rating of 3 indicates earnings that need to be improved. Earnings may not fully support operations and provide for the accretion of capital and allowance levels in relation to the institution's overall condition, growth, and other factors affecting the quality, quantity, and trend of earnings.
4 A rating of 4 indicates earnings that are deficient. Earnings are insufficient to support operations and maintain appropriate capital and allowance levels. Institutions so rated may be characterized by erratic fluctuations in net income or net interest margin, the development of significant negative trends, nominal or unsustainable earnings, intermittent losses, or a substantive drop in earnings from the previous years.
5 A rating of 5 indicates earnings that are critically deficient. A financial institution with earnings rated 5 is experiencing losses that represent a distinct threat to its viability through the erosion of capital.
Liquidity
In evaluating the adequacy of a financial institution's liquidity position, consideration should be given to the current level and prospective sources of liquidity compared to funding needs, as well as to the adequacy of funds management practices relative to the institution's size, complexity, and risk profile. In general, funds management practices should ensure that an institution is able to maintain a level of liquidity sufficient to meet its financial obligations in a timely manner and to fulfill the legitimate banking needs of its community. Practices should reflect the ability of the institution to manage unplanned changes in funding sources, as well as react to changes in market conditions that affect the ability to quickly liquidate assets with minimal loss. In addition, funds management practices should ensure that liquidity is not maintained at a high cost, or through undue reliance on funding sources that may not be available in times of financial stress or adverse changes in market conditions.
Liquidity is rated based upon, but not limited to, an assessment of the following evaluation factors:
• The adequacy of liquidity sources compared to present and future needs and the ability of the institution to meet liquidity needs without adversely affecting its operations or condition.
• The availability of assets readily convertible to cash without undue loss.
• Access to money markets and other sources of funding.
• The level of diversification of funding sources, both on- and off-balance sheet.
• The degree of reliance on short-term, volatile sources of funds, including borrowings and brokered deposits, to fund longer term assets.
• The trend and stability of deposits.
• The ability to securitize and sell certain pools of assets.
• The capability of management to properly identify, measure, monitor, and control the institution's liquidity position, including the effectiveness of funds management strategies, liquidity policies, management information systems, and contingency funding plans.
Liquidity Ratings
1 A rating of 1 indicates strong liquidity levels and well-developed funds management practices. The institution has reliable access to sufficient sources of funds on favorable terms to meet present and anticipated liquidity needs.
2 A rating of 2 indicates satisfactory liquidity levels and funds management practices. The institution has access to sufficient sources of funds on acceptable terms to meet present and anticipated liquidity needs. Modest weaknesses may be evident in funds management practices.
3 A rating of 3 indicates liquidity levels or funds management practices in need of improvement. Institutions rated 3 may lack ready access to funds on reasonable terms or may evidence significant weaknesses in funds management practices.
4 A rating of 4 indicates deficient liquidity levels or inadequate funds management practices. Institutions rated 4 may not have or be able to obtain a sufficient volume of funds on reasonable terms to meet liquidity needs.
5 A rating of 5 indicates liquidity levels or funds management practices so critically deficient that the continued viability of the institution is threatened. Institutions rated 5 require immediate external financial assistance to meet maturing obligations or other liquidity needs.
Sensitivity to Market Risk
The sensitivity to market risk component reflects the degree to which changes in interest rates, foreign exchange rates, commodity prices, or equity prices can adversely affect a financial institution's earnings or economic capital. When evaluating this component, consideration should be given to: management's ability to identify, measure, monitor, and control market risk; the institution's size; the nature and complexity of its activities; and the adequacy of its capital and earnings in relation to its level of market risk exposure.
For many institutions, the primary source of market risk arises from nontrading positions and their sensitivity to changes in interest rates. In some larger institutions, foreign operations can be a significant source of market risk. For some institutions, trading activities are a major source of market risk.
Market risk is rated based upon, but not limited to, an assessment of the following evaluation factors:
• The sensitivity of the financial institution's earnings or the economic value of its capital to adverse changes in interest rates, foreign exchanges rates, commodity prices, or equity prices.
• The ability of management to identify, measure, monitor, and control exposure to market risk given the institution's size, complexity, and risk profile.
• The nature and complexity of interest rate risk exposure arising from nontrading positions.
• Where appropriate, the nature and complexity of market risk exposure arising from trading and foreign operations.
Sensitivity to Market Risk Ratings
1 A rating of 1 indicates that market risk sensitivity is well controlled and that there is minimal potential that the earnings performance or capital position will be adversely affected. Risk management practices are strong for the size, sophistication, and market risk accepted by the institution. The level of earnings and capital provide substantial support for the degree of market risk taken by the institution.
2 A rating of 2 indicates that market risk sensitivity is adequately controlled and that there is only moderate potential that the earnings performance or capital position will be adversely affected. Risk management practices are satisfactory for the size, sophistication, and market risk accepted by the institution. The level of earnings and capital provide adequate support for the degree of market risk taken by the institution.
3 A rating of 3 indicates that control of market risk sensitivity needs improvement or that there is significant potential that the earnings performance or capital position will be adversely affected. Risk management practices need to be improved given the size, sophistication, and level of market risk accepted by the institution. The level of earnings and capital may not adequately support the degree of market risk taken by the institution.
4 A rating of 4 indicates that control of market risk sensitivity is unacceptable or that there is high potential that the earnings performance or capital position will be adversely affected. Risk management practices are deficient for the size, sophistication, and level of market risk accepted by the institution. The level of earnings and capital provide inadequate support for the degree of market risk taken by the institution.
5 A rating of 5 indicates that control of market risk sensitivity is unacceptable or that the level of market risk taken by the institution is an imminent threat to its viability. Risk management practices are wholly inadequate for the size, sophistication, and level of market risk accepted by the institution.
UNIFORM INTERAGENCY TRUST RATING SYSTEM (modified)
OVERVIEW
Under the modified UITRS, the fiduciary activities of financial institutions are assigned a composite rating based on an evaluation and rating of five essential components of an institution's fiduciary activities. These components address the following: the capability of management; the adequacy of operations, controls and audits; the quality and level of earnings; compliance with governing instruments, applicable law (including self-dealing and conflicts of interest laws and regulations), and sound fiduciary principles; and the management of fiduciary assets.
Composite and component ratings are assigned based on a 1 to 5 numerical scale. A 1 is the highest rating and indicates the strongest performance and risk management practices and the least degree of supervisory concern. A 5 is the lowest rating and indicates the weakest performance and risk management practices and, therefore, the highest degree of supervisory concern. A rating of 0 is also possible under the Asset Management component of the modified UITRS, for institutions which do not engage in any asset management activities. Evaluation of the composite and components considers the size and sophistication, the nature and complexity, and the risk profile of the institution's fiduciary activities.
The composite rating generally bears a close relationship to the component ratings assigned. However, the composite rating is not derived by computing an arithmetic average of the component ratings. Each component rating is based on a qualitative analysis of the factors comprising that component and its interrelationship with the other components. When assigning a composite rating, some components may be given more weight than others depending on the situation at the institution. In general, assignment of a composite rating may incorporate any factor that bears significantly on the overall administration of the financial institution's fiduciary activities. Assigned composite and component ratings are disclosed to the institution's board of directors and senior management.
The ability of management to respond to changing circumstances and to address the risks that may arise from changing business conditions, or the initiation of new fiduciary activities or products, is an important factor in evaluating an institution's overall fiduciary risk profile and the level of supervisory attention warranted. For this reason, the management component is given special consideration when assigning a composite rating.
The ability of management to identify, measure, monitor, and control the risks of its fiduciary operations is also taken into account when assigning each component rating. It is recognized, however, that appropriate management practices may vary considerably among financial institutions, depending on the size, complexity and risk profiles of their fiduciary activities. For less complex institutions engaged solely in traditional fiduciary activities and whose directors and senior managers are actively involved in the oversight and management of day-to-day operations, relatively basic management systems and controls may be adequate. On the other hand, at more complex institutions, detailed and formal management systems and controls are needed to address a broader range of activities and to provide senior managers and directors with the information they need to supervise day-to-day activities.
All institutions are expected to properly manage their risks. For less complex institutions engaging in less risky activities, detailed or highly formalized management systems and controls are not required to receive strong or satisfactory component or composite ratings.
The following two sections contain the composite rating definitions, and the descriptions and definitions for the five component ratings.
COMPOSITE RATINGS
Composite ratings are based on a careful evaluation of how an institution conducts its fiduciary activities. The review encompasses the capability of management, the soundness of policies and practices, the quality of service rendered to the public, and the effect of fiduciary activities upon the soundness of the institution. The five key components used to assess an institution's fiduciary activities are: the capability of management; the adequacy of operations, controls and audits; the quality and level of earnings; compliance with governing instruments, applicable law (including self-dealing and conflicts of interest laws and regulations), and sound fiduciary principles; and the management of fiduciary assets. The composite ratings are defined as follows:
Composite 1
Administration of fiduciary activities is sound in every respect. Generally all components are rated 1 or 2. Any weaknesses are minor and can be handled in a routine manner by management. The institution is in substantial compliance with fiduciary laws and regulations. Risk management practices are strong relative to the size, complexity, and risk profile of the institution's fiduciary activities. Fiduciary activities are conducted in accordance with sound fiduciary principles and give no cause for supervisory concern.
Composite 2
Administration of fiduciary activities is fundamentally sound. Generally no component rating should be more severe than 3. Only moderate weaknesses are present and are well within management's capabilities and willingness to correct. Fiduciary activities are conducted in substantial compliance with laws and regulations. Overall risk management practices are satisfactory relative to the institution's size, complexity, and risk profile. There are no material supervisory concerns and, as a result, the supervisory response is informal and limited.
Composite 3
Administration of fiduciary activities exhibits some degree of supervisory concern in one or more of the component areas. A combination of weaknesses exists that may range from moderate to severe; however, the magnitude of the deficiencies generally does not cause a component to be rated more severely than 4. Management may lack the ability or willingness to effectively address weaknesses within appropriate time frames. Additionally, fiduciary activities may reveal some significant noncompliance with laws and regulations. Risk management practices may be less than satisfactory relative to the institution's size, complexity, and risk profile. While problems of relative significance may exist, they are not of such importance as to pose a threat to the trust beneficiaries generally, or to the soundness of the institution. The institution's fiduciary activities require more than normal supervision and may include formal or informal enforcement actions.
Composite 4
Fiduciary activities generally exhibit unsafe and unsound practices or conditions, resulting in unsatisfactory performance. The problems range from severe to critically deficient and may be centered around inexperienced or inattentive management, weak or dangerous operating practices, or an accumulation of unsatisfactory features of lesser importance. The weaknesses and problems are not being satisfactorily addressed or resolved by the board of directors and management. There may be significant noncompliance with laws and regulations. Risk management practices are generally unacceptable relative to the size, complexity, and risk profile of fiduciary activities. These problems pose a threat to the account beneficiaries generally and, if left unchecked, could evolve into conditions that could cause significant losses to the institution and ultimately undermine the public confidence in the institution. Close supervisory attention is required, which means, in most cases, formal enforcement action is necessary to address the problems.
Composite 5
Fiduciary activities are conducted in an extremely unsafe and unsound manner. Administration of fiduciary activities is critically deficient in numerous major respects, with problems resulting from incompetent or neglectful administration, flagrant and/or repeated disregard for laws and regulations, or a willful departure from sound fiduciary principles and practices. The volume and severity of problems are beyond management's ability or willingness to control or correct. Such conditions evidence a flagrant disregard for the interests of the beneficiaries and may pose a serious threat to the soundness of the institution. Continuous close supervisory attention is warranted and may include termination of the institution's fiduciary activities.
COMPONENT RATINGS
Each of the component rating descriptions is divided into three sections: a narrative description of the component; a list of the principal factors used to evaluate that component; and a description of each numerical rating for that component. Some of the evaluation factors are reiterated under one or more of the other components to reinforce the interrelationship among components. The listing of evaluation factors is in no particular order of importance.
Management
This rating reflects the capability of the board of directors and management, in their respective roles, to identify, measure, monitor and control the risks of an institution's fiduciary activities. It also reflects their ability to ensure that the institution's fiduciary activities are conducted in a safe and sound manner, and in compliance with applicable laws and regulations. Directors should provide clear guidance regarding acceptable risk exposure levels and ensure that appropriate policies, procedures and practices are established and followed. Senior fiduciary management is responsible for developing and implementing policies, procedures and practices that translate the board's objectives and risk limits into prudent operating standards.
Depending on the nature and scope of an institution's fiduciary activities, management practices may need to address some or all of the following risks: reputation, operating or transaction, strategic, compliance, legal, credit, market, liquidity and other risks. Sound management practices are demonstrated by: active oversight by the board of directors and management; competent personnel; adequate policies, processes, and controls that consider the size and complexity of the institution's fiduciary activities; and effective risk monitoring and management information systems. This rating should reflect the board's and management's ability as it applies to all aspects of fiduciary activities in which the institution is involved.
The management rating is based upon an assessment of the capability and performance of management and the board of directors, including, but not limited to, the following evaluation factors:
• The level and quality of oversight and support of fiduciary activities by the board of directors and management, including committee structure and adequate documentation of committee actions.
• The ability of the board of directors and management, in their respective roles, to plan for, and respond to, risks that may arise from changing business conditions or the introduction of new activities or products.
• The adequacy of, and conformance with, appropriate internal policies, practices and controls addressing the operations and risks of significant fiduciary activities.
• The accuracy, timeliness, and effectiveness of management information and risk monitoring systems appropriate for the institution's size, complexity, and fiduciary risk profile.
• The overall level of compliance with laws, regulations, and sound fiduciary principles.
• Responsiveness to recommendations from auditors and regulatory authorities.
• Strategic planning for fiduciary products and services.
• The level of experience and competence of fiduciary management and staff, including issues relating to turnover and succession planning.
• The adequacy of insurance coverage.
• The availability of competent legal counsel.
• The extent and nature of pending litigation associated with fiduciary activities, and its potential impact on earnings, capital, and the institution's reputation.
• The process for identifying and responding to fiduciary customer complaints.
Management Ratings
Rating No. 1 - indicates strong performance by management and the board of directors and strong risk management practices relative to the size, complexity and risk profile of the institution's fiduciary activities. All significant risks are consistently and effectively identified, measured, monitored, and controlled. Management and the board are proactive, and have demonstrated the ability to promptly and successfully address existing and potential problems and risks.
Rating No. 2 - indicates satisfactory management and board performance and risk management practices relative to the size, complexity and risk profile of the institution's fiduciary activities. Moderate weaknesses may exist, but are not material to the sound administration of fiduciary activities, and are being addressed. In general, significant risks and problems are effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates management and board performance that needs improvement or risk management practices that are less than satisfactory given the nature of the institution's fiduciary activities. The capabilities of management or the board of directors may be insufficient for the size, complexity, and risk profile of the institution's fiduciary activities. Problems and significant risks may be inadequately identified, measured, monitored, or controlled.
Rating No. 4 - indicates deficient management and board performance or risk management practices that are inadequate considering the size, complexity, and risk profile of the institution's fiduciary activities. The level of problems and risk exposure is excessive. Problems and significant risks are inadequately identified, measured, monitored, or controlled and require immediate action by the board and management to protect the assets of account beneficiaries and to prevent erosion of public confidence in the institution. Replacing or strengthening management or the board may be necessary.
Rating No. 5 - indicates critically deficient management and board performance or risk management practices. Management and the board of directors have not demonstrated the ability to correct problems and implement appropriate risk management practices. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the continued viability of the institution or its administration of fiduciary activities, and pose a threat to the safety of the assets of account beneficiaries. Replacing or strengthening management or the board of directors is necessary.
Operations, Internal Controls & Auditing
This rating reflects the adequacy of the institution's fiduciary operating systems and internal controls in relation to the volume and character of business conducted. Audit coverage must assure the integrity of the financial records, the sufficiency of internal controls, and the adequacy of the compliance process.
The institution's fiduciary operating systems, internal controls, and audit function subject it primarily to transaction and compliance risk. Other risks including reputation, strategic, and financial risk may also be present. The ability of management to identify, measure, monitor and control these risks is reflected in this rating. The operations, internal controls and auditing rating is based upon, but not limited to, an assessment of the following evaluation factors:
Operations and Internal Controls, including the adequacy of:
• Staff, facilities and operating systems;
• Records, accounting and data processing systems (including controls over systems access and such accounting procedures as aging, investigation and disposition of items in suspense accounts);
• Trading functions and securities lending activities;
• Vault controls and securities movement;
• Segregation of duties;
• Controls over disbursements (checks or electronic) and unissued securities;
• Controls over income processing activities;
• Reconciliation processes (depository, cash, vault, sub-custodians, suspense accounts, etc.);
• Disaster and/or business recovery programs;
• Hold-mail procedures and controls over returned mail; and,
• Investigation and proper escheatment of funds in dormant accounts.
Auditing, including:
• The independence, frequency, quality and scope of the internal and external fiduciary audit function relative to the volume, character and risk profile of the institution's fiduciary activities;
• The volume and/or severity of internal control and audit exceptions and the extent to which these issues are tracked and resolved; and
• The experience and competence of the audit staff.
Operations, Internal Controls & Auditing Ratings
Rating No. 1 - indicates that operations, internal controls, and auditing are strong in relation to the volume and character of the institution's fiduciary activities. All significant risks are consistently and effectively identified, measured, monitored, and controlled.
Rating No. 2 - indicates that operations, internal controls and auditing are satisfactory in relation to the volume and character of the institution's fiduciary activities. Moderate weaknesses may exist, but are not material. Significant risks, in general, re effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates that operations, internal controls or auditing need improvement in relation to the volume and character of the institution's fiduciary activities. One or more of these areas are less than satisfactory. Problems and significant risks may be inadequately identified, measured, monitored, or controlled.
Rating No. 4 - indicates deficient operations, internal controls or audits. One or more of these areas are inadequate or the level of problems and risk exposure is excessive in relation to the volume and character of the institution's fiduciary activities. Problems and significant risks are inadequately identified, measured, monitored, or controlled and require immediate action. Institutions with this level of deficiencies may make little provision for audits, or may evidence weak or potentially dangerous operating practices in combination with infrequent or inadequate audits.
Rating No. 5 - indicates critically deficient operations, internal controls or audits. Operating practices, with or without audits, pose a serious threat to the safety of assets of fiduciary accounts. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the ability of the institution to continue engaging in fiduciary activities.
Earnings
This rating reflects the profitability of an institution's fiduciary activities and its effect on the financial condition of the institution. The use and adequacy of budgets and earnings projections by functions, product lines and clients are reviewed and evaluated.
Risk exposure that may lead to negative earnings is also evaluated.
An evaluation of earnings is required for all institutions with fiduciary activities. An assignment of an earnings rating, however, is required only for institutions that, at the time of the examination, have total trust assets of more than $100 million, or are a non-deposit trust company (those institutions that would be required to file Schedule E of FFIEC 001).
For institutions where the assignment of an Earnings rating is not required by the UITRS, the Department of Banking has the option to assign an earnings rating using an alternate set of ratings. A rating will be assigned in accordance with implementing guidelines adopted by the supervisory agency. The definitions for the alternate ratings may be found in the section immediately following the definitions for the required ratings.
The evaluation of earnings is based upon, but not limited to, an assessment of the following factors:
• The profitability of fiduciary activities in relation to the size and scope of those activities and to the overall business of the institution.
• The overall importance to the institution of offering fiduciary services to its customers and local community.
• The effectiveness of the institution's procedures for monitoring fiduciary activity income and expense relative to the size and scope of these activities and their relative importance to the institution, including the frequency and scope of profitability reviews and planning by the institution's board of directors or a committee thereof.
• The level and consistency of profitability, or the lack thereof, generated by the institution's fiduciary activities in relation to the volume and character of the institution's business.
• Dependence upon non-recurring fees and commissions, such as fees for court accounts.
• The effects of charge-offs or compromise actions.
• Unusual features regarding the composition of business and fee schedules.
• Accounting practices that contain practices such as (1) unusual methods of allocating direct and indirect expenses and overhead, or (2) unusual methods of allocating fiduciary income and expense where two or more fiduciary institutions within the same holding company family share fiduciary services and/or processing functions.
• The extent of management's use of budgets, projections and other cost analysis procedures.
• Methods used for directors' approval of financial budgets and/or projections.
• Management's attitude toward growth and new business development.
• New business development efforts, including types of business solicited, market potential, advertising, competition, relationships with local organizations, and an evaluation by management of risk potential inherent in new business areas.
Earnings Ratings
Rating No. 1 - indicates strong earnings. The institution consistently earns a rate of return on its fiduciary activities that is commensurate with the risk of those activities. This rating would normally be supported by a history of consistent profitability over time and a judgement that future earnings prospects are favorable.
In addition, management techniques for evaluating and monitoring earnings performance are fully adequate and there is appropriate oversight by the institution's board of directors or a committee thereof. Management makes effective use of budgets and cost analysis procedures. Methods used for reporting earnings information to the board of directors, or a committee thereof, are comprehensive.
Rating No. 2 - indicates satisfactory earnings. Although the earnings record may exhibit some weaknesses, earnings performance does not pose a risk to the overall institution nor to its ability to meet its fiduciary obligations. Generally, fiduciary earnings meet management targets and appear to be at least sustainable. Management processes for evaluating and monitoring earnings are generally sufficient in relationship to the size and risk of fiduciary activities that exist, and any deficiencies can be addressed in the normal course of business. A rating of 2 may also be assigned to institutions with a history of profitable operations if there are indications that management is engaging in activities with which it is not familiar, or where there may be inordinately high levels of risk present that have not been adequately evaluated. Alternatively, an institution with otherwise strong earnings performance may also be assigned a 2 rating if there are significant deficiencies in its methods used to monitor and evaluate earnings.
Rating No. 3 - indicates less than satisfactory earnings. Earnings are not commensurate with the risk associated with the fiduciary activities undertaken. Earnings may be erratic or exhibit downward trends, and future prospects are unfavorable. This rating may also be assigned if management processes for evaluating and monitoring earnings exhibit serious deficiencies, provided the deficiencies identified do not pose an immediate danger to either the overall financial condition of the institution or its ability to meet its fiduciary obligations.
Rating No. 4 - indicates earnings that are seriously deficient. Fiduciary activities have a significant adverse effect on the overall income of the institution and its ability to generate adequate capital to support the continued operation of its fiduciary activities. The institution is characterized by fiduciary earnings performance that is poor historically, or faces the prospect of significant losses in the future. Management processes for monitoring and evaluating earnings may be poor. The board of directors has not adopted appropriate measures to address significant deficiencies.
Rating No. 5 - indicates critically deficient earnings. In general, an institution with this rating is experiencing losses from fiduciary activities that have a significant negative impact on the overall institution, representing a distinct threat to its viability through the erosion of its capital. The board of directors has not implemented effective actions to address the situation.
Alternate Rating of Earnings
Alternate ratings are assigned based on the level of implementation of four minimum standards by the board of directors and management.
These standards are:
• Standard No. 1 - The institution has reasonable methods for measuring income and expense commensurate with the volume and nature of the fiduciary services offered.
• Standard No. 2 - The level of profitability is reported to the board of directors, or a committee thereof, at least annually.
• Standard No. 3 - The board of directors periodically determines that the continued offering of fiduciary services provides an essential service to the institution's customers or to the local community.
• Standard No. 4 - The board of directors, or a committee thereof, reviews the justification for the institution to continue to offer fiduciary services even if the institution does not earn sufficient income to cover the expenses of providing those services.
Alternate Ratings
Rating No. 1 - may be assigned where an institution has implemented all four minimum standards. If fiduciary earnings are lacking, management views this as a cost of doing business as a full service institution and believes that the negative effects of not offering fiduciary services are more significant than the expense of administrating those services.
Rating No. 2 - may be assigned where an institution has implemented, at a minimum, at least three of the four standards. This rating may be assigned if the institution is not generating positive earnings or where formal earnings information may not be available.
Rating No. 3 - may be assigned if the institution has implemented at least two of the four standards. While management may have attempted to identify and quantify other revenue to be earned by offering fiduciary services, it has decided that these services should be offered as a service to customers, even if they cannot be operated profitably.
Rating No. 4 - may be assigned if the institution has implemented only one of the four standards. Management has undertaken little or no effort to identify or quantify the collateral advantages, if any, to the institution from offering fiduciary services.
Rating No. 5 - may be assigned if the institution has implemented none of the standards.
Compliance
This rating reflects an institution's overall compliance with applicable laws, regulations, accepted standards of fiduciary conduct, governing account instruments, duties associated with account administration, and internally established policies and procedures. This component specifically incorporates an assessment of a fiduciary's duty of undivided loyalty and compliance with applicable laws, regulations, and accepted standards of fiduciary conduct related to self-dealing and other conflicts of interest.
The compliance component includes reviewing and evaluating the adequacy and soundness of adopted policies, procedures, and practices generally, and as they relate to specific transactions and accounts. It also includes reviewing policies, procedures, and practices to evaluate the sensitivity of management and the board of directors to refrain from self-dealing, minimize potential conflicts of interest, and resolve actual conflict situations in favor of the fiduciary account beneficiaries.
Risks associated with account administration are potentially unlimited because each account is a separate contractual relationship that contains specific obligations. Risks associated with account administration include: failure to comply with applicable laws, regulations or terms of the governing instrument; inadequate account administration practices; and inexperienced management or inadequately trained staff. Risks associated with a fiduciary's duty of undivided loyalty generally stem from engaging in self-dealing or other conflict of interest transactions. An institution may be exposed to compliance, strategic, financial and reputation risk related to account administration and conflicts of interest activities. The ability of management to identify, measure, monitor and control these risks is reflected in this rating. Policies, procedures and practices pertaining to account administration and conflicts of interest are evaluated in light of the size and character of an institution's fiduciary business.
The compliance rating is based upon, but not limited to, an assessment of the following evaluation factors:
• Compliance with applicable federal and state statutes and regulations, including, but not limited to, federal and state fiduciary laws, the Employee Retirement Income Security Act of 1974, federal and state securities laws, state investment standards, state principal and income acts, and state probate codes;
• Compliance with the terms of governing instruments;
• The adequacy of overall policies, practices, and procedures governing compliance, considering the size, complexity, and risk profile of the institution's fiduciary activities;
• The adequacy of policies and procedures addressing account administration;
• The adequacy of policies and procedures addressing conflicts of interest, including those designed to prevent the improper use of "material inside information";
• The effectiveness of systems and controls in place to identify actual and potential conflicts of interest;
• The adequacy of securities trading policies and practices relating to the allocation of brokerage business, the payment of services with "soft dollars" and the combining, crossing, and timing of trades;
• The extent and permissibility of transactions with related parties, including, but not limited to, the volume of related commercial and fiduciary relationships and holdings of corporations in which directors, officers, or employees of the institution may be interested;
• The decision making process used to accept, review, and terminate accounts; and,
• The decision making process related to account administration duties, including cash balances, overdrafts, and discretionary distributions.
Compliance Ratings
Rating No. 1 - indicates strong compliance policies, procedures and practices. Policies and procedures covering conflicts of interest and account administration are appropriate in relation to the size and complexity of the institution's fiduciary activities. Accounts are administered in accordance with governing instruments, applicable laws and regulations, sound fiduciary principles, and internal policies and procedures. Any violations are isolated, technical in nature and easily correctable. All significant risks are consistently and effectively identified, measured, monitored and controlled.
Rating No. 2 - indicates fundamentally sound compliance policies, procedures and practices in relation to the size and complexity of the institution's fiduciary activities. Account administration may be flawed by moderate weaknesses in policies, procedures or practices. Management's practices indicate a determination to minimize the instances of conflicts of interest. Fiduciary activities are conducted in substantial compliance with laws and regulations, and any violations are generally technical in nature. Management corrects violations in a timely manner and without loss to fiduciary accounts. Significant risks are effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates compliance practices that are less than satisfactory in relation to the size and complexity of the institution's fiduciary activities. Policies, procedures and controls have not proven effective and require strengthening. Fiduciary activities may be in substantial noncompliance with laws, regulations or governing instruments, but losses are no worse than minimal. While management may have the ability to achieve compliance, the number of violations that exist, or the failure to correct prior violations, are indications that management has not devoted sufficient time and attention to its compliance responsibilities. Risk management practices generally need improvement.
Rating No. 4 - indicates an institution with deficient compliance practices in relation to the size and complexity of its fiduciary activities. Account administration is notably deficient. The institution makes little or no effort to minimize potential conflicts or refrain from self-dealing, and is confronted with a considerable number of potential or actual conflicts. Numerous substantive and technical violations of laws and regulations exist and many may remain uncorrected from previous examinations. Management has not exerted sufficient effort to effect compliance and may lack the ability to effectively administer fiduciary activities. The level of compliance problems is significant and, if left unchecked, may subject the institution to monetary losses or reputation risk. Risks are inadequately identified, measured, monitored and controlled.
Rating No. 5 - indicates critically deficient compliance practices. Account administration is critically deficient or incompetent and there is a flagrant disregard for the terms of the governing instruments and interests of account beneficiaries. The institution frequently engages in transactions that compromise its fundamental duty of undivided loyalty to account beneficiaries. There are flagrant or repeated violations of laws and regulations and significant departures from sound fiduciary principles. Management is unwilling or unable to operate within the scope of laws and regulations or within the terms of governing instruments and efforts to obtain voluntary compliance have been unsuccessful. The severity of noncompliance presents an imminent monetary threat to account beneficiaries and creates significant legal and financial exposure to the institution. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the ability of management to continue engaging in fiduciary activities.
Asset Management
This rating reflects the risks associated with managing the assets (including cash) of others. Prudent portfolio management is based on an assessment of the needs and objectives of each account or portfolio. An evaluation of asset management should consider the adequacy of processes related to the investment of all discretionary accounts and portfolios, including collective investment funds, proprietary mutual funds, and investment advisory arrangements.
The institution's asset management activities subject it to reputation, compliance and strategic risks. In addition, each individual account or portfolio managed by the institution is subject to financial risks such as market, credit, liquidity, and interest rate risk, as well as transaction and compliance risk. The ability of management to identify, measure, monitor and control these risks is reflected in this rating.
The asset management rating is based upon, but not limited to, an assessment of the following evaluation factors:
• The adequacy of overall policies, practices and procedures governing asset management, considering the size, complexity and risk profile of the institution's fiduciary activities.
• The decision-making processes used for selection, retention and preservation of discretionary assets including adequacy of documentation, committee review and approval, and a system to review and approve exceptions.
• The use of quantitative tools to measure the various financial risks in investment accounts and portfolios.
• The existence of policies and procedures addressing the use of derivatives or other complex investment products.
• The adequacy of procedures related to the purchase or retention of miscellaneous assets including real estate, notes, closely held companies, limited partnerships, mineral interests, insurance and other unique assets.
• The extent and adequacy of periodic reviews of investment performance, taking into consideration the needs and objectives of each account or portfolio.
• The monitoring of changes in the composition of fiduciary assets for trends and related risk exposure.
• The quality of investment research used in the decision-making process and documentation of the research.
• The due diligence process for evaluating investment advice received from vendors and/or brokers (including approved or focus lists of securities).
• The due diligence process for reviewing and approving brokers and/or counter parties used by the institution.
Asset Management Ratings
This rating may not be applicable for some institutions because their operations do not include activities involving the management of any discretionary assets. Functions of this type would include, but not necessarily be limited to, directed agency relationships, securities clearing, non-fiduciary custody relationships, transfer agent and registrar activities. In institutions of this type, the rating for Asset Management may be omitted by the examiner in accordance with the examining agency's implementing guidelines. However, this component should be assigned when the institution provides investment advice, even though it does not have discretion over the account assets. An example of this type of activity would be where the institution selects or recommends the menu of mutual funds offered to participant directed 401(k) plans.
Rating No. 0 - indicates an institution that does not engage in any asset management. Functions that do not require asset management may include, but are not necessarily limited to: directed agency relationships, securities clearing, non-fiduciary custody relationships, and transfer agent and registrar activities. In institutions of the type, the Asset Management rating may be 0 if:
• Operations do not include activities involving the management of any discretionary assets.
• Investment advisory services are not offered.
• There are no assets held on-site.
• There are no unique assets, such as closely-held investments, real estate, limited partnerships, or notes receivable, that require special handling such as non-standard registration or insurance protection.
• There is no discretion regarding the investment of cash balances.
• Although administering a participant-directed plan, the institution does not select or recommend the menu of funds offered to the participants.
Rating No. 1 - indicates strong asset management practices. Identified weaknesses are minor in nature. Risk exposure is modest in relation to management's abilities and the size and complexity of the assets managed.
Rating No. 2 - indicates satisfactory asset management practices. Moderate weaknesses are present and are well within management's ability and willingness to correct. Risk exposure is commensurate with management's abilities and the size and complexity of the assets managed. Supervisory response is limited.
Rating No. 3 - indicates that asset management practices are less than satisfactory in relation to the size and complexity of the assets managed. Weaknesses may range from moderate to severe; however, they are not of such significance as to generally pose a threat to the interests of account beneficiaries. Asset management and risk management practices generally need to be improved. An elevated level of supervision is normally required.
Rating No. 4 - indicates deficient asset management practices in relation to the size and complexity of the assets managed. The levels of risk are significant and inadequately controlled. The problems pose a threat to account beneficiaries generally, and if left unchecked, may subject the institution to losses and could undermine the reputation of the institution.
Rating No. 5 - represents critically deficient asset management practices and a flagrant disregard of fiduciary duties. These practices jeopardize the interests of account beneficiaries, subject the institution to losses, and may pose a threat to the soundness of the institution.
UNIFORM INTERAGENCY RATING SYSTEM
FOR INFORMATION TECHNOLOGY
INTRODUCTION
The quality, reliability, and integrity of a financial institution or service provider's information technology (IT) affects all aspects of its performance. An assessment of the technology risk management framework is necessary whether or not the institution or a third-party service provider manages these operations. The Uniform Rating System for Information Technology (URSIT) is an internal rating system used by federal and state regulators to uniformly assess financial institution and service provider risks introduced by IT. It also allows the regulators to identify those insured institutions and service providers whose information technology risk exposure or performance requires special supervisory attention.
The rating system includes component and composite rating descriptions and the explicit identification of risks and assessment factors that examiners consider in assigning component ratings. Additionally, information technology can affect the risks associated with financial institutions. The effect on credit, operational, market, reputation, strategic, liquidity, interest rate, and compliance risks should be considered for each IT rating component.
The primary purpose of the rating system is to identify those entities whose condition or performance of information technology functions requires special supervisory attention. This rating system assists examiners in making an assessment of risk and compiling examination findings. However, the rating system does not drive the scope of an examination. Examiners should use the rating system to help evaluate the entity's overall risk exposure and risk management performance, and determine the degree of supervisory attention believed necessary to ensure that weaknesses are addressed and that risk is properly managed.
OVERVIEW
The URSIT is based on a risk evaluation of four critical components: Audit, Management, Development and Acquisition, and Support and Delivery (AMDS). These components are used to assess the overall performance of IT within an organization. Examiners evaluate the functions identified within each component to assess the institution's ability to identify, measure, monitor and control information technology risks. Each organization examined for IT is assigned a summary or composite rating based on the overall results of the evaluation. The IT composite rating and each component rating are based on a scale of "1" through "5" in ascending order of supervisory concern; "1" representing the highest rating and least degree of concern, and "5" representing the lowest rating and highest degree of concern.
The first step in developing an IT composite rating for an organization is the assignment of a performance rating to the individual AMDS components. The evaluation of each of these components, their interrelationships, and relative importance is the basis for the composite rating. The composite rating is derived by making a qualitative summarization of all of the AMDS components. A direct relationship exists between the composite rating and the individual AMDS component performance ratings. However, the composite rating is not an arithmetic average of the individual components. An arithmetic approach does not reflect the actual condition of IT when using a risk-focused approach. A poor rating in one component may heavily influence the overall composite rating for an institution. For example, if the audit function is viewed as inadequate, the overall integrity of the IT systems is not readily verifiable. Thus, a composite rating of less than satisfactory ("3"-"5") would normally be appropriate.
A principal purpose of the composite rating is to identify those financial institutions and service providers that pose an inordinate amount of information technology risk and merit special supervisory attention. Thus, individual risk exposures that more explicitly affect the viability of the organization and/or its customers should be given more weight in the composite rating.
The FFIEC recognizes that management practices, particularly as they relate to risk management, vary considerably among financial institutions and service bureaus depending on their size and sophistication, the nature and complexity of their business activities and their risk profile. Accordingly, the FFIEC also recognizes that for less complex information systems environments, detailed or highly formalized systems and controls are not required to receive the higher composite and component ratings.
The following two sections contain the URSIT composite rating definitions, the assessment factors, and definitions for the four component ratings. These assessment factors and definitions outline various IT functions and controls that may be evaluated as part of the examination.
COMPOSITE RATINGS
Composite 1
Financial institutions and service providers rated composite "1" exhibit strong performance in every respect and generally have components rated 1 or 2. Weaknesses in IT are minor in nature and are easily corrected during the normal course of business. Risk management processes provide a comprehensive program to identify and monitor risk relative to the size, complexity and risk profile of the entity. Strategic plans are well defined and fully integrated throughout the organization. This allows management to quickly adapt to changing market, business and technology needs of the entity. Management identifies weaknesses promptly and takes appropriate corrective action to resolve audit and regulatory concerns. The financial condition of the service provider is strong and overall performance shows no cause for supervisory concern.
The descriptive examples in the numeric composite rating definitions are intended to provide guidance to examiners as they evaluate the overall condition of Information Technology. Examiners must use professional judgement when making this assessment and assigning the numeric rating.
Composite 2
Financial institutions and service providers rated composite "2" exhibit safe and sound performance but may demonstrate modest weaknesses in operating performance, monitoring, management processes or system development. Generally, senior management corrects weaknesses in the normal course of business. Risk management processes adequately identify and monitor risk relative to the size, complexity and risk profile of the entity. Strategic plans are defined but may require clarification, better coordination or improved communication throughout the organization. As a result, management anticipates, but responds less quickly to changes in market, business, and technological needs of the entity. Management normally identifies weaknesses and takes appropriate corrective action. However, greater reliance is placed on audit and regulatory intervention to identify and resolve concerns. The financial condition of the service provider is acceptable and while internal control weaknesses may exist, there are no significant supervisory concerns. As a result, supervisory action is informal and limited.
Composite 3
Financial institutions and service providers rated composite "3" exhibit some degree of supervisory concern due to a combination of weaknesses that may range from moderate to severe. If weaknesses persist, further deterioration in the condition and performance of the institution or service provider is likely. Risk management processes may not effectively identify risks and may not be appropriate for the size, complexity, or risk profile of the entity. Strategic plans are vaguely defined and may not provide adequate direction for IT initiatives. As a result, management often has difficulty responding to changes in business, market, and technological needs of the entity. Self-assessment practices are weak and are generally reactive to audit and regulatory exceptions. Repeat concerns may exist, indicating that management may lack the ability or willingness to resolve concerns. The financial condition of the service provider may be weak and/or negative trends may be evident. While financial or operational failure is unlikely, increased supervision is necessary. Formal or informal supervisory action may be necessary to secure corrective action.
Composite 4
Financial institutions and service providers rated composite "4" operate in an unsafe and unsound environment that may impair the future viability of the entity. Operating weaknesses are indicative of serious managerial deficiencies. Risk management processes inadequately identify and monitor risk, and practices are not appropriate given the size, complexity, and risk profile of the entity. Strategic plans are poorly defined and not coordinated or communicated throughout the organization. As a result, management and the board are not committed to, or may be incapable of ensuring that technological needs are met. Management does not perform self-assessments and demonstrates an inability or unwillingness to correct audit and regulatory concerns. The financial condition of the service provider is severely impaired and/or deteriorating. Failure of the financial institution or service provider may be likely unless IT problems are remedied. Close supervisory attention is necessary and, in most cases, formal enforcement action is warranted.
Composite 5
Financial institutions and service providers rated composite "5" exhibit critically deficient operating performance and are in need of immediate remedial action. Operational problems and serious weaknesses may exist throughout the organization. Risk management processes are severely deficient and provide management little or no perception of risk relative to the size, complexity, and risk profile of the entity. Strategic plans do not exist or are ineffective, and management and the board provide little or no direction for IT initiatives. As a result, management is unaware of, or inattentive to technological needs of the entity. Management is unwilling or incapable of correcting audit and regulatory concerns. The financial condition of the service provider is poor and failure is highly probable due to poor operating performance or financial instability. Ongoing supervisory attention is necessary.
COMPONENT RATINGS
Audit
Financial institutions and service providers are expected to provide independent assessments of their exposure to risks and the quality of internal controls associated with the acquisition, implementation and use of information technology. Audit practices should address the IT risk exposures throughout the institution and its service provider(s) in the areas of user and data center operations, client/server architecture, local and wide area networks, telecommunications, information security, electronic data interchange, systems development, and contingency planning. This rating should reflect the adequacy of the organization's overall IT audit program, including the internal and external auditor's abilities to detect and report significant risks to management and the board of directors on a timely basis. It should also reflect the internal and external auditor's capability to promote a safe, sound, and effective operation.
The descriptive examples in the numeric component rating definitions are intended to provide guidance to examiners as they evaluate the individual components. Examiners must use professional judgement when assessing a component area and assigning a numeric rating value as it is likely that examiners will encounter conditions that correspond to descriptive examples in two or more numeric rating value definitions.
Financial institutions that outsource their data processing operations should obtain copies of internal audit reports, SAS 70 reviews, and/or regulatory examination reports of their service providers.
The performance of audit is rated based upon an assessment of factors such as:
• The level of independence maintained by audit and the quality of the oversight and support provided by the board of directors and management.
• The adequacy of audit's risk analysis methodology used to prioritize the allocation of audit resources and to formulate the audit schedule.
• The scope, frequency, accuracy, and timeliness of internal and external audit reports.
• The extent of audit participation in application development, acquisition, and testing, to ensure the effectiveness of internal controls and audit trails.
• The adequacy of the overall audit plan in providing appropriate coverage of IT risks.
• The auditor's adherence to codes of ethics and professional audit standards.
• The qualifications of the auditor, staff succession, and continued development through training.
• The existence of timely and formal follow-up and reporting on management's resolution of identified problems or weaknesses.
• The quality and effectiveness of internal and external audit activity as it relates to IT controls.
Audit Ratings
Rating No. 1 - indicates strong audit performance. Audit independently identifies and reports weaknesses and risks to the board of directors or its audit committee in a thorough and timely manner. Outstanding audit issues are monitored until resolved. Risk analysis ensures that audit plans address all significant IT operations, procurement, and development activities with appropriate scope and frequency. Audit work is performed in accordance with professional auditing standards and report content is timely, constructive, accurate, and complete. Because audit is strong, examiners may place substantial reliance on audit results.
Rating No. 2 - indicates satisfactory audit performance. Audit independently identifies and reports weaknesses and risks to the board of directors or audit committee, but reports may be less timely. Significant outstanding audit issues are monitored until resolved. Risk analysis ensures that audit plans address all significant IT operations, procurement, and development activities; however, minor concerns may be noted with the scope or frequency. Audit work is performed in accordance with professional auditing standards; however, minor or infrequent problems may arise with the timeliness, completeness and accuracy of reports. Because audit is satisfactory, examiners may rely on audit results but because minor concerns exist, examiners may need to expand verification procedures in certain situations.
Rating No. 3 - indicates less than satisfactory audit performance. Audit identifies and reports weaknesses and risks; however, independence may be compromised and reports presented to the board or audit committee may be less than satisfactory in content and timeliness. Outstanding audit issues may not be adequately monitored. Risk analysis is less than satisfactory. As a result, the audit plan may not provide sufficient audit scope or frequency for IT operations, procurement, and development activities. Audit work is generally performed in accordance with professional auditing standards; however, occasional problems may be noted with the timeliness, completeness and/or accuracy of reports. Because audit is less than satisfactory, examiners must use caution if they rely on the audit results.
Rating No. 4 - indicates deficient audit performance. Audit may identify weaknesses and risks but it may not independently report to the board or audit committee and report content may be inadequate. Outstanding audit issues may not be adequately monitored and resolved. Risk analysis is deficient. As a result, the audit plan does not provide adequate audit scope or frequency for IT operations, procurement, and development activities. Audit work is often inconsistent with professional auditing standards and the timeliness, accuracy, and completeness of reports is unacceptable. Because audit is deficient, examiners cannot rely on audit results.
Rating No. 5 - indicates critically deficient audit performance. If an audit function exists, it lacks sufficient independence and, as a result, does not identify and report weaknesses or risks to the board or audit committee. Outstanding audit issues are not tracked and no follow-up is performed to monitor their resolution. Risk analysis is critically deficient. As a result, the audit plan is ineffective and provides inappropriate audit scope and frequency for IT operations, procurement and development activities. Audit work is not performed in accordance with professional auditing standards and major deficiencies are noted regarding the timeliness, accuracy, and completeness of audit reports. Because audit is critically deficient examiners cannot rely on audit results.
Management
This rating reflects the abilities of the board and management as they apply to all aspects of IT acquisition, development, and operations. Management practices may need to address some or all of the following IT-related risks: strategic planning, quality assurance, project management, risk assessment, infrastructure and architecture, end-user computing, contract administration of third party service providers, organization and human resources, regulatory and legal compliance. Generally, directors need not be actively involved in day-to-day operations; however, they must provide clear guidance regarding acceptable risk exposure levels and ensure that appropriate policies, procedures, and practices have been established. Sound management practices are demonstrated through active oversight by the board of directors and management, competent personnel, sound IT plans, adequate policies and standards, an effective control environment, and risk monitoring. This rating should reflect the board's and management's ability as it applies to all aspects of IT operations.
The performance of management and the quality of risk management are rated based upon an assessment of factors such as:
• The level and quality of oversight and support of the IT activities by the board of directors and management.
• The ability of management to plan for and initiate new activities or products in response to information needs and to address risks that may arise from changing business conditions.
• The ability of management to provide information reports necessary for informed planning and decision making in an effective and efficient manner.
• The adequacy of, and conformance with, internal policies and controls addressing the IT operations and risks of significant business activities.
• The effectiveness of risk monitoring systems.
• The timeliness of corrective action for reported and known problems.
• The level of awareness of and compliance with laws and regulations.
• The level of planning for management succession.
• The ability of management to monitor the services delivered and to measure the organization's progress toward identified goals in an effective and efficient manner.
• The adequacy of contracts and management's ability to monitor relationships with third-party servicers.
• The adequacy of strategic planning and risk management practices to identify, measure, monitor, and control risks, including management's ability to perform self-assessments.
• The ability of management to identify, measure, monitor, and control risks and to address emerging information technology needs and solutions.
In addition to the above, factors such as the following are included in the assessment of management at service providers:
• The financial condition and ongoing viability of the entity.
• The impact of external and internal trends and other factors on the ability of the entity to support continued servicing of client financial institutions.
• The propriety of contractual terms and plans.
Management Ratings
Rating No. 1 - indicates strong performance by management and the board. Effective risk management practices are in place to guide IT activities, and risks are consistently and effectively identified, measured, controlled, and monitored. Management immediately resolves audit and regulatory concerns to ensure sound operations. Written technology plans, policies and procedures, and standards are thorough and properly reflect the complexity of the IT environment. They have been formally adopted, communicated, and enforced throughout the organization. IT systems provide accurate, timely reports to management. These reports serve as the basis of major decisions and as an effective performance-monitoring tool. Outsourcing arrangements are based on comprehensive planning; routine management supervision sustains an appropriate level of control over vendor contracts, performance, and services provided. Management and the board have demonstrated the ability to promptly and successfully address existing IT problems and potential risks.
Rating No. 2 - indicates satisfactory performance by management and the board. Adequate risk management practices are in place and guide IT activities. Significant IT risks are identified, measured, monitored, and controlled; however, risk management processes may be less structured or inconsistently applied and modest weaknesses exist. Management routinely resolves audit and regulatory concerns to ensure effective and sound operations, however, corrective actions may not always be implemented in a timely manner. Technology plans, policies and procedures, and standards are adequate and are formally adopted. However, minor weaknesses may exist in management's ability to communicate and enforce them throughout the organization. IT systems provide quality reports to management which serve as a basis for major decisions and a tool for performance planning and monitoring. Isolated or temporary problems with timeliness, accuracy or consistency of reports may exist. Outsourcing arrangements are adequately planned and controlled by management, and provide for a general understanding of vendor contracts, performance standards and services provided. Management and the board have demonstrated the ability to address existing IT problems and risks successfully.
Rating No. 3 - indicates less than satisfactory performance by management and the board. Risk management practices may be weak and offer limited guidance for IT activities. Most IT risks are generally identified; however, processes to measure and monitor risk may be flawed. As a result, management's ability to control risk is less than satisfactory. Regulatory and audit concerns may be addressed, but time frames are often excessive and the corrective action taken may be inappropriate. Management may be unwilling or incapable of addressing deficiencies. Technology plans, policies and procedures, and standards exist, but may be incomplete. They may not be formally adopted, effectively communicated, or enforced throughout the organization. IT systems provide requested reports to management, but periodic problems with accuracy, consistency and timeliness lessen the reliability and usefulness of reports and may adversely affect decision making and performance monitoring. Outsourcing arrangements may be entered into without thorough planning. Management may provide only cursory supervision that limits their understanding of vendor contracts, performance standards, and services provided. Management and the board may not be capable of addressing existing IT problems and risks, evidenced by untimely corrective actions for outstanding IT problems.
Rating No. 4 - indicates deficient performance by management and the board. Risk management practices are inadequate and do not provide sufficient guidance for IT activities. Critical IT risk are not properly identified, and processes to measure and monitor risks are deficient. As a result, management may not be aware of and is unable to control risks. Management may be unwilling and/or incapable of addressing audit and regulatory deficiencies in an effective and timely manner. Technology plans, policies and procedures, and standards are inadequate, have not been formally adopted, or effectively communicated throughout the organization, and management does not effectively enforce them. IT systems do not routinely provide management with accurate, consistent, and reliable reports, thus contributing to ineffective performance monitoring and/or flawed decision making. Outstanding arrangements may be entered into without planning or analysis, and management may provide little or no supervision of vendor contracts, performance standards, or services provided. Management and the board are unable to address existing IT problems and risks, as evidenced by ineffective actions and longstanding IT weaknesses. Strengthening of management and its processes is necessary. The financial condition of the service provider may threaten its viability.
Rating No. 5 - indicates critically deficient performance by management and the board. Risk management practices are severely flawed and provide inadequate guidance for IT activities. Critical IT risks are not identified, and processes to measure and monitor risks do not exist, or are not effective. Management's inability to control risk may threaten the continued viability of the institution or service provider. Management is unable and/or unwilling to correct audit and regulatory identified deficiencies and immediate action by the board is required to preserve the viability of the institution or service provider. If they exist, technology plans, policies and procedures, and standards are critically deficient. Because of systemic problems, IT systems do not produce management reports which are accurate, timely, or relevant. Outsourcing arrangements may have been entered into without management planning or analysis, resulting in significant losses to the financial institution or ineffective vendor services. The financial condition of the service provider presents an imminent threat to its viability.
Development and Acquisition
This rating reflects an organization's ability to identify, acquire, install, and maintain appropriate information technology solutions. Management practices may need to address all or parts of the business process for implementing any kind of change to the hardware or software used. These business processes include an institution's or service provider's purchase of hardware or software, development and programming performed by the institution or service provider, purchase of services from independent vendors or affiliated data centers, or a combination of these activities. The business process is defined as all phases taken to implement a change including researching alternatives available, choosing an appropriate option for the organization as a whole, and converting to the new system, or integrating the new system with existing systems. This rating reflects the adequacy of the institution's systems development methodology and related risk management practices for acquisition and deployment of information technology. This rating also reflects the boards and management's ability to enhance and replace information technology prudently in a controlled environment,
The performance of systems development and acquisition and related risk management practice is rated based upon an assessment of factors such as:
• The level and quality of oversight and support of systems development and acquisition activities by senior management and the board of directors.
• The adequacy of the organizational and management structures to establish accountability and responsibility for IT systems and technology initiatives.
• The volume, nature, and extent of risk exposure to the financial institution in the area of systems development and acquisition.
• The adequacy of the institution's Systems Development Life Cycle (SDLC) and programming standards.
• The quality of project management programs and practices which are followed by developers, operators, executive management/owners, independent vendors or affiliated servicers, and end-users.
• The independence of the quality assurance function and the adequacy of controls over program changes.
• The quality and thoroughness of system documentation.
• The integrity and security of the network, system, and application software.
• The development of information technology solutions that meet the needs of end users.
• The extent of end user involvement in the system development process.
In addition to the above, factors such as the following are included in the assessment of development and acquisition at service providers:
• The quality of software releases and documentation.
• The adequacy of training provided to clients.
Development and Acquisition Ratings
Rating No. 1 - indicates strong systems development, acquisition, implementation, and change management performance. Management and the board routinely demonstrate successfully the ability to identify and implement appropriate IT solutions while effectively managing risk. Project management techniques and the SDLC are fully effective and supported by written policies, procedures and project controls that consistently result in timely and efficient project completion. An independent quality assurance function provides strong controls over testing and program change management. Technology solutions consistently meet end user needs. No significant weaknesses or problems exist.
Rating No. 2 - indicates satisfactory systems development, acquisition, implementation, and change management performance. Management and the board frequently demonstrate the ability to identify and implement appropriate IT solutions while managing risk. Project management and the SDLC are generally effective; however, weaknesses may exist that result in minor project delays or cost overruns. An independent quality assurance function provides adequate supervision of testing and program change management, but minor weaknesses may exist. Technology solutions meet end user needs. However, minor enhancements may be necessary to meet original user expectations. Weaknesses may exist; however, they are not significant and they are easily corrected in the normal course of business.
Rating No. 3 - indicates less than satisfactory systems development, acquisition, implementation, and change management performance. Management and the board may often be unsuccessful in identifying and implementing appropriate IT solutions; therefore, unwarranted risk exposure may exist. Project management techniques and the SDLC are weak and may result in frequent project delays, backlogs or significant cost overruns. The quality assurance function may not be independent of the programming function which may adversely impact the integrity of testing and program change management. Technology solutions generally meet end user needs, but often require an inordinate level of change after implementation. Because of weaknesses, significant problems may arise that could result in disruption to operations or significant losses.
Rating No. 4 - indicates deficient systems development, acquisition, implementation, and change management performance. Management and the board may be unable to identify and implement appropriate IT solutions and do not effectively mange risk. Project management techniques and the SDLC are ineffective and may result in severe project delays and cost overruns. The quality assurance function is not fully effective and may not provide independent or comprehensive review of testing controls or program change management. Technology solutions may not meet the critical needs of the organization. Problems and significant risks exist that require immediate action by the board and management to preserve the soundness of the institution.
Rating No. 5 - indicates critically deficient systems development, acquisition, implementation, and change management performance. Management and the board appear to be incapable of identifying, and implementing appropriate information technology solutions. If they exist, project management techniques and the SDLC are critically deficient and provide little or no direction for development of systems or technology projects. The quality assurance function is severely deficient or not present and unidentified problems in testing and program change management have caused significant IT risks. Technology solutions do not meet the needs of the organization. Serious problems and significant risks exist which raise concern for the financial institution's or service providers' ongoing viability.
Support and Delivery
This rating reflects an organization's ability to provide technology services in a secure environment. It reflects not only the condition of IT operations but also factors such as reliability, security, and integrity, which may affect the quality of the information delivery system. The factors include customer support and training, and the ability to manage problems and incidents, operations, system performance, capacity planning, and facility and data management. Risk management practices should promote effective, safe and sound IT operations that ensure the continuity of operations and the reliability and availability of data. The scope of this component rating includes operational risks throughout the organization and service providers.
The rating of IT support and delivery is based on a review and assessment of requirements such as:
• The ability to provide a level of service that meets the requirements of the business.
• The adequacy of security policies, procedures, and practices in all units and at all levels of the financial institution and service providers.
• The adequacy of data controls over preparation, input, processing, and output.
• The adequacy of corporate contingency planning and business resumption for data centers, networks, service providers and business units.
• The quality of processes or programs that monitor capacity and performance.
• The adequacy of controls and the ability to monitor controls at service providers.
• The quality of assistance provided to users, including the ability to handle problems.
• The adequacy of operating policies, procedures, and manuals.
• The quality of physical and logical security, including the privacy of data.
• The adequacy of firewall architectures and the security of connections with public networks.
In addition to the above, factors such as the following are included in the assessment of support and delivery at service providers:
• The adequacy of customer service provided to clients.
• The ability of the entity to provide and maintain service level performance that meets the requirements of the client.
Support and Delivery Ratings
Rating No. 1 - indicates strong IT support and delivery performance. The organization provides technology services that are reliable and consistent. Service levels adhere to well-defined service level agreements and routinely meet or exceed business requirements. A comprehensive corporate contingency and business resumption plan is in place. Annual contingency plan testing and updating is performed; and, critical systems and applications are recovered within acceptable time frames. A formal written data security policy and awareness program is communicated and enforced throughout the organization. The logical and physical security for all IT platforms is closely monitored and security incidents and weaknesses are identified and quickly corrected. Relationships with third-party service providers are closely monitored. IT operations are highly reliable, and risk exposure is successfully identified and controlled.
Rating No. 2 - indicates satisfactory IT support and delivery performance. The organization provides technology services that are generally reliable and consistent, however, minor discrepancies in service levels may occur. Service performance adheres to service agreements and meets business requirements. A corporate contingency and business resumption plan is in place, but minor enhancements may be necessary. Annual plan testing and updating is performed and minor problems may occur when recovering systems or applications. A written data security policy is in place but may require improvement to ensure its adequacy. The policy is generally enforced and communicated throughout the organization, e.g. via a security awareness program. The logical and physical security for critical IT platforms is satisfactory. Systems are monitored, and security incidents and weaknesses are identified and resolved within reasonable time frames. Relationships with third-party service providers are monitored. Critical IT operations are reliable and risk exposure is reasonably identified and controlled.
Rating No. 3 - indicates that the performance of IT support and delivery is less than satisfactory and needs improvement. The organization provides technology services that may not be reliable or consistent. As a result, service levels periodically do not adhere to service level agreements or meet business requirements. A corporate contingency and business resumption plan is in place but may not be considered comprehensive. The plan is periodically tested; however, the recovery of critical systems and applications is frequently unsuccessful. A data security policy exists; however, it may not be strictly enforced or communicated throughout the organization. The logical and physical security for critical IT platforms is less than satisfactory. Systems are monitored; however, security incidents and weaknesses may not be resolved in a timely manner. Relationships with third-party service providers may not be adequately monitored. IT operations are not acceptable and unwarranted risk exposures exist. If not corrected, weaknesses could cause performance degradation or disruption to operations.
Rating No. 4 - indicates deficient IT support and delivery performance. The organization provides technology services that are unreliable and inconsistent. Service level agreements are poorly defined and service performance usually fails to meet business requirements. A corporate contingency and business resumption plan may exist, but its content is critically deficient. If contingency testing is performed, management is typically unable to recover critical systems and applications. A data security policy may not exist. As a result, serious supervisory concerns over security and the integrity of data exist. The logical and physical security for critical IT platforms is deficient. Systems may be monitored, but security incidents and weaknesses are not successfully identified or resolved. Relationships with third-party service providers are not monitored. IT operations are not reliable and significant risk exposure exists. Degradation in performance is evident and frequent disruption in operations has occurred.
Rating No. 5 - indicates critically deficient IT support and delivery performance. The organization provides technology services that are not reliable or consistent. Service level agreements do not exist and service performance does not meet business requirements. A corporate contingency and business resumption plan does not exist. Contingency testing is not performed and management has not demonstrated the ability to recover critical systems and applications. A data security policy does not exist, and a serious threat to the organization's security and data integrity exists. The logical and physical security for critical IT platforms is inadequate, and management does not monitor systems for security incidents and weaknesses. Relationships with third-party service providers are not monitored, and the viability of a service provider may be in jeopardy. IT operations are severely deficient, and the seriousness of weaknesses could cause failure of the financial institution or service provider if not addressed.
RATING SYSTEM FOR U.S. BRANCHES AND AGENCIES
OF FOREIGN BANKING ORGANIZATIONS
The rating system for U.S. branches and agencies1 of foreign banking organizations (FBOs) is a management information and supervisory tool designed to assess the condition of a branch and to identify significant supervisory concerns at a branch in a systematic and consistent fashion. The rating system (ROCA) has been revised from the previous rating system of asset quality, internal controls, and management (AIM) to better assess the condition of a branch within the context of the FBO, of which it is an integral part, and to pinpoint the key areas of concern in a branch office.
For evaluation purposes, the rating system divides a branch's overall activities into three individual components: risk management, operational controls, and compliance. These components represent the major activities or processes of the branch that may raise supervisory concern. The rating system also provides for a specific rating of the quality of the branch's stock of assets as of the examination date.
COMPOSITE RATING
The overall or composite rating indicates whether, in the aggregate, the operations of the branch may present supervisory concerns and the extent of any concerns. While the individual component ratings will be taken into consideration in arriving at the branch's overall assessment, the composite rating should not be considered merely an arithmetic average of the individual components. The examiner should assign and justify in the report a composite rating using definitions provided below as a guide.2 The composite rating is based on a scale of one through five in ascending order of supervisory concern. Thus, one represents the lowest level of supervisory concern while five represents the highest level. The five composite ratings are defined as follows.
Composite Rating 1
Branches in this group are strong in every respect. These branches require only normal supervisory attention.
Composite Rating 2
Branches in this group are in satisfactory condition, but may have modest weaknesses that can be corrected by branch management in the normal course of business. Generally, they do not require additional or more than normal supervisory attention.
Composite Rating 3
Branches in this group are viewed as fair due to a combination of weaknesses in risk management, operational controls, and compliance, or asset quality problems that in combination with the condition of the FBO or other factors, cause supervisory concern. In addition, branch and/or head office management may not be taking the necessary corrective actions to address substantive weaknesses. This rating may also be assigned when risk management, operational controls, or compliance is individually viewed as unsatisfactory. Generally, these branches raise supervisory concern and require more than normal supervisory attention to address their weaknesses.
Composite Rating 4
Branches in this group are in marginal condition due to serious weaknesses as reflected in the assessments of the individual components. Serious problems or unsafe and unsound banking practices or operations exist, which have not been satisfactorily addressed or resolved by branch and/or head office management. Branches in this category require close supervisory attention and surveillance monitoring and a definitive plan for corrective action by branch and head office management.
It also should be recognized that different offices of the FBO can be assigned widely different roles in the FBO's overall strategy. Thus, an individual office that books very few loans, but is otherwise poorly managed, should not be given undue credit for having good asset quality. Alternatively, a branch that is designated to hold problem assets generated by other offices of the FBO, in order to better manage the workout process, should not be penalized, so long as the FBO has the ability to support the level of problem assets.
Finally, it should be recognized that asset quality tends to be a "trailing" indicator of branch performance. In instances where risk management systems are weak, but problem assets are currently nominal, it is realistic to assume there will be future deterioration in asset quality. By the same measure, management should be given credit in the overall evaluation where the causes of past asset quality problems have been corrected.
Composite Rating 5
Branches in this group are in unsatisfactory condition due to a high level of severe weaknesses or unsafe and unsound conditions, and consequently require urgent restructuring of operations by branch and head office management.
DISCLOSURE
Following approval of the rating by appropriate senior supervisory officials at the examining agency, the composite numeric rating should be disclosed in the open, summary section of the examination report. In disclosing the rating, its meaning should be explained clearly using the appropriate composite rating definition. The report should also make it clear that the rating is part of the overall findings of the examination and is thus confidential. Any composite rating disclosed or discussed at an examination closeout meeting should be held out by the examiner-in-charge to be tentative.
COMPONENT EVALUATIONS
Similar to the composite rating, the individual rating components are evaluated on a scale of one to five, where one represents the lowest level of supervisory concern and five represents the highest. Each component is discussed below followed by a description of the individual performance ratings.
Risk Management
Risk is an inevitable component of any financial institution. Risk management, or the process of identifying, measuring, and controlling risk, is therefore an important responsibility of any financial institution. In a branch, which is typically removed from its head office by location and time zone, an effective risk management system is critical not only to manage the scope of its activities but to achieve comprehensive, ongoing oversight by branch and head office management. In the examination process, examiners will therefore determine the extent to which risk management techniques are adequate (i) to control risk exposures that result from the branch's activities and (ii) to ensure adequate oversight by branch and head office management and thereby promote a safe and sound banking environment.
The primary components of a sound risk management system are a comprehensive risk assessment approach; a detailed structure of limits, guidelines, and other parameters used to govern risk taking; and a strong management information system for monitoring and reporting risks.
The process of risk assessment includes the identification of all the risks associated with the branch's balance sheet and off-balance-sheet activities and grouping them into appropriate risk categories. These categories broadly relate to credit, market, liquidity, operational, and legal risks.3 All major risks should be measured explicitly and consistently by branch management; risks should also be reevaluated on an ongoing basis as underlying risk assumptions relating to economic and market conditions vary and as the branch's activities change. The branch's expansion into new products or business lines should not outpace proper risk management or supervision by head office.Where risks cannot be explicitly measured, management should demonstrate knowledge of their potential impact and a sense of how to manage such risks.
Risk identification and measurement are followed by an evaluation of the tradeoff between risks and returns to establish acceptable risk exposure levels, which are stated primarily in the branch's lending and trading policies subject to the approval of head office management. These policies should give standards for evaluating and undertaking risk exposure in individual branch activities as well as procedures for tracking and reporting risk exposure to monitor compliance with established policy limits or guidelines.
Head office management has a role in developing and approving the branch's risk management system as part of its responsibility to provide a comprehensive system of oversight for the branch. Generally, the branch's risk management system, including risk identification, measurement, limits or guidelines, and monitoring should be modeled on that of the FBO as a whole to provide for a fully-integrated institution-wide risk management system.4
In assigning the risk management rating, examiners should evaluate the current, ongoing situation and concentrate on developments since the previous examination. The rating should not concentrate on past problems, such as those relating to the current quality of the branch's stock of assets, if risk management techniques have improved significantly since those problems developed.5
More specifically, in rating the branch's risk management procedures, examiners should consider the following:
• The extent to which the branch is able to manage the risks inherent in its lending, trading, and other activities, specifically its ability to identify, measure, and control these risks.
• The soundness of the qualitative and quantitative assumptions implicit in the risk management system.
• Whether risk policies, guidelines, and limits at the branch are consistent with its lending, trading, and other activities; management's experience level; and the overall financial strength of the branch and/or the FBO.
• Whether the management information system and other forms of communication are consistent with the level of business activity at the branch and sufficient to accurately monitor risk exposure, compliance with established limits, and sufficient to enable the head office to monitor the real performance and risks of the branch.
• Management's ability to recognize and accommodate new risks that may arise from the changing environment, and to identify and address risks not readily quantified in a risk management system.
For example, in the lending area, a branch would be expected to have (1) experienced lending officers, an effective credit approval and review function, and, where appropriate, credit work-out personnel; (2) a credit risk evaluation system that was viewed as adequate in assessing relative credit risks; (3) branch officer lending limits, lending guidelines, and portfolio policies consistent with the abilities of branch personnel and the financial expertise and resources of the FBO; (4) a system that identified existing and potential problem credits, a method for assessing the likely impact of those credits on existing and future profits, and procedures for accurately informing head office of the credit quality of the portfolio and possible credit losses; and (5) procedures for assessing the impact on the portfolio of specific or general changes in the business climate.
Risk Management Ratings
A rating of 1 indicates that management has a fully-integrated risk management system that effectively identifies and controls all major types of risk at the branch, including those from new products and the changing environment. This assessment, in most cases, will be supported by a superior level of financial performance and asset quality at the branch. No supervisory concerns are evident.
A rating of 2 indicates that the risk management system is fully effective with respect to almost all major risk factors. It reflects a responsiveness and ability to cope successfully with existing and foreseeable exposures that may arise in carrying out the branch's business plan. While the branch may have residual risk-related weaknesses, these problems have been recognized and are being addressed by the branch and/or head office. Any such weaknesses will not have a material adverse affect on the branch. Generally, risks are being controlled in a manner that does not require additional or more than normal supervisory attention.
A rating of 3 signifies a risk management system that is lacking in some important measures. Its effectiveness in dealing with the branch's level of risk exposures is cause for more than normal supervisory attention, and deterioration in financial performance indicators is probable. Current risk-related procedures are considered fair, existing problems are not being satisfactorily addressed, or risks are not being adequately identified and controlled. While these deficiencies may not have caused significant problems yet, there are clear indications that the branch is vulnerable to risk-related deterioration.
A rating of 4 represents a marginal risk management system that generally fails to identify and control significant risk exposures in many important respects. Generally, such a situation reflects a lack of adequate guidance and supervision by head office management. As a result, deterioration in overall performance is imminent or is already evident in the branch's overall performance since the previous examination. Failure of management to correct risk management deficiencies that have created significant problems in the past warrants close supervisory attention.
A branch rated 5 has critical performance problems that are due to the absence of an effective risk management system in almost every respect. Not only are there a large volume of problem risk exposures, the problems are also intensifying. Management has not demonstrated the capability to stabilize the branch's situation. If corrective actions are not taken immediately, the operations of the branch are severely endangered.
Operational Controls
This component assesses the effectiveness of the branch's operational controls, including accounting and financial controls. The assessment is based on the expectation that branches should have an independent internal audit function and/or an adequate system of head office or external audits as well as a system of internal controls consistent with the size and complexity of their operations. In this regard, internal audit and control procedures should ensure that operations are conducted in accordance with internal guidelines and regulatory policies and that all reports and analysis provided to the head office and branch senior management are timely and accurate. This aspect of supervision in the context of branches is intended to achieve two basic goals. One goal is that the participation of branches in U.S. financial markets does not undermine the high standards, efficiency, and confidence in U.S. markets. The second goal is that head office management has adequate controls in place at the branch that both ensure that the branch is operating within corporate policies and enable head office management, and by extension the home country supervisor, to supervise the FBO on a consolidated basis in accordance with the Basle supervisory principles. The rating of operational controls should include the following:
• The adequacy of controls and the level of adherence to existing procedures and systems. (These are separate but related factors.)
• The frequency, scope, and adequacy of the branch's internal and external audit function, relative to the size and risk profile of the branch, and the independence of the internal audit function from line management.
• The number and severity of internal control and audit exceptions.
• Whether internal control and audit exceptions are effectively tracked and resolved in a timely manner.
• The adequacy and accuracy of management information reports. This assessment should be based primarily on whether reports and analysis are sufficient to properly inform head office management of the branch's condition on a timely basis, and whether there are sufficient procedures to ensure the accuracy of those reports.
• Whether the system of controls is regularly reviewed to keep pace with changes in the branch's business plan and laws and regulations.
Operational Controls Ratings
A branch that is rated 1 has a fully comprehensive system of operational controls that protects against losses from transactional and operational risks and ensures accurate financial reporting. Branch operations are fully consistent with sound market practices. The branch also has a well-defined and independent audit function that is appropriate to the size and risk profile of the branch. No supervisory concerns are evident.
A rating of 2 may indicate some minor weaknesses, such as the presence of new business activities where some modest control deficiencies exist, but which management is addressing. Some recommendations may be noted. Overall, the system of controls, including the audit function, is considered satisfactory and effective in maintaining a safe and sound branch operation. Only routine supervisory attention is required.
A rating of 3 indicates that the branch's system of controls, including the quality of the audit function, is lacking in some important respects, particularly as indicated by continued control exceptions and/or substantial deficiencies in or failure to adhere to written policies and procedures. As a result, more than normal supervisory attention is required.
A branch that is rated 4 signifies that the system of operational controls has serious deficiencies that require substantial improvement. In such a case, the branch may lack control functions, including those related to the audit function, that meet minimal expectations; therefore, adherence to bank and regulatory policy is questionable. Head office management has failed to give the branch proper support to maintain operations in accordance with U.S. norms. Close supervisory attention is required.
A branch that is rated 5 lacks a system of operational controls to such a degree that its operations are in serious jeopardy. The branch either lacks or has a wholly deficient audit function. Immediate substantial improvement is required by branch and head office management, along with strong supervisory attention.
Compliance
In addition to maintaining an effective system of operational controls, branches should also demonstrate compliance with all applicable state and federal laws and regulations including reporting and special supervisory requirements. To the extent possible, given the size and risk profile of the branch, these responsibilities should be vested in a branch official or compliance officer whose function is separate from line management. Branch management should also ensure that all appropriate personnel are properly trained in meeting regulatory requirements on an ongoing basis. The scope of the branch's audit function also should ensure that the branch is meeting all applicable regulatory requirements. Accordingly, the branch's level of compliance should be rated based on the following factors:
• The level of adherence to applicable state and federal laws and regulations and any supervisory follow-up actions.
• The effectiveness of (i) written compliance procedures and (ii) training of line personnel charged with maintaining compliance with regulatory requirements.
• Management's ability to submit required regulatory reports in a timely and accurate manner.
• Management's ability to identify and correct compliance issues.
• Whether the internal audit function checks for compliance with applicable state and federal laws and regulations.
Compliance Ratings
A branch accorded a rating of 1 demonstrates an outstanding level of compliance with applicable laws, regulations, and reporting requirements. No supervisory concerns are evident.
A rating of 2 indicates that compliance is generally effective with respect to most factors. Compliance monitoring and related training programs are sufficient to prevent significant problems. Minor reporting errors may be present, but they are being adequately addressed by branch management. Only normal supervisory attention is warranted.
A branch that is rated 3 has deficiencies in management and training systems that result in an atmosphere where significant compliance problems could and do occur. Such deficiencies could include a lack of written compliance procedures, no system for identifying possible compliance issues, or a substantial number of minor or repeat violations or deficiencies. More than normal supervisory attention is warranted.
A rating of 4 indicates that compliance matters are not given proper attention by branch and head office management, and close supervisory attention is warranted. The lack of an effective compliance program, including an ongoing training program, may be evident along with a failure to meet significant regulatory requirements and/or significant, widespread inaccuracies in regulatory reports.
A rating of 5 would signal that attention to compliance matters is wholly lacking at the branch to the extent that immediate supervisory attention is warranted.
Asset Quality
Generally, asset quality is evaluated to determine whether a financial entity has sufficient capital to absorb prospective losses and, ultimately, whether it can maintain its viability as an ongoing entity. The evaluation of asset quality in a branch does not have the same result because a branch is not a separately capitalized entity. Instead, a branch relies on the financial and managerial support of the FBO as a whole.
Nonetheless, the evaluation of asset quality is important both in assessing the effectiveness of credit risk management and in the event of a possible liquidation of a branch. However, as indicated above, a branch is not strictly limited by its own internal and external funding sources in meeting solvency and liquidity needs. The ability of a branch to honor its liabilities ultimately is based upon the condition and level of support from the FBO, a concept that is integral to the FBO supervision program.
This concept states that if the condition of the FBO is satisfactory, the FBO is presumed to be able to support the branch with sufficient capital and reserves on a consolidated basis. As a result, the assessment of asset quality in such circumstances would not, in and of itself, be a predominant factor in the branch's overall assessment, if existing risk management techniques are satisfactory. If, however, the condition of the FBO is less than satisfactory and/or support from the FBO is questionable, the evaluation of asset quality should be carefully considered in determining whether supervisory actions are needed to improve the branch's ability to meet its obligations on a stand-alone basis. In cases where a branch is subject to asset maintenance, it is expected that asset quality issues will be addressed by disqualifying classified assets as eligible assets.
The quality of the branch's stock of assets is evaluated based on the following factors. Generally, credit administration concerns should be addressed in rating risk management.
• The level, distribution, and severity of asset and off-balance-sheet exposures classified for credit and transfer risk.6
• The level and composition of nonaccrual and reduced rate assets.
Asset Quality Ratings
A branch accorded a rating of 1 has strong asset quality.
A branch accorded a rating of 2 has satisfactory asset quality.
A branch accorded a rating of 3 has fair asset quality.
A branch accorded a rating of 4 has marginal asset quality.
A branch accorded a rating of 5 has unsatisfactory asset quality.
December 31, 1998 (rev.)
| TO: | All State-Chartered Trust Companies |
| FROM: | Catherine A. Ghiglieri, Commissioner |
| SUBJECT: | Trust Company Rating Systems |
Overview
The Department of Banking uses two distinct rating systems to assess the condition of state-chartered trust companies under its supervision: the Trust Company Rating System is used to evaluate the strength of the corporate entity; and, a modified version of the federal Uniform Interagency Trust Rating System (UITRS) is used to assess the condition of the fiduciary operations. It is also the policy of the Department to advise boards of directors of trust companies of the ratings assigned pursuant to an examination by this agency. This is consistent with Departmental policy for commercial banks. The Trust Company Rating System and the modified version of the Uniform Interagency Trust Rating System are attached.
Focus of the Rating Systems
The Trust Company Rating System (the CAMEL rating) is similar to the regulatory rating system used for commercial banks. Five primary aspects of the corporate entity's condition are evaluated and rated. These are: Capital adequacy, Asset quality, Management, Earnings and Liquidity; hence, the acronym CAMEL.
Under the modified UITRS, the fiduciary activities of financial institutions are assigned a composite rating based on an evaluation and rating of five essential components of an institution's fiduciary activities. These components address the following: the capability of management; the adequacy of operations, controls and audits; the quality and level of earnings; compliance with governing instruments, applicable law (including self-dealing and conflicts of interest laws and regulations), and sound fiduciary principles; and the management of fiduciary assets.
Disclosure of Ratings
Each rating system arrives at a "composite" rating, disclosed on page 1 of an examination report, which summarizes the overall condition of the company, and reflects the risk and comparable importance of each individual component. While not an arithmetic average of the component ratings, the composite ratings are consistent with the individual component ratings.
The board of directors and management of each trust company is advised of the assigned CAMEL and UITRS ratings in a separate, confidential letter addressed to the board. These ratings are not a matter of public information. By disclosing the entire CAMEL and UITRS ratings to the board, the Department believes directors will be more fully informed of the company's condition and therefore be better equipped to address all financial and operational deficiencies.
ATTACHMENTS
TRUST COMPANY RATING SYSTEM
Overview
The rating system is based upon an evaluation of five critical dimensions of a trust company's operations that reflect in a comprehensive fashion an institution's financial condition, compliance with fiduciary regulations and statutes, and overall operating soundness. The specific dimensions that are to be evaluated are the following:
Capital Adequacy
Asset Quality
Management/Administration
Earnings
Liquidity
Each of these dimensions is rated on a scale of 1 through 5 in descending order of performance quality. Thus, 1 represents the highest and, 5 the lowest (and most critically deficient), level of operating performance.
Each trust company is accorded a summary or composite rating that is predicated upon the evaluations of the specific performance dimensions. The composite rating is also based upon a scale of 1 through 5 in ascending order of supervisory concern. In arriving at a composite rating, each financial dimension must be weighed and due consideration given to the interrelationships among the various aspects of a company's operations. The delineation of specific performance dimensions does not preclude consideration of other factors that, in the judgement of the examiner or reviewer, are deemed relevant to accurately reflect the overall condition and soundness of a particular trust company. However, the assessment of the specific performance dimensions represents the essential foundation upon which the composite rating is based.
Composite Ratings
The five composite ratings are defined and distinguished as follows:
Composite 1
Companies in this group are sound institutions in almost every respect; any critical findings are basically of a minor nature and can be handled in a routine manner. Such companies are resistant to external economic and financial disturbances and capable of withstanding the vagaries of business conditions more ably than companies with lower composite ratings.
Composite 2
Companies in this group are also fundamentally sound institutions but may reflect modest weaknesses correctable in the normal course of business. Such companies are stable and also able to withstand business fluctuations quite well; however, areas of weakness could develop into conditions of greater concern. To the extent that minor adjustments are handled in the normal course of business, the supervisory response is limited.
Composite 3
Companies in this group exhibit a combination of weaknesses ranging from moderately severe to unsatisfactory. Such companies are only nominally resistant to the onset of adverse business conditions and could easily deteriorate if concerted action is not effective in correcting the areas of weakness. Consequently, such companies are vulnerable and require more than normal supervision. Overall strength and financial capacity, however, are still such as to make failure only a remote possibility.
Composite 4
Companies in this group have an immoderate volume of asset weaknesses, or a combination of other conditions that are less than satisfactory. Unless prompt action is taken to correct these conditions, they could reasonably develop into a situation that could impair future viability and/or threaten the safety of fiduciary assets. A potential for failure is present but is not pronounced. Companies in this category require close supervisory attention and financial surveillance.
Composite 5
This category is reserved for companies whose conditions are worse than defined under number 4 above. The volume and character of weaknesses are such as to require urgent aid from the shareholders or other sources. Such companies require immediate corrective action and constant supervisory attention. The probability of failure is high for these companies.
Performance Evaluation
As already noted, the five key performance dimensions -- capital adequacy, asset quality, management/administration, earnings, and liquidity -- are to be evaluated on a scale of one to five. Following is a description of the gradations to be utilized in assignment performance ratings:
Rating No. 1 - indicates strong performance. It is the highest rating and is indicative of performance that is significantly higher than average.
Rating No. 2 - reflects satisfactory performance. It reflects performance that is average or above; it includes performance that adequately provides for the safe and sound operation of the company.
Rating No. 3 - represents performance that is flawed to some degree; as such, is considered fair. It is neither satisfactory nor marginal but is characterized by performance of below average quality.
Rating No. 4 - represents marginal performance which is significantly below average; if left unchecked, such performance might evolve into weaknesses or conditions that could threaten the viability of the institution.
Rating No. 5 - is considered unsatisfactory. It is the lowest rating and is indicative of performance that is critically deficient and in need of immediate remedial attention. Such performance by itself, or in combination with other weaknesses, could threaten the viability of the institution.
Capital Adequacy
Capital is rated 1 through 5 in relation to: (a) the volume of risk assets and off-balance sheet items; (b) the volume of marginal and inferior quality assets; (c) growth experience, plans, and prospects; and, (d) the strength of management in relation to (a), (b) and (c). In addition, consideration may be given to a company's total capital accounts relative to the minimum required level, its earnings retention, and its access to capital markets or other appropriate sources of financial assistance.
Companies rated 1 or 2 are considered to have adequate capital, although the former's capital level will generally exceed that of the latter. A 3 rating should be ascribed to a company's capital position when the relationship of the capital structure to points (a), (b) or (c) is adverse even giving weight to management as a mitigating factor. Companies rated 4 and 5 are clearly inadequately capitalized, the latter representing a situation of such gravity as to threaten viability and solvency. A 5 rating also denotes a company that requires urgent assistance from shareholders or other external sources of financial support.
Asset Quality
Asset quality is rated 1 through 5 in relation to: (a) the level, distribution and severity of classified assets; and, (b) the level and composition of nonaccrual and reduced rate assets. Obviously, adequate valuation reserves mitigate to some degree the weaknesses inherent in a given level of classified assets. In evaluating asset quality, consideration should also be given to any undue degree of concentration of investments, the investment grades and the adequacy of investment policies.
Asset quality ratings of 1 and 2 represent situations involving a minimal level of concern. Both ratings represent sound portfolios although the level and severity of classifications of the latter generally exceed those of the former. A 3 asset rating indicates a situation involving an appreciable degree of concern, especially to the extent that current adverse trends suggest potential future problems. Ratings 4 and 5 represent increasingly more severe asset problems; rating 5, in particular, represents an imminent threat to company viability through the corrosive effect of asset problems on the level of capital support.
Management/Administration
Management's performance must be evaluated against virtually all factors considered necessary to operate the company within accepted fiduciary practices and in a safe and sound manner. Thus, management is rated 1 through 5 with respect to: (a) technical competence, leadership and administrative ability; (b) compliance with regulation and statutes; (c) ability to plan and respond to changing circumstances; (d) adequacy of and compliance with internal policies; (e) depth and succession; (f) tendencies toward self-dealing; and (g) demonstrated willingness to serve the legitimate fiduciary needs of the community.
A 1 rating is indicative of management that is fully effective with respect to almost all factors and exhibits a responsiveness and ability to cope successfully with existing and foreseeable problems that may arise in the conduct of the company's affairs. A 2 rating reflects some deficiencies but generally indicates a satisfactory record of performance in light of the company's particular circumstances. A rating of 3 reflects performance that is lacking in some measure of competence desirable to meet responsibilities of the situation in which management is found. Either it is characterized by modest talent when above-average abilities are called for, or it is distinctly below average for the type and size of company in which it operates. Thus, its responsiveness or ability to correct less than satisfactory conditions may be lacking. The 4 rating is indicative of management that is generally inferior in ability compared to the responsibilities with which it is charged. A rating of 5 is applicable to those instances where incompetence has been demonstrated. In these cases, problems resulting from management weakness are of such severity that management must be strengthened or replaced before sound conditions can be brought about.
Earnings
Earnings will be rated 1 through 5 with respect to: (a) the ability to cover losses and provide for adequate capital; (b) earnings trends; and (c) quality and composition of net income. Consideration must also be given to the interrelationships that exist between the dividend payout ratio, the rate of growth of retained earnings and the adequacy of company capital. A dividend payout rate that is sufficiently high as to cause an adverse relationship to exist suggests conditions warranting a lower rating despite a level of earnings that might otherwise warrant a more favorable appraisal. Quality is also an important factor in evaluating this dimension of a company's performance. Consideration should be given to the adequacy of transfers to a valuation reserve and the extent to which extraordinary items, securities transactions, and tax effects contribute to net income.
Earnings rated 1 are sufficient to make full provision for the absorption of losses and the accretion of capital when due consideration is given to asset quality and company growth. A company whose earnings are relatively static or even moving downward may receive a 2 rating provided its level of earnings is adequate in view of the considerations discussed above. A 3 should be accorded earnings that are not sufficient to make full provision for the absorption of losses and the accretion of capital in relation to company growth. The earnings pictures of such companies may be further clouded by static or inconsistent earnings trends, chronically insufficient earnings, a high dividend payout rate or less than satisfactory asset quality. Earnings rated 4, while generally positive, may be characterized by erratic fluctuations in net income, the development of a downward trend, intermittent losses or a substantial drop from the previous year. Companies with earnings accorded a 5 rating should be experiencing pre-provision operating losses or reflecting a level of earnings that is worse than defined in No. 4 above. Such losses may represent a distinct threat to the company's solvency through the erosion of capital
Liquidity
Liquidity is rated 1 through 5 with respect to: (a) the volatility of trust funds; (b) reliance on interest-sensitive funds and frequency and level of borrowings; (c) technical competence relative to structure of liabilities; (d) availability of assets readily convertible into cash; and (e) access to money markets of other ready sources of cash. Ultimately, the company's liquidity must be evaluated on the basis of its capacity to promptly meet the demand for payment of its obligations. In appraising liquidity, attention should be directed to the company's average liquidity over a specific time period as well as its liquidity position on any particular date. Consideration should be given where appropriate to the overall effectiveness of asset-liability management strategies and compliance with and adequacy of established liquidity policies.
A liquidity rating of 1 indicates a more than sufficient volume of liquid assets and/or ready and easy access on favorable terms to external sources of liquidity within the context of the company's overall asset-liability management strategy. A company developing a trend toward decreasing liquidity and increasing reliance on borrowed funds, yet still within acceptable proportions, may be accorded a 2 rating. A 3 liquidity rating reflects an insufficient volume of liquid assets and/or a reliance on interest-sensitive funds that is approaching or exceeds reasonable proportions for a given company. Ratings of 4 and 5 represent increasingly serious liquidity positions. Companies with liquidity positions so critical as to constitute an imminent threat to continued viability should be accorded a 5 rating. Such companies require immediate remedial action or external financial assistance to allow them to meet their maturing obligations.
UNIFORM INTERAGENCY TRUST RATING SYSTEM (modified)
Overview
Under the modified UITRS, the fiduciary activities of financial institutions are assigned a composite rating based on an evaluation and rating of five essential components of an institution's fiduciary activities. These components address the following: the capability of management; the adequacy of operations, controls and audits; the quality and level of earnings; compliance with governing instruments, applicable law (including self-dealing and conflicts of interest laws and regulations), and sound fiduciary principles; and the management of fiduciary assets.
Composite and component ratings are assigned based on a 1 to 5 numerical scale. A 1 is the highest rating and indicates the strongest performance and risk management practices and the least degree of supervisory concern. A 5 is the lowest rating and indicates the weakest performance and risk management practices and, therefore, the highest degree of supervisory concern. A rating of 0 is also possible under the Asset Management component of the modified UITRS, for institutions which do not engage in any asset management activities. Evaluation of the composite and components considers the size and sophistication, the nature and complexity, and the risk profile of the institution's fiduciary activities.
The composite rating generally bears a close relationship to the component ratings assigned. However, the composite rating is not derived by computing an arithmetic average of the component ratings. Each component rating is based on a qualitative analysis of the factors comprising that component and its interrelationship with the other components. When assigning a composite rating, some components may be given more weight than others depending on the situation at the institution. In general, assignment of a composite rating may incorporate any factor that bears significantly on the overall administration of the financial institution's fiduciary activities. Assigned composite and component ratings are disclosed to the institution's board of directors and senior management.
The ability of management to respond to changing circumstances and to address the risks that may arise from changing business conditions, or the initiation of new fiduciary activities or products, is an important factor in evaluating an institution's overall fiduciary risk profile and the level of supervisory attention warranted. For this reason, the management component is given special consideration when assigning a composite rating.
The ability of management to identify, measure, monitor, and control the risks of its fiduciary operations is also taken into account when assigning each component rating. It is recognized, however, that appropriate management practices may vary considerably among financial institutions, depending on the size, complexity and risk profiles of their fiduciary activities. For less complex institutions engaged solely in traditional fiduciary activities and whose directors and senior managers are actively involved in the oversight and management of day-to-day operations, relatively basic management systems and controls may be adequate. On the other hand, at more complex institutions, detailed and formal management systems and controls are needed to address a broader range of activities and to provide senior managers and directors with the information they need to supervise day-to-day activities.
All institutions are expected to properly manage their risks. For less complex institutions engaging in less risky activities, detailed or highly formalized management systems and controls are not required to receive strong or satisfactory component or composite ratings.
The following two sections contain the composite rating definitions, and the descriptions and definitions for the five component ratings.
Composite Ratings
Composite ratings are based on a careful evaluation of how an institution conducts its fiduciary activities. The review encompasses the capability of management, the soundness of policies and practices, the quality of service rendered to the public, and the effect of fiduciary activities upon the soundness of the institution. The five key components used to assess an institution's fiduciary activities are: the capability of management; the adequacy of operations, controls and audits; the quality and level of earnings; compliance with governing instruments, applicable law (including self-dealing and conflicts of interest laws and regulations), and sound fiduciary principles; and the management of fiduciary assets. The composite ratings are defined as follows:
Composite 1
Administration of fiduciary activities is sound in every respect. Generally all components are rated 1 or 2. Any weaknesses are minor and can be handled in a routine manner by management. The institution is in substantial compliance with fiduciary laws and regulations. Risk management practices are strong relative to the size, complexity, and risk profile of the institution's fiduciary activities. Fiduciary activities are conducted in accordance with sound fiduciary principles and give no cause for supervisory concern.
Composite 2
Administration of fiduciary activities is fundamentally sound. Generally no component rating should be more severe than 3. Only moderate weaknesses are present and are well within management's capabilities and willingness to correct. Fiduciary activities are conducted in substantial compliance with laws and regulations. Overall risk management practices are satisfactory relative to the institution's size, complexity, and risk profile. There are no material supervisory concerns and, as a result, the supervisory response is informal and limited.
Composite 3
Administration of fiduciary activities exhibits some degree of supervisory concern in one or more of the component areas. A combination of weaknesses exists that may range from moderate to severe; however, the magnitude of the deficiencies generally does not cause a component to be rated more severely than 4. Management may lack the ability or willingness to effectively address weaknesses within appropriate time frames. Additionally, fiduciary activities may reveal some significant noncompliance with laws and regulations. Risk management practices may be less than satisfactory relative to the institution's size, complexity, and risk profile. While problems of relative significance may exist, they are not of such importance as to pose a threat to the trust beneficiaries generally, or to the soundness of the institution. The institution's fiduciary activities require more than normal supervision and may include formal or informal enforcement actions.
Composite 4
Fiduciary activities generally exhibit unsafe and unsound practices or conditions, resulting in unsatisfactory performance. The problems range from severe to critically deficient and may be centered around inexperienced or inattentive management, weak or dangerous operating practices, or an accumulation of unsatisfactory features of lesser importance. The weaknesses and problems are not being satisfactorily addressed or resolved by the board of directors and management. There may be significant noncompliance with laws and regulations. Risk management practices are generally unacceptable relative to the size, complexity, and risk profile of fiduciary activities. These problems pose a threat to the account beneficiaries generally and, if left unchecked, could evolve into conditions that could cause significant losses to the institution and ultimately undermine the public confidence in the institution. Close supervisory attention is required, which means, in most cases, formal enforcement action is necessary to address the problems.
Composite 5
Fiduciary activities are conducted in an extremely unsafe and unsound manner. Administration of fiduciary activities is critically deficient in numerous major respects, with problems resulting from incompetent or neglectful administration, flagrant and/or repeated disregard for laws and regulations, or a willful departure from sound fiduciary principles and practices. The volume and severity of problems are beyond management's ability or willingness to control or correct. Such conditions evidence a flagrant disregard for the interests of the beneficiaries and may pose a serious threat to the soundness of the institution. Continuous close supervisory attention is warranted and may include termination of the institution's fiduciary activities.
Component Ratings
Each of the component rating descriptions is divided into three sections: a narrative description of the component; a list of the principal factors used to evaluate that component; and a description of each numerical rating for that component. Some of the evaluation factors are reiterated under one or more of the other components to reinforce the interrelationship among components. The listing of evaluation factors is in no particular order of importance.
Management
This rating reflects the capability of the board of directors and management, in their respective roles, to identify, measure, monitor and control the risks of an institution's fiduciary activities. It also reflects their ability to ensure that the institution's fiduciary activities are conducted in a safe and sound manner, and in compliance with applicable laws and regulations. Directors should provide clear guidance regarding acceptable risk exposure levels and ensure that appropriate policies, procedures and practices are established and followed. Senior fiduciary management is responsible for developing and implementing policies, procedures and practices that translate the board's objectives and risk limits into prudent operating standards.
Depending on the nature and scope of an institution's fiduciary activities, management practices may need to address some or all of the following risks: reputation, operating or transaction, strategic, compliance, legal, credit, market, liquidity and other risks. Sound management practices are demonstrated by: active oversight by the board of directors and management; competent personnel; adequate policies, processes, and controls that consider the size and complexity of the institution's fiduciary activities; and effective risk monitoring and management information systems. This rating should reflect the board's and management's ability as it applies to all aspects of fiduciary activities in which the institution is involved.
The management rating is based upon an assessment of the capability and performance of management and the board of directors, including, but not limited to, the following evaluation factors:
The level and quality of oversight and support of fiduciary activities by the board of directors and management, including committee structure and adequate documentation of committee actions.
The ability of the board of directors and management, in their respective roles, to plan for, and respond to, risks that may arise from changing business conditions or the introduction of new activities or products.
The adequacy of, and conformance with, appropriate internal policies, practices and controls addressing the operations and risks of significant fiduciary activities.
The accuracy, timeliness, and effectiveness of management information and risk monitoring systems appropriate for the institution's size, complexity, and fiduciary risk profile.
The overall level of compliance with laws, regulations, and sound fiduciary principles.
Responsiveness to recommendations from auditors and regulatory authorities.
Strategic planning for fiduciary products and services.
The level of experience and competence of fiduciary management and staff, including issues relating to turnover and succession planning.
The adequacy of insurance coverage.
The availability of competent legal counsel.
The extent and nature of pending litigation associated with fiduciary activities, and its potential impact on earnings, capital, and the institution's reputation.
The process for identifying and responding to fiduciary customer complaints.
Management Ratings
Rating No. 1 - indicates strong performance by management and the board of directors and strong risk management practices relative to the size, complexity and risk profile of the institution's fiduciary activities. All significant risks are consistently and effectively identified, measured, monitored, and controlled. Management and the board are proactive, and have demonstrated the ability to promptly and successfully address existing and potential problems and risks.
Rating No. 2 - indicates satisfactory management and board performance and risk management practices relative to the size, complexity and risk profile of the institution's fiduciary activities. Moderate weaknesses may exist, but are not material to the sound administration of fiduciary activities, and are being addressed. In general, significant risks and problems are effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates management and board performance that needs improvement or risk management practices that are less than satisfactory given the nature of the institution's fiduciary activities. The capabilities of management or the board of directors may be insufficient for the size, complexity, and risk profile of the institution's fiduciary activities. Problems and significant risks may be inadequately identified, measured, monitored, or controlled.
Rating No. 4 - indicates deficient management and board performance or risk management practices that are inadequate considering the size, complexity, and risk profile of the institution's fiduciary activities. The level of problems and risk exposure is excessive. Problems and significant risks are inadequately identified, measured, monitored, or controlled and require immediate action by the board and management to protect the assets of account beneficiaries and to prevent erosion of public confidence in the institution. Replacing or strengthening management or the board may be necessary.
Rating No. 5 - indicates critically deficient management and board performance or risk management practices. Management and the board of directors have not demonstrated the ability to correct problems and implement appropriate risk management practices. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the continued viability of the institution or its administration of fiduciary activities, and pose a threat to the safety of the assets of account beneficiaries. Replacing or strengthening management or the board of directors is necessary.
Operations, Internal Controls & Auditing
This rating reflects the adequacy of the institution's fiduciary operating systems and internal controls in relation to the volume and character of business conducted. Audit coverage must assure the integrity of the financial records, the sufficiency of internal controls, and the adequacy of the compliance process.
The institution's fiduciary operating systems, internal controls, and audit function subject it primarily to transaction and compliance risk. Other risks including reputation, strategic, and financial risk may also be present. The ability of management to identify, measure, monitor and control these risks is reflected in this rating. The operations, internal controls and auditing rating is based upon, but not limited to, an assessment of the following evaluation factors:
Operations and Internal Controls, including the adequacy of:
Staff, facilities and operating systems;
Records, accounting and data processing systems (including controls over systems access and such accounting procedures as aging, investigation and disposition of items in suspense accounts);
Trading functions and securities lending activities;
Vault controls and securities movement;
Segregation of duties;
Controls over disbursements (checks or electronic) and unissued securities;
Controls over income processing activities;
Reconciliation processes (depository, cash, vault, sub-custodians, suspense accounts, etc.);
Disaster and/or business recovery programs;
Hold-mail procedures and controls over returned mail; and,
Investigation and proper escheatment of funds in dormant accounts.
Auditing, including:
The independence, frequency, quality and scope of the internal and external fiduciary audit function relative to the volume, character and risk profile of the institution's fiduciary activities;
The volume and/or severity of internal control and audit exceptions and the extent to which these issues are tracked and resolved; and
The experience and competence of the audit staff.
Operations, Internal Controls & Auditing Ratings
Rating No. 1 - indicates that operations, internal controls, and auditing are strong in relation to the volume and character of the institution's fiduciary activities. All significant risks are consistently and effectively identified, measured, monitored, and controlled.
Rating No. 2 - indicates that operations, internal controls and auditing are satisfactory in relation to the volume and character of the institution's fiduciary activities. Moderate weaknesses may exist, but are not material. Significant risks, in general, are effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates that operations, internal controls or auditing need improvement in relation to the volume and character of the institution's fiduciary activities. One or more of these areas are less than satisfactory. Problems and significant risks may be inadequately identified, measured, monitored, or controlled.
Rating No. 4 - indicates deficient operations, internal controls or audits. One or more of these areas are inadequate or the level of problems and risk exposure is excessive in relation to the volume and character of the institution's fiduciary activities. Problems and significant risks are inadequately identified, measured, monitored, or controlled and require immediate action. Institutions with this level of deficiencies may make little provision for audits, or may evidence weak or potentially dangerous operating practices in combination with infrequent or inadequate audits.
Rating No. 5 - indicates critically deficient operations, internal controls or audits. Operating practices, with or without audits, pose a serious threat to the safety of assets of fiduciary accounts. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the ability of the institution to continue engaging in fiduciary activities.
Earnings
This rating reflects the profitability of an institution's fiduciary activities and its effect on the financial condition of the institution. The use and adequacy of budgets and earnings projections by functions, product lines and clients are reviewed and evaluated.
Risk exposure that may lead to negative earnings is also evaluated.
The evaluation of earnings is based upon, but not limited to, an assessment of the following factors:
The profitability of fiduciary activities in relation to the size and scope of those activities and to the overall business of the institution.
The overall importance to the institution of offering fiduciary services to its customers and local community.
The effectiveness of the institution's procedures for monitoring fiduciary activity income and expense relative to the size and scope of these activities and their relative importance to the institution, including the frequency and scope of profitability reviews and planning by the institution's board of directors or a committee thereof.
The level and consistency of profitability, or the lack thereof, generated by the institution's fiduciary activities in relation to the volume and character of the institution's business.
Dependence upon non-recurring fees and commissions, such as fees for court accounts.
The effects of charge-offs or compromise actions.
Unusual features regarding the composition of business and fee schedules.
Accounting practices that contain practices such as (1) unusual methods of allocating direct and indirect expenses and overhead, or (2) unusual methods of allocating fiduciary income and expense where two or more fiduciary institutions within the same holding company family share fiduciary services and/or processing functions.
The extent of management's use of budgets, projections and other cost analysis procedures.
Methods used for directors' approval of financial budgets and/or projections.
Management's attitude toward growth and new business development.
New business development efforts, including types of business solicited, market potential, advertising, competition, relationships with local organizations, and an evaluation by management of risk potential inherent in new business areas.
Earnings Ratings
Rating No. 1 - indicates strong earnings. The institution consistently earns a rate of return on its fiduciary activities that is commensurate with the risk of those activities. This rating would normally be supported by a history of consistent profitability over time and a judgement that future earnings prospects are favorable. In addition, management techniques for evaluating and monitoring earnings performance are fully adequate and there is appropriate oversight by the institution's board of directors or a committee thereof. Management makes effective use of budgets and cost analysis procedures. Methods used for reporting earnings information to the board of directors, or a committee thereof, are comprehensive.
Rating No. 2 - indicates satisfactory earnings. Although the earnings record may exhibit some weaknesses, earnings performance does not pose a risk to the overall institution nor to its ability to meet its fiduciary obligations. Generally, fiduciary earnings meet management targets and appear to be at least sustainable. Management processes for evaluating and monitoring earnings are generally sufficient in relationship to the size and risk of fiduciary activities that exist, and any deficiencies can be addressed in the normal course of business. A rating of 2 may also be assigned to institutions with a history of profitable operations if there are indications that management is engaging in activities with which it is not familiar, or where there may be inordinately high levels of risk present that have not been adequately evaluated. Alternatively, an institution with otherwise strong earnings performance may also be assigned a 2 rating if there are significant deficiencies in its methods used to monitor and evaluate earnings.
Rating No. 3 - indicates less than satisfactory earnings. Earnings are not commensurate with the risk associated with the fiduciary activities undertaken. Earnings may be erratic or exhibit downward trends, and future prospects are unfavorable. This rating may also be assigned if management processes for evaluating and monitoring earnings exhibit serious deficiencies, provided the deficiencies identified do not pose an immediate danger to either the overall financial condition of the institution or its ability to meet its fiduciary obligations.
Rating No. 4 - indicates earnings that are seriously deficient. Fiduciary activities have a significant adverse effect on the overall income of the institution and its ability to generate adequate capital to support the continued operation of its fiduciary activities. The institution is characterized by fiduciary earnings performance that is poor historically, or faces the prospect of significant losses in the future. Management processes for monitoring and evaluating earnings may be poor. The board of directors has not adopted appropriate measures to address significant deficiencies.
Rating No. 5 - indicates critically deficient earnings. In general, an institution with this rating is experiencing losses from fiduciary activities that have a significant negative impact on the overall institution, representing a distinct threat to its viability through the erosion of its capital. The board of directors has not implemented effective actions to address the situation.
Compliance
This rating reflects an institution's overall compliance with applicable laws, regulations, accepted standards of fiduciary conduct, governing account instruments, duties associated with account administration, and internally established policies and procedures. This component specifically incorporates an assessment of a fiduciary's duty of undivided loyalty and compliance with applicable laws, regulations, and accepted standards of fiduciary conduct related to self-dealing and other conflicts of interest.
The compliance component includes reviewing and evaluating the adequacy and soundness of adopted policies, procedures, and practices generally, and as they relate to specific transactions and accounts. It also includes reviewing policies, procedures, and practices to evaluate the sensitivity of management and the board of directors to refrain from self-dealing, minimize potential conflicts of interest, and resolve actual conflict situations in favor of the fiduciary account beneficiaries.
Risks associated with account administration are potentially unlimited because each account is a separate contractual relationship that contains specific obligations. Risks associated with account administration include: failure to comply with applicable laws, regulations or terms of the governing instrument; inadequate account administration practices; and inexperienced management or inadequately trained staff. Risks associated with a fiduciary's duty of undivided loyalty generally stem from engaging in self-dealing or other conflict of interest transactions. An institution may be exposed to compliance, strategic, financial and reputation risk related to account administration and conflicts of interest activities. The ability of management to identify, measure, monitor and control these risks is reflected in this rating. Policies, procedures and practices pertaining to account administration and conflicts of interest are evaluated in light of the size and character of an institution's fiduciary business.
The compliance rating is based upon, but not limited to, an assessment of the following evaluation factors:
Compliance with applicable federal and state statutes and regulations, including, but not limited to, federal and state fiduciary laws, the Employee Retirement Income Security Act of 1974, federal and state securities laws, state investment standards, state principal and income acts, and state probate codes;
Compliance with the terms of governing instruments;
The adequacy of overall policies, practices, and procedures governing compliance, considering the size, complexity, and risk profile of the institution's fiduciary activities;
The adequacy of policies and procedures addressing account administration;
The adequacy of policies and procedures addressing conflicts of interest, including those designed to prevent the improper use of "material inside information";
The effectiveness of systems and controls in place to identify actual and potential conflicts of interest;
The adequacy of securities trading policies and practices relating to the allocation of brokerage business, the payment of services with "soft dollars" and the combining, crossing, and timing of trades;
The extent and permissibility of transactions with related parties, including, but not limited to, the volume of related commercial and fiduciary relationships and holdings of corporations in which directors, officers, or employees of the institution may be interested;
The decision making process used to accept, review, and terminate accounts; and,
The decision making process related to account administration duties, including cash balances, overdrafts, and discretionary distributions.
Compliance Ratings
Rating No. 1 - indicates strong compliance policies, procedures and practices. Policies and procedures covering conflicts of interest and account administration are appropriate in relation to the size and complexity of the institution's fiduciary activities. Accounts are administered in accordance with governing instruments, applicable laws and regulations, sound fiduciary principles, and internal policies and procedures. Any violations are isolated, technical in nature and easily correctable. All significant risks are consistently and effectively identified, measured, monitored and controlled.
Rating No. 2 - indicates fundamentally sound compliance policies, procedures and practices in relation to the size and complexity of the institution's fiduciary activities. Account administration may be flawed by moderate weaknesses in policies, procedures or practices. Management's practices indicate a determination to minimize the instances of conflicts of interest. Fiduciary activities are conducted in substantial compliance with laws and regulations, and any violations are generally technical in nature. Management corrects violations in a timely manner and without loss to fiduciary accounts. Significant risks are effectively identified, measured, monitored, and controlled.
Rating No. 3 - indicates compliance practices that are less than satisfactory in relation to the size and complexity of the institution's fiduciary activities. Policies, procedures and controls have not proven effective and require strengthening. Fiduciary activities may be in substantial noncompliance with laws, regulations or governing instruments, but losses are no worse than minimal. While management may have the ability to achieve compliance, the number of violations that exist, or the failure to correct prior violations, are indications that management has not devoted sufficient time and attention to its compliance responsibilities. Risk management practices generally need improvement.
Rating No. 4 - indicates an institution with deficient compliance practices in relation to the size and complexity of its fiduciary activities. Account administration is notably deficient. The institution makes little or no effort to minimize potential conflicts or refrain from self-dealing, and is confronted with a considerable number of potential or actual conflicts. Numerous substantive and technical violations of laws and regulations exist and many may remain uncorrected from previous examinations. Management has not exerted sufficient effort to effect compliance and may lack the ability to effectively administer fiduciary activities. The level of compliance problems is significant and, if left unchecked, may subject the institution to monetary losses or reputation risk. Risks are inadequately identified, measured, monitored and controlled.
Rating No. 5 - indicates critically deficient compliance practices. Account administration is critically deficient or incompetent and there is a flagrant disregard for the terms of the governing instruments and interests of account beneficiaries. The institution frequently engages in transactions that compromise its fundamental duty of undivided loyalty to account beneficiaries. There are flagrant or repeated violations of laws and regulations and significant departures from sound fiduciary principles. Management is unwilling or unable to operate within the scope of laws and regulations or within the terms of governing instruments and efforts to obtain voluntary compliance have been unsuccessful. The severity of noncompliance presents an imminent monetary threat to account beneficiaries and creates significant legal and financial exposure to the institution. Problems and significant risks are inadequately identified, measured, monitored, or controlled and now threaten the ability of management to continue engaging in fiduciary activities.
Asset Management
This rating reflects the risks associated with managing the assets (including cash) of others. Prudent portfolio management is based on an assessment of the needs and objectives of each account or portfolio. An evaluation of asset management should consider the adequacy of processes related to the investment of all discretionary accounts and portfolios, including collective investment funds, proprietary mutual funds, and investment advisory arrangements.
The institution's asset management activities subject it to reputation, compliance and strategic risks. In addition, each individual account or portfolio managed by the institution is subject to financial risks such as market, credit, liquidity, and interest rate risk, as well as transaction and compliance risk. The ability of management to identify, measure, monitor and control these risks is reflected in this rating.
The asset management rating is based upon, but not limited to, an assessment of the following evaluation factors:
The adequacy of overall policies, practices and procedures governing asset management, considering the size, complexity and risk profile of the institution's fiduciary activities.
The decision-making processes used for selection, retention and preservation of discretionary assets including adequacy of documentation, committee review and approval, and a system to review and approve exceptions.
The use of quantitative tools to measure the various financial risks in investment accounts and portfolios.
The existence of policies and procedures addressing the use of derivatives or other complex investment products.
The adequacy of procedures related to the purchase or retention of miscellaneous assets including real estate, notes, closely held companies, limited partnerships, mineral interests, insurance and other unique assets.
The extent and adequacy of periodic reviews of investment performance, taking into consideration the needs and objectives of each account or portfolio.
The monitoring of changes in the composition of fiduciary assets for trends and related risk exposure.
The quality of investment research used in the decision-making process and documentation of the research.
The due diligence process for evaluating investment advice received from vendors and/or brokers (including approved or focus lists of securities).
The due diligence process for reviewing and approving brokers and/or counter parties used by the institution.
Asset Management Ratings
This rating may not be applicable for some institutions because their operations do not include activities involving the management of any discretionary assets. Functions of this type would include, but not necessarily be limited to, directed agency relationships, securities clearing, non-fiduciary custody relationships, transfer agent and registrar activities. In institutions of this type, the rating for Asset Management may be omitted by the examiner in accordance with the examining agency's implementing guidelines. However, this component should be assigned when the institution provides investment advice, even though it does not have discretion over the account assets. An example of this type of activity would be where the institution selects or recommends the menu of mutual funds offered to participant directed 401(k) plans.
Rating No. 0 - indicates an institution that does not engage in any asset management. Functions that do not require management may include, but are not necessarily limited to: directed agency relationships, securities clearing, non-fiduciary custody relationships, and transfer agent and registrar activities. In institutions of this type, the Asset Management rating may be 0 if:
Operations do not include activities involving the management of any discretionary assets.
Investment advisory services are not offered.
There are no assets held on-site.
There are no unique assets, such as closely-held investments, real estate, limited partnerships, or notes receivable, that require special handling such as non-standard registration or insurance protection.
There is no discretion regarding the investment of cash balances.
Although administering a participant-directed plan, the institution does not select or recommend the menu of funds offered to the participants.
Rating No. 1 - indicates strong asset management practices. Identified weaknesses are minor in nature. Risk exposure is modest in relation to management's abilities and the size and complexity of the assets managed.
Rating No. 2 - indicates satisfactory asset management practices. Moderate weaknesses are present and are well within management's ability and willingness to correct. Risk exposure is commensurate with management's abilities and the size and complexity of the assets managed. Supervisory response is limited.
Rating No. 3 - indicates that asset management practices are less than satisfactory in relation to the size and complexity of the assets managed. Weaknesses may range from moderate to severe; however, they are not of such significance as to generally pose a threat to the interests of account beneficiaries. Asset management and risk management practices generally need to be improved. An elevated level of supervision is normally required.
Rating No. 4 - indicates deficient asset management practices in relation to the size and complexity of the assets managed. The levels of risk are significant and inadequately controlled. The problems pose a threat to account beneficiaries generally, and if left unchecked, may subject the institution to losses and could undermine the reputation of the institution.
Rating No. 5 - represents critically deficient asset management practices and a flagrant disregard of fiduciary duties. These practices jeopardize the interests of account beneficiaries, subject the institution to losses, and may pose a threat to the soundness of the institution.
April 11, 2024
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Examination Frequency for State-chartered Banks1 |
BACKGROUND
Section 31.105 of the Texas Finance Code requires the banking commissioner to examine each state bank annually or on another periodic basis as may be required by rule or policy, or as the commissioner considers necessary to safeguard the interests of depositors, creditors, and shareholders, and efficiently enforce applicable law.
PURPOSE
The intent of this Supervisory Memorandum is to clearly communicate the Department of Banking's (Department) on-site examination timing requirements for state banks and trust departments of state banks and promote an efficient regulatory system. To promote competitive parity, the Department generally attempts to align its examination frequency policy for state-chartered banks with the examination frequency requirements applied by the federal bank supervisory agencies, as set forth in 12 U.S.C. 1820(d)(4) and implemented by 12 C.F.R. §208.64 (for member banks) or §337.12 (for nonmember banks), subject to safety and soundness considerations. This Supervisory Memorandum does not limit the authority of the banking commissioner to examine any state bank as frequently as deemed necessary.
BANK EXAMINATION FREQUENCY POLICY
The Department, in cooperation with the Federal Deposit Insurance Corporation (FDIC) and the Federal Reserve Bank of Dallas (FRB), has committed to coordinating examination efforts to reduce regulatory burden. The general practice of the agencies is to alternate examinations between the Department and the FDIC or, if the institution is a member bank, with the FRB. However, the Department will conduct an independent examination or a joint examination with the appropriate federal supervisory agency whenever deemed appropriate.
Banks which meet certain qualifying criteria (outlined below) may have the examination frequency extended to a maximum of 18 months. While the examination frequency for banks may change based on the criteria in the table below, the general practice of alternating examinations between the state and appropriate federal agency will continue.
EXAMINATION SCOPE
The scope of each examination is based upon circumstances of the individual financial institution. The Department utilizes four types of examination scopes: Full Scope, Continuous, Visitation, and Interim Risk Examination and Assessment.
• A Full Scope Examination is the most comprehensive with the Department's examiners completing procedures that are designed to assess the safety and soundness of the bank's operations and activities, resulting in the assignment of an appropriate CAMELS (Capital, Asset Quality, Management, Earnings, Liquidity, and Sensitivity to Market Risk) rating. A Report of Examination is produced for the bank to review.
• A Visitation is a narrowly scoped examination which may focus on one or more CAMELS components, a specific risk area, or compliance with an enforcement action. The results of a Visitation will be documented with a Letter of Findings to the bank. The FDIC's use of a Visitation or the FRB’s use of a Target Examination may be different in scope than the Visitation performed by the Department. The Department may accept risk assessment rating changes from a federal agency Visitation/Target review conducted between annual Full Scope examinations.
• An Interim Risk Examination and Assessment Program (IREAP) is an examination that consists of risk-focused reviews of the CAMELS components, an assessment of compliance with enforcement actions, and a review of any significant criticisms noted at the last examination which affects a CAMELS component. At the conclusion of an IREAP, a CAMELS component or the overall CAMELS rating may be changed. Findings are documented in a Report of Examination when two or more CAMELS components or the overall CAMELS rating is changed. If no change is made to the overall CAMELS rating but one CAMELS component or receives an upgrade or a downgrade, then a Letter of Findings will be provided to the bank instead of a Report of Examination.
• A Continuous Examination Program (CEP) is primarily utilized in larger institutions, generally $10 billion and greater or as determined by the Commissioner or Deputy Commissioner, and includes a series of targeted reviews conducted over an examination cycle generally covering a 12-month period. The targeted reviews focus on one or more specific risk areas of an institution's operations. Under the CEP, all CAMELS components are evaluated during the examination cycle. The results of targeted reviews are documented in a Letter of Findings. The results of targeted reviews performed during the examination cycle are utilized to assign a composite CAMELS rating for the institution which is documented in a formal Report of Examination.
The Full Scope examination as well as the CEP meet the examination priorities of the Department and federal regulators. If at any time it becomes apparent that the planned scope of supervisory activity should be expanded, the Department will not hesitate to do so.
EXAMINATION SCOPE AND FREQUENCY SCHEDULE
The following chart details the general criteria for determining examination frequency of state-chartered banks for Safety and Soundness examinations. The frequency and scope outlined in the Examination Scope and Frequency Schedule meet the examination priorities of the Department. Examinations started 30 days or less after the due date are considered to meet the Department's performance measures. Examinations started 60 days or more before the due date or more than 30 days after the due date require approval by the Director of Bank and Trust Supervision and the Commissioner or the Deputy Commissioner.
EXAMINATION SCOPE AND FREQUENCY SCHEDULE
|
Generally, Full Scope examinations of banks with total assets greater than $1 billion will be conducted jointly with the appropriate federal regulator. Full Scope examinations of 3, 4, and 5 rated institutions should be conducted jointly with the appropriate federal regulator. The examinations for 1 or 2 rated de novo institutions will be conducted jointly with the appropriate federal regulator for the first three years and then continue on an alternating basis.
An Information Technology (IT) review should be performed to coincide with the Full Scope examination as outlined in Supervisory Memorandum 1020.
EXCEPTIONS TO BANK EXAMINATION FREQUENCY SCHEDULE
Exceptions may be made to the examination frequency schedule of a bank depending upon the circumstances as determined by the Director of Bank and Trust Supervision and the Commissioner or the Deputy Commissioner. The following addresses when an examination schedule may be shortened or lengthened temporarily, and the authorization required.
Shortened Examination Frequency
Banks that qualify for an 18-month examination frequency cycle may be subject to a 12-month examination cycle as determined by the Director of Bank and Trust Supervision and the Commissioner or the Deputy Commissioner. A shortened examination cycle may be necessary for institutions operating under certain circumstances which include but are not limited to the following:
a. a change of control during the preceding 12 month period;
b. a Capital, Asset Quality, Earnings, Liquidity or Sensitivity to Market Risk component rating of "3", "4", or "5" as defined by the Uniform Financial Institutions Rating System; or
c. a formal or informal enforcement action.
Extended Examination Frequency
An extension to the examination frequency schedule for banks is permitted under certain circumstances. The reason(s) for the extension must be in writing, maintained with the institution's records at the Department, and be approved by the Commissioner or Deputy Commissioner.
The Commissioner has authority to extend the date of any type of examination (Safety and Soundness, Information Technology, or Trust Department) up to six months predicated on extenuating circumstances including, but not limited to:
a. an anticipated merger or acquisition with another institution;
b. an anticipated change in charter;
c. a disruption in normal operations due a natural disaster or state of emergency; or
d. other significant reasons as determined by the Commissioner or Deputy Commissioner.
Authority to extend an examination beyond six months requires approval of the Commissioner.
TRUST DEPARTMENT EXAMINATION FREQUENCY POLICY
For banks with Trust departments, Trust examinations generally will be scheduled within 120 days prior to, or on the same day as, the start date of the safety and soundness examination. In certain circumstances, trust examinations may be delayed up to 60 days after the safety and soundness examination start date, with the concurrence of the Director of Bank and Trust Supervision. The flexible due date allows coordination with the bank to reduce the regulatory burden and preclude conflicts with safety and soundness examination procedures. Generally, banks eligible for an 18-month or subject to a 12-month safety and soundness examination cycle will require Trust Department examinations of a like frequency. However, banks subject to a 6-month safety and soundness examination cycle are eligible to have a Trust Department examination waived if the most recent Trust examination occurred within the last 12 months and the Trust composite risk rating is a "1" or "2". In situations where the most recent composite risk rating is "3", "4" or "5", the scope and frequency of the next Trust Department review will be established by the Chief Trust Examiner and the Director of Bank and Trust Supervision.
For examinations of Trust departments of banks under the CEP, targeted reviews are conducted over an examination cycle generally covering a 12-month period and focus on one or more specific risk areas of the institution’s trust operations.
The findings of the Trust examination may be embedded into the bank safety and soundness Report of Examination or delivered separately as an independent Report of Examination, as determined by the Chief Trust Examiner and applicable Regional Director. The examination frequency policy for Trust Companies is addressed in Supervisory Memorandum 1004. The findings of the Trust examination performed for a bank under the CEP will be documented in a Letter of Findings.
CONTACT INFORMATION
Questions about this Supervisory Memorandum may be directed to the Director of Bank and Trust Supervision at 512-475-1300.
April 11, 2024
| TO: | All State-Chartered Trust Companies |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Examination Frequency for Trust Companies 1 |
BACKGROUND
Section 181.104 of the Texas Finance Code (TFC) requires that the banking commissioner examine each state trust company annually, or on another periodic basis as may be required by rule or policy, or as the commissioner considers necessary to safeguard the interests of clients, creditors, shareholders, participants, or participant-transferees and efficiently enforce applicable law. Additionally, section 182.013 of the TFC allows the banking commissioner to examine or investigate an exempt 2 state trust company periodically, as necessary, to verify the annual certification required to be filed by an exempt state trust company.
PURPOSE
This Supervisory Memorandum specifically outlines the Department of Banking's (Department) examination priorities for trust companies and the types of examination scopes utilized. The applicability of this policy to exempt trust companies is specifically addressed in the Examination Scope and Frequency Schedule.
EXAMINATION FREQUENCY POLICY
The general policy of the Department is to conduct an on-site examination at every trust company at least annually. Trust companies which meet certain qualifying criteria may have the examination frequency extended to a maximum of 18 months. Qualifying criteria and examination frequency are outlined in the Examination Scope and Frequency Schedule included in this policy. Risk, and thus examination frequency, is generally determined by the supervisory ratings assigned to the trust company. Ratings definitions are found in Supervisory Memorandum 1002. Examinations performed by the Federal Deposit Insurance Corporation (FDIC) or Federal Reserve Bank (FRB) are considered acceptable for meeting these priorities when a trust company is an affiliate of a bank, under a bank holding company, or subject to FDIC or FRB review by federal statute.
EXAMINATION SCOPE
The scope of each examination is based upon circumstances of the individual trust company. The Department utilizes two types of examination scopes for trust companies: Full Scope and Visitation. The Full Scope examination meets the requirements of the Department's examination priorities for measuring performance.
• A Full Scope Examination is the most comprehensive with the Department's examiners completing procedures that are designed to assess the safety and soundness of the trust company's operations and activities, resulting in an appropriate Trust Company Rating which includes Capital, Asset Quality, Management, Earnings, and Liquidity (CAMEL); and a Uniform Interagency Trust Rating which covers Management; Operations, Internal Controls, and Audits; Earnings; Compliance; and Asset Management (MOECA). A formal Report of Examination is produced for the trust company to review.
• A Visitation is a narrowly scoped examination which may focus on one or more Corporate or Fiduciary components, a specific risk area, or compliance with an enforcement action. The results of a Visitation will be documented with a Letter of Findings to the trust company.
If at any time it becomes apparent that the planned scope of supervisory activity should be expanded, the Department will not hesitate to do so.
EXAMINATION SCOPE AND FREQUENCY SCHEDULE
The following chart details the general criteria for determining the examination frequency of state-chartered trust companies for Safety and Soundness examinations. The frequency and scope outlined in the Examination Scope and Frequency Schedule meet the examination priorities of the Department. Examinations started 30 days or less after the due date are considered to meet the Department's performance measures. Examinations started 60 days or more before the due date or more than 30 days after the due date require approval by the Director of Bank and Trust Supervision and the Deputy Commissioner, or Commissioner.
EXAMINATION SCOPE AND FREQUENCY SCHEDULE FOR TRUST COMPANIES
|
An Information Technology (IT) review for a trust company should be performed to coincide with the examinations as outlined in Supervisory Memorandum 1020. Trust companies exempt under TFC §182.011 do not receive an IT examination.
EXCEPTIONS TO EXAMINATION FREQUENCY SCHEDULE
Exceptions may be made to the examination frequency schedule of a trust company depending upon the circumstances as determined by the Director of Bank and Trust Supervision and the Commissioner or the Deputy Commissioner. The following addresses when an examination schedule may be shortened or lengthened temporarily and the authorization required.
Shortened Examination Frequency
A trust company that qualifies for an 18-month examination frequency cycle may be subject to a 12-month examination cycle as determined by the Director of Bank and Trust Supervision and the Commissioner or Deputy Commissioner. A shortened examination cycle may be necessary for institutions operating under certain circumstances which include but are not limited to the following:
a. a change of control during the preceding 12-month period;
b. a formal or informal enforcement action;
c. a Capital, Asset Quality, Earnings, or Liquidity component rating of "3", "4", or "5" as defined by the Uniform Financial Institutions Rating System; or
d. an Operations, Internal Controls, and Audits; Earnings; Compliance; or Asset Management rating of "3","4", or "5" as defined by the Uniform Interagency Trust Rating System.
Extended Examination Frequency
An extension to the examination frequency schedule for trust companies is permitted under certain circumstances. The reason(s) for the extension must be in writing, maintained with the institution's records at the Department, and be approved by the Commissioner or Deputy Commissioner.
The Commissioner has authority to extend the date of a Safety and Soundness or Information Technology examination up to six months predicated on extenuating circumstances including, but not limited to:
a. an anticipated merger or acquisition with another institution;
b. an anticipated change in charter;
c. a disruption in normal operations due a natural disaster or state of emergency; or
d. other significant reasons as determined by the Commissioner or Deputy Commissioner.
Extending an examination beyond six months requires approval of the Commissioner.
CONTACT INFORMATION
Questions regarding this Supervisory Memorandum may be directed to either Jared Whitson, Director of Bank and Trust Supervision, at (512) 475-1300, or Sylvia Fry, Chief Trust Examiner, at (972) 935-8698.
October 25, 2023
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Commissioner |
| SUBJECT: | Policy on Enforcement Actions for State-Chartered Banks 1 |
Overview
The purpose of this Memorandum is to set forth the circumstances under which enforcement actions are used by the Department of Banking (Department) with regard to the banks and bank holding companies 2 under its regulation, and to specify the general methodology which is followed. An enforcement action is designed to address and correct specific problems identified within the financial and operational affairs of a banking institution and is an essential element of effective regulation.
Public Disclosure of Enforcement Actions
Other than final Prohibition or Removal Orders, Department enforcement actions, whether informal or formal, are confidential. The Banking Commissioner (Commissioner) has discretion to publicize final Cease and Desist Orders, final Administrative Penalty Orders, Orders of Supervision, and Orders of Conservatorship if the Commissioner concludes that the release would enhance effective enforcement of the order.
Definitions
"Management" includes bank officers as well as bank directors.
"Regulatory responses" are actions taken by the Department in response to particular conditions at a bank. They include informal communications as well as enforcement actions.
Policy for Implementing Enforcement Actions
Regulatory responses are initiated whenever the Department becomes aware of situations or issues that weaken the safety and soundness of an institution, or that arise from non-compliance with policies, procedures, regulations, or laws.
To assure uniformity of action and to ensure that supervisory efforts are directed to banks exhibiting elevated risk profiles or other major deficiencies, the general policy of the Department is to initiate enforcement actions on banks with composite CAMELS ratings of "3," "4," or "5." (The CAMELS rating system is defined in Supervisory Memorandum -1001.) Banks rated "1" or "2" generally do not warrant an enforcement action, although the Department may initiate one depending on the specific circumstances of the institution. In particular, banks have Information Technology examinations and Bank Secrecy Act examinations that may reveal the need for an enforcement action even though the bank has a composite rating of "1" or "2."
Enforcement actions often set forth the practices, conditions, and violations giving rise to the particular problems or weaknesses identified. The actions also outline specific corrective measures, often including appropriate time frames and goals for achievement. Specific types of enforcement actions available to the Department are outlined below in the section, "Types of Enforcement Actions."
The Department's enforcement actions are not part of a hierarchy; they are not designed to build on one another. On a case-by-case basis, the Department thoroughly analyzes the situation at the bank and designs the action it believes to be the most effective in curing the bank's adverse conditions.
Bank Ratings
1-Rated Banks
A composite "1" rating implies that a bank is sound in all respects and that any weaknesses or deficiencies are so insignificant or immaterial that they pose no supervisory concern. Regulatory responses are generally limited to informal requests for future plans and/or a written response from the bank regarding the examiner's findings as indicated in the report of examination.
2-Rated Banks
Banks having a composite rating of "2" are fundamentally sound. Identified weaknesses or deficiencies are generally of a moderate nature and correction is attainable in the normal course of business. Regulatory responses are the same as for 1-rated banks; however, a Board Resolution may be initiated depending on specific circumstances encountered. In instances of repeated or willful law violations and/or continuing unsound banking practices, the issuance of a stronger enforcement action may be warranted.
3-Rated Banks
A composite "3" rating implies that a bank has weaknesses which, if not corrected, could worsen into a more severe situation. Regulatory responses will most likely be enforcement actions which require remedial action.
4 and 5-Rated Banks
Banks with composite ratings of "4" or "5," by definition, have problems of sufficient severity to warrant a strong regulatory response. An enforcement action such as a Cease and Desist Order is issued when there is evidence of unsafe and unsound practices or conditions. Exceptions to this policy are considered only when the condition of the bank clearly reflects significant improvement resulting from an effective correction program or where individual circumstances militate against the appropriateness or feasibility of strong enforcement actions.
Types of Enforcement Actions
Enforcement actions are either formal or informal. With the exception of determination letters, informal enforcement actions are voluntary commitments made by bank management designed to correct identified deficiencies and ensure compliance. Formal enforcement actions are generally more severe and result in an order issued by the Commissioner. Banks have a statutory right of appeal from formal enforcement actions to which they have not agreed.
A. Informal Enforcement Actions
Board Resolutions: A Board Resolution is a statement adopted by the board of directors of a bank that specifies corrective actions the board of directors will take. It is issued either on management's own volition or at the request of the Department. Board Resolutions are accepted from banks that exhibit only modest regulatory concerns.
Memorandum of Understanding: A Memorandum of Understanding is an agreement between a bank and the Commissioner that sets forth specific corrective actions to be undertaken by the board of directors of a bank. This action is normally pursued with banks where management does not pose a significant regulatory concern, and where the Department believes management has the ability and the willingness to correct noted deficiencies. A Memorandum of Understanding is an agreement within the meaning of Texas Finance Code (TFC) Sections 31.002(a)(29)(C) and 35.002(a)(5). Therefore, violation of a Memorandum of Understanding is grounds for issuance of a Cease and Desist Order, and, if other conditions are met, a Supervision or Conservatorship Order. A Memorandum of Understanding may occasionally have a different title.
Determination Letter: A Determination Letter is a warning issued pursuant to Section 35.001 of the TFC that the practices or condition of a bank need immediate attention to avoid the issuance of an enforcement order under the TFC. A Determination Letter includes a listing of the requirements to abate the Commissioner's determination. A Determination Letter is normally used in a bank where problems are of a serious nature, but the Commissioner believes that a more formal enforcement action may not be necessary to achieve correction.
B. Formal Enforcement Actions
Written Agreement: A Written Agreement between a bank and the Commissioner sets forth specific corrective actions to be undertaken by the board of directors of a bank and/or bank holding company. A Written Agreement is given a Commissioner's Order number. A Written Agreement is usually issued in conjunction with the Federal Reserve Bank of Dallas (Federal Reserve). The Commissioner will join with a federal agency in issuing a Written Agreement only after making the necessary findings to establish the action as a Cease and Desist Order under TFC Sections 35.002, 201.009, and 202.005. Therefore, the Commissioner may publicize a Written Agreement pursuant to Section 35.012. Written Agreements entered into with the Federal Reserve are public under federal law. The Commissioner's decision to issue a joint Written Agreement with the Federal Reserve includes a conclusion that effective enforcement of such a Written Agreement will be enhanced by its publication.
Cease and Desist Order: A Cease and Desist Order is issued pursuant to Section 35.002 of the TFC, demanding that a current or former officer, employee, or director of a state bank, or the bank itself discontinue violations and/or unsafe and unsound banking practices, and take certain affirmative action as may be necessary to correct the conditions resulting from such violations or practices. A Cease and Desist Order is deemed necessary and appropriate for serious violations and unsafe practices. Management of a bank subject to such an order would normally have demonstrated a disregard for safe and sound banking practices and/or the lack of willingness or ability to correct deficiencies on their own. If a bank agrees to enter into such an order, the order is called a Consent Order. The Commissioner may publish a final Cease and Desist Order or Consent Order pursuant to TFC Section 35.012. Cease and Desist Orders or Consent Orders entered into with the Federal Deposit Insurance Corporation (FDIC) are public under federal law. Therefore, the Commissioner will join with a federal agency in issuing a joint Cease and Desist Order or Consent Order only after making the findings required by TFC Section 35.012.
Order of Removal or Prohibition: A Removal or Prohibition Order is issued pursuant to Section 35.003 of the TFC if the Commissioner finds that a present or former officer, director, employee, controlling shareholder, or other person participating in the affairs of a state bank has committed or participated in violations of law or agreements, and/or unsafe and unsound banking practices, or made false entries, which caused certain effects, and which were done in other than an inadvertent or unintentional manner. Such orders have the effect of removing a person from office or employment or prohibiting a person from office, employment, or any further participation in the affairs of a state bank or any other entity chartered, registered, permitted, or licensed by the Commissioner. The Commissioner must publish all final Removal and Prohibition Orders.
Pursuant to Section 31.105(c-2) of the TFC, if an officer, director, employee, controlling shareholder, or other person participating in the affairs of a state bank refuses to comply with a subpoena issued under Section 31.105, the Commissioner may issue an order on an emergency basis removing the person from the person's position and prohibiting the person from participating in the affairs of the state bank or any other entity chartered, registered, permitted, or licensed by the Commissioner until the person complies with the subpoena.
Order of Supervision: Pursuant to Section 35.101 of the TFC, upon determining that a bank is in hazardous condition as defined by TFC Section 31.002(a)(29), the Commissioner may issue an Order of Supervision without prior notice to appoint an individual as a supervisor of the bank. Supervision is generally used in situations where the Commissioner has little confidence in the ability or willingness of the management of the bank to follow safe and sound banking practices. The authority of a supervisor, (enumerated under TFC Section 35.106), includes acting as the Commissioner's on-site observer and agent to assure, through approval authority and/or moral suasion, that the bank is operated properly and in accordance with law and the enforcement action.
Order of Conservatorship: A Order of Conservatorship may be issued by the Commissioner pursuant to Section 35.102 of the TFC when it is determined that a bank is in hazardous condition and immediate and irreparable harm is threatened to the bank, its depositors, creditors or shareholders, or the public. Under Section 35.107, the board of directors may not direct or participate in the affairs of the bank during conservatorship. An appointed conservator immediately takes charge of the bank, its property, books and records, and affairs on behalf of and at the direction and control of the Commissioner.
Administrative Penalties: If a bank or person commits applicable violations of law or a Commissioner's order (see Section 35.009 of the TFC), the Commissioner may seek to assess monetary fines or penalties. The bank or person is notified that a hearing will be held to determine whether administrative penalties will be assessed. Unless the violation is of a Commissioner's order, the bank or person will be given an opportunity to correct the action and reduce or avoid the penalty. Section 35.010(b) of the TFC sets out factors the Commissioner must consider when setting the penalty and Section 35.010(c) sets out minimum and maximum penalty amounts.
Procedure for Implementing Enforcement Actions
Board Resolutions, Memorandums of Understanding and Determination Letters are normally handled through written correspondence with the board of directors of a bank. Nevertheless, they may require a special meeting of the board of directors. Other enforcement actions usually require a special meeting of the directorate of the bank and generally such meetings are conducted by senior Department officials, including a member of the legal staff, at the Austin headquarters office. If an enforcement action is a joint action with a federal agency, the board meeting may occur at the federal agency's regional office.
Follow-up by examining personnel on enforcement actions is conducted in accordance with the Department's examination priorities unless variance from policy is deemed necessary. A bank that is placed under Supervision or Conservatorship will have the appointed supervisor or conservator assist in monitoring compliance with enforcement orders.
September 7, 2023
| TO: | All Institutions Regulated by the Texas Department of Banking |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Request for Reconsideration of Examination Finding (REF) |
Purpose
It is the policy of the Department to provide sound supervision of the entities it regulates through fair and unbiased examinations and monitoring. In the event that a material disagreement arises regarding an examination finding or rating, the regulated entity may submit a request for the Reconsideration of an Examination Finding (REF). This Supervisory Memorandum addresses the proper process for submitting a REF to the Department.
Reconsideration of Examination Finding During an Examination
If a material disagreement between Department examiners and an entity under examination arises regarding an examination finding, the entity should first attempt to resolve the dispute with the Examiner-In-Charge (EIC) of the examination. Entities are encouraged to discuss any conflicting issues during an examination with the EIC and to work closely with the EIC to ensure that all available information is received and fully explained.
If a satisfactory resolution is not reached, the entity may further pursue its concerns with the EIC's supervisor. For examinations conducted by the Bank and Trust Supervision Division, the entity may contact the Regional Director, Chief Trust Examiner, Chief IT Security Examiner or the Director of Bank and Trust Supervision. For examinations conducted by the Non-Depository Supervision Division, the Director of Non-Depository Supervision may be contacted.
Request for Reconsideration of Report of Examination Finding
If, after the Report of Examination is received and an entity continues to have an unresolved objection with one or more finding(s) or rating(s) in the Report of Examination, the entity may file a written request for review of the matter with the Banking Commissioner. The written request should be submitted through U.S. mail to the Texas Department of Banking Ombudsman at 2601 N. Lamar Blvd., Austin, Texas 78705. A request for a REF should be submitted within 30 days after receipt of a Report of Examination and should include a full description of the matter in dispute, along with supporting documentation.
The objection(s) will be investigated by the Ombudsman who is appointed by the Commissioner. The Ombudsman may request additional information from the entity requesting the REF and obtain documents from the examining division. The Ombudsman will perform an independent analysis and makes a recommendation to the Commissioner regarding the objection. The Commissioner will issue a final determination in the form of a written response to the entity. The supervised entity requesting the REF has no right to a hearing or further appeal after the Commissioner has rendered a decision.
As a general rule, supervisory decisions and actions continue in effect during this process. However, new supervisory decisions or actions based on examination findings associated with a REF may be suspended until the review is completed and the Commissioner makes a final determination.
Withdrawal of Request
A REF may be withdrawn by an entity at any time during the review process by submitting a written notice to the Ombudsman.
March 6, 2015 (rev.)
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Policies Regarding Investment Securities 1 |
Background
With the passage of the Dodd-Frank Wall Street Reform and Consumer Protection Act of 2010 (Dodd-Frank Act), regulatory changes have been implemented regarding the permissibility of certain investment activities. The Office of the Comptroller of the Currency (OCC) adopted a final rule and related guidance which removes references to external credit ratings and clarifies regulatory expectations regarding assessing a security's creditworthiness and ongoing due diligence consistent with requirements in the Dodd-Frank Act. Under part 362 of the Federal Deposit Insurance Corporation's regulations, insured state banks generally are prohibited from engaging in an investment activity that is not permissible for a national bank under OCC regulations. Under the Federal Reserve Act (12 USC 335) and the Federal Reserve's Regulation H (12 CFR 208.21), state member banks may purchase, sell, underwrite, or hold securities and stock as national banks under the National Banking Act. State member and nonmember banks must comply with the OCC regulations when investing in securities.
This Supervisory Memorandum reinforces the Department's endorsement and adoption of federal banking agencies' policies relating to the investment security standards and activities, consistent with the Dodd-Frank Act. This Memorandum also establishes the Department's policy regarding the classification and appraisal of municipal bonds.
Policy
The investment guidance issued by the OCC and affirmed by the FDIC in Financial Institution Letter FIL-48-2012 and the Federal Reserve Board in SR letter 12-15, amends the definition of "investment grade" by removing references to external credit ratings and requires banks to make assessments of a security's creditworthiness to determine if it is "investment grade." 2 A security meets the "investment grade" regulatory standard for credit quality if the security has (1) low risk of default by the obligor, and (2) the full and timely repayment of principal and interest is expected over the life of the investment. Banks may continue to take into account external credit ratings and assessments as a valuable source of information; however, banks are expected to supplement these ratings with due diligence processes which consider the interest rate, credit, liquidity, price, size, complexity, and other risks presented by the investments. Additionally, ongoing analysis of the investment portfolio should continue to be performed to ensure that investments are appropriate for the bank's risk profile.
The Department concurs that state-chartered banks must comply with the federal regulations and guidance related to investment securities. The Department's policy regarding investment in municipal bonds, however, considers that if a bond is rated, it should be in the top four rating categories provided by Nationally Recognized Statistical Rating Organizations in order to be considered "investment grade." Per the federal guidance, independent credit analysis should still be performed by the bank on purchases of municipal revenue bonds. While it is not mandatory that general obligation bonds meeting the criteria for Type I bonds be subject to detailed credit analysis, an adequate level of credit review is still expected as a safe and sound banking practice. If a bond is not rated, the bank's supplemental analysis should validate why the bond is considered to be of "investment grade." Banks must perform both pre-acquisition and ongoing periodic post-acquisition analysis of securities held to support the "investment grade" nature of the bonds held.
The Department also concurs with the Uniform Agreement on the Classification and Appraisal of Securities Held by Financial Institutions which was updated by federal regulatory authorities on October 29, 2013.
October 1, 2020 (rev.)
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Policy for Other Real Estate Owned (OREO) 1 |
OVERVIEW
This policy statement interprets the state statutes and rules governing other real estate and defines the Department's classification policy for OREO for state-chartered banks.
Section 34.003 of the Texas Finance Code (TFC) authorizes a state bank to hold real estate other than its banking premises in limited circumstances. Section 34.004 of the TFC further permits a state bank to hold nonparticipating royalty interests as personal property in specific instances. Title 7, Section 12.91 of the Texas Administrative Code (7 TAC §12.91) defines other real estate; describes the limited circumstances under which it can be lawfully acquired by a bank; outlines the appraisal/evaluation requirements; establishes a procedure whereby additional expenditures may be made; defines a maximum holding period for each parcel; and outlines the minimum criteria for disposition efforts by a bank.
ACCOUNTING FOR THE ACQUISITION OF OREO
Initial Booking
Under 7 TAC §12.91 OREO must be accounted for in accordance with regulatory accounting principles, 2 defined in the TFC as generally accepted accounting principles (GAAP) as modified by rules adopted under the TFC or an applicable federal statute or regulation.
Each parcel of OREO should be recorded at the fair value less costs to sell the property, which becomes the "cost" of the foreclosed real estate. If the fair value (less the estimated costs to sell) exceeds the recorded amount of the loan, the excess should be reported as a recovery of a previous charge-off on the loan or in current earnings, as applicable. 3 If the recorded value of the loan exceeds the fair value of the foreclosed property minus estimated selling costs upon initial booking, the deficiency is a loss which should be charged to the Allowance for Loan and Lease Losses. 4 Further accounting guidance for OREO can be found in the Federal Financial Institutions Examination Council (FFIEC) Call Report Instructions, which require that OREO be accounted for in accordance with GAAP.
The recorded value is the outstanding principal balance of the loan plus any booked accrued and unpaid interest (not to exceed 90 days) plus any unamortized premium and loan acquisition costs, less previous write-downs, finance charges, and any unamortized discount. Direct costs incurred by the bank in a foreclosure, such as legal fees, should be expensed when they are incurred.
Accounting for Other Liens
In accordance with FASB ASC Topic 360, Property, Plant, and Equipment (formerly FASB 144, Accounting for the Impairment of Disposal of Long-Lived Assets), the amount of any senior debt (principal and accrued interest) to which the property is subject (even if not formally assumed by the bank) should be reported as a liability at the time of foreclosure. The carrying amount of the asset would, therefore, be increased by such amount; however, the resulting carrying amount cannot exceed the market value, net of estimated sales costs, of the property. Any subsequent payments of principal should reduce the liability. Interest that accrues after foreclosure should be recognized as interest expense and added to the liability account balance if left unpaid.
Subsequent Costs
Ongoing expenses not associated with acquiring clear title to the property (i.e., taxes, hazard insurance, utilities, etc.) should be expensed as incurred. Costs incurred to protect a bank's investment in OREO which is improved or under construction, and necessary to place a property in a saleable condition, may be capitalized in accordance with GAAP. Additional investments which alter the current status or intended use of the property or made for the purpose of speculating in real estate are not allowed under the law.
APPRAISALS AND EVALUATIONS
Appraisals and Evaluations at Acquisition
As provided in 7 TAC §12.91(d), when OREO is acquired, a state bank must substantiate the market value by obtaining an appraisal within 90 days of the date of the property's acquisition by the bank, unless extended by the banking commissioner. An evaluation may be substituted for an appraisal if the recorded book value of the OREO is $500,000 or less.
If the bank has already obtained an appraisal or appropriate evaluation within the year prior to foreclosure, as provided in 7 TAC §12.91(d)(2), then a new valuation is not yet required.
Subsequent Appraisal and Evaluation Requirements
An evaluation of the value of OREO must be made at least once a year. An appraisal is required at least once every three years unless extended by the banking commissioner. An evaluation may be substituted for an appraisal if the recorded book value of OREO is $500,000 or less. The one-year period is measured from the date of the last appraisal or evaluation.
If any subsequent appraisal or evaluation indicates a reduction in the value of a property below the current book value, FASB ASC 360 requires the bank to recognize the deficiency as a valuation allowance against the asset, which is created through a charge to expense. For reporting purposes, the reserve account should be netted against the book value of the OREO and is not considered as part of the bank's capital structure. The valuation allowance should thereafter be increased or decreased (but not below zero) through charges or credits to expense for changes in the asset's value or estimated selling costs. In no event, however, should the carrying value of the property be increased to an amount greater than the original book value at the time of acquisition or transfer to the other real estate category.
Maintenance of a general reserve for losses on the sale of OREO and write-downs below appraised value are not consistent with generally accepted accounting principles. Write-downs below appraised value must be supported by documentation that indicates that the write-down was appropriate.
Obtaining an Appraisal Extension
The banking commissioner may extend the deadline for when an appraisal is required on OREO property per 7 TAC §12.91(d)(1) and (3). Requests for an extension of the deadline for obtaining an appraisal within 90 days of acquisition of OREO or the deadline to obtain an appraisal of OREO property every three years must be submitted to the commissioner in writing. Extension requests must include information necessary to support the reason(s) for the extension. The required form for submitting an extension request, “Application to Extend Appraisal Deadline,” is available under the Applications & Forms section of the Department’s website.
Decisions to approve or deny requests for the extension of a deadline to obtain an appraisal will be made on a case-by-case basis after considering all relevant factors of the transaction. Reasons for granting an extension vary but may include a pending written sales agreement that is expected to close within the next 90 days.
HOLDING PERIOD FOR OREO
Holding Period Limit
Texas statutes require that a state bank dispose of OREO within five years from the date the real property:
• is originally acquired or transferred to that asset category;
• ceases to be used as a bank facility; or
• ceases to be considered future expansion property as a bank facility as provided by Section 34.002(b) of the TFC.
When a state bank acquires OREO as the result of a merger with or an acquisition of another institution, the holding period of the newly acquired OREO commences on the date of merger or acquisition. If an entity converts to a state-charter, the OREO property held by the entity at the time of conversion will be considered acquired or transferred to OREO as of the conversion date.
The banking commissioner may grant an extension of time for disposing of an OREO property if, in the commissioner's opinion, the bank has made a good faith effort to dispose of the property, or if the commissioner determines that disposal of the property within the initial five-year period would be detrimental to the bank. Should the extension request be denied, failure to dispose of the property may result in citing a violation of 7 TAC §12.91 at the next examination. Examining personnel will review the bank's efforts to dispose of each property and evaluate compliance with the regulation. Continued noncompliance and/or absence of good faith efforts to dispose of the property may result in the issuance of an enforcement action to effect correction.
Holding Period Extensions
All requests for extensions of holding periods must be in writing. The required form for submitting an extension request, "Extension on Holding Period for OREO," is available under the Applications & Forms section of the Department's website.
Extensions for future expansion will be handled on a case-by-case basis. Primary factors that are considered by the Department in evaluating compliance with the law and in deciding whether to approve requests for extensions of holding periods include the following:
• Carrying value of the property in relation to current market value, asking price, and purchase offers received;
• Length of time the property has been held and reason(s) why it has not been sold;
• Income and expenses associated with ownership and maintenance of the property for: (i) all prior years; (ii) the current year; and (iii) an estimate of next two years; and,
• Potential or known contingent liabilities (e.g., environmental concerns, litigation, etc.) relative to the holding of the property.
Extensions for holding property, other than future expansion, are not normally granted if the extended time exceeds ten years from the original date of acquisition, or the date a former bank facility was reclassified as OREO.
Holding Non-participating Royalty Interest Beyond Disposal Period
A non-participating royalty is an interest in the minerals that is non-possessory and does not entitle the owner to produce the minerals, join in a lease of the mineral estate to which the royalty is appurtenant, or share in bonuses or delay rentals that may be paid under the lease, but merely entitles the owner to a share of the production under the lease free of exploration and production expenses.
If acquired for the purpose of avoiding or minimizing a loss on a loan or investment previously made in good faith, under certain circumstances a bank may retain a limited interest in OREO in the form of a non-participating royalty interest, subject to Section 34.004 of the TFC. The commissioner may order the bank to dispose of the interest if it is determined at any time that continued ownership is detrimental to the bank.
In order to own and retain any non-participating royalty interest beyond the disposal period for OREO, a written request must be submitted to the commissioner. The request form, "Application to Hold Non-Participating Royalty Interest," is available on the Applications & Forms section of the Department's website. The written request must be accompanied by a copy of the instrument creating the royalty. Upon receiving approval by the Department, a letter application to the FDIC must be submitted requesting permission to hold the reclassified property at the bank level, pursuant to 12 CFR §362.3(b)(2)(i).
DISPOSAL OF OREO
Minimum Documentation Requirements
Under 7 TAC §12.91(g), banks are expected to maintain documentation showing compliance with the regulation and good faith efforts to dispose of each parcel of OREO. Required minimum documentation includes:
• Specific action plans for disposal of each parcel of OREO showing review and approval by the bank's board of directors or a designated committee thereof. Such action plans and reviews should be recorded in the official records of the board or committee meetings;
• Listing agreements executed with real estate agents/brokers detailing the asking price and terms of sale. If a property is not listed, adequate documentation showing the bank's own marketing efforts must be maintained;
• Documented reasonableness of the asking price relative to the appraised market value of the property;
• Records of all verbal and/or written inquiries and offers received for each property;
• Decisions made and actions taken by the board, or designated committee, on all verbal or written offers received; and
• Files of all advertising media employed, e.g., signs, publications, and broadcast media.
Accounting for Disposition of OREO
FASB issued Accounting Standards Update (ASU) 2014-09 in May of 2014 which created ASC Topic 606, Revenue from Contracts with Customers, and amended ASC Topic 610, Other Income. 5 Per ASU 2014-09, sales of OREO should be accounted for in accordance with ASC Subtopic 610-20 Other Income – Gains and Losses from the Derecognition of Nonfinancial Assets. 6
Bank Financing of OREO Purchases
It is not uncommon for a bank to provide financing upon sale of OREO to facilitate the orderly liquidation of such assets. The receivable resulting from the sale of the OREO should be reported as a loan if the transaction meets five contract criteria in ASC Topic 606. Any dispositions which do not initially qualify for sales treatment should continue to be reported as OREO and monitored for subsequent reclassification to a sale when the minimum criteria are met. Payments received from the borrower are reported as a liability until the requirements in ASC Topic 606 are met. In addition, if the transaction price is less than the carrying amount of the OREO, the bank should consider whether this indicates a decline in fair value of the OREO that should be recognized as a valuation allowance, or as an increase in an existing valuation allowance. For additional guidance, refer to ASC Subtopic 610-20 and ASC Topic 606.
When a financed property remains OREO for reporting purposes, it is not subject to the disposal efforts and holding period limits incorporated in law and this policy. Also, Section 34.201(a)(15) of the TFC specifically excludes the portion of a purchase money mortgage taken by a bank in consideration for the sale of OREO owned by the bank from the legal lending limit, if the sale was in the bank's best interest.
Exchange, Acceptance or Additional Purchases
As provided in 7 TAC §12.91(c)(4), a state bank may exchange or acquire real estate or personal property in order to avoid or minimize loss potential on OREO with the prior written approval of the banking commissioner. Alternate or additional real estate so acquired should be accounted for on the bank's books as OREO, and the initial holding period for such properties will be measured from the date legal title to the original OREO was first acquired by the bank. Disposal of personal property should be within 90 days of acquisition.
Criteria for Exchanging or Acquiring Additional OREO
The commissioner's decision to approve or deny requests for the exchange or acquisition of real estate will be made after considering all relevant factors of the transaction, particularly the following:
• Has the bank demonstrated good faith efforts to dispose of the original OREO?
• Has the bank reduced its loss exposure as evidenced by current market value appraisals of the properties involved?
• Does the bank have specific plans to market the newly acquired property?
• What is the amount of cash to be received by the bank in connection with a transaction where the bank is accepting an alternate parcel of real estate as partial consideration in the sale of existing OREO?
• Will the nature of the original OREO be changed?
• What is the bank's aggregate investment in the existing OREO plus the property to be acquired in relation to equity capital?
Transfer of OREO to a Bank Subsidiary
7 TAC 12.91 (h)(4) provides that a bank may dispose of other real estate owned by: (1) transferring the property to a majority-owned subsidiary; and (2) complying with FDIC regulation 12 CFR §362.4(b)(5)(i). In the event that the bank does not already have a majority-owned subsidiary for this purpose, the bank must submit a notice to the Department pursuant to Section 34.103(e) of the TFC. The instructions for submitting the required subsidiary notice to the Department, “Notice to Applicants – Subsidiary Notice Filings,” is available under the Applications & Forms section of the Department’s website.
If a bank (and its subsidiary) meet the core eligibility requirements of 12 CFR §362.4(c), it can transfer OREO to the qualifying subsidiary under 12 CFR §362.4(b)(5)(i) after filing notice with the FDIC and that notice is processed without objection.
Transfer of OREO to an Affiliate
7 TAC 12.91(h) (5) provides that a bank may dispose of real estate by transferring the real estate for market value to an affiliate. This is subject to Section 33.109 of the TFC and applicable federal law, including 12 U.S.C. §§371c, 371c-1, and 1828(j) relating to transactions with affiliates. Section 33.109 of the TFC requires that a bank may not directly or indirectly sell or lease an asset of the bank to an officer, director, or principal shareholder of the bank or of an affiliate of the bank without the prior approval of a disinterested majority of the board. If a disinterested majority cannot be obtained, the prior written approval of the banking commissioner is required.
A bank may also dividend in kind the real property to an up-stream subsidiary or affiliate at the market value of the asset on the date of the dividend.
According to 12 C.F.R § 225.22 (d), the Federal Reserve Board may, upon request, permit a bank holding company or a nonbank subsidiary of the bank holding company that receives the real estate through sale, transfer, or dividend in kind from the bank, to hold the property for a maximum of 10 years. The holding period requirement is based upon the date that the property was acquired by the bank or the date a former bank facility became OREO.
CLASSIFICATION STANDARDS
The Department evaluates OREO in the same manner as any other bank-owned asset, utilizing the same criteria for assessing quality and propriety. As warranted, adverse criticism is assigned in a manner consistent with the uniform classification standards used by state and federal bank regulatory agencies.
Income producing properties may be excluded from classification provided the annual net cash flow from the property yields a market rate of return on the entire book amount. "Net cash flow" is defined by GAAP as gross cash receipts less the cost of insurance, taxes, management fees, and other operating costs. For purposes of the classification treatment outlined below, the market rate of return must equal or exceed the average yield on real estate loans as reflected in the bank's most recent federal reports of condition and income plus 100 basis points. If book value is materially less than the market value of the property due to previous unsubstantiated write downs, for classification purposes the rate of return is calculated using the market value of the asset.
Suggested classification treatments are shown below and assume that the examiner has no material reservations with the validity of the appraisal or its assumptions. In the case of income producing properties, the assumption is also made that there are no significant reservations about the quality and continued viability of the future cash flow stream of the property. However, if an examiner has reasonable cause to question the appraisal, its assumptions, or the future cash flow stream, more severe classifications than those shown may be assigned.
Income Producing Properties
Pass - Market rate of return equals or exceeds the average yield of the bank's real estate loans plus 100 basis points.
Substandard - Market rate of return does not equal or exceed the average yield of the bank's real estate loans plus 100 basis points.
Doubtful - N.A. (this classification is generally not appropriate).
Loss - Excess of book value over current appraised value.
Non-income Producing Properties
Substandard - Current appraised value.
Doubtful - N.A. (this classification is generally not appropriate).
Loss - Excess of book value over current appraised value.
April 3, 2014 (rev.)
| TO: | All State-Chartered Banks and Trust Companies; |
| FROM: | Charles G. Cooper, Commissioner |
| SUBJECT: | Business Plans and Strategic Planning1 |
Background
This Supervisory Memorandum reinforces the Department's position on the importance of business plans and strategic planning for de novo banks and trust companies as well as for those institutions that have already been established. Clearly defined business plans and annual strategic planning are essential for the continuing success of an institution. This policy provides an overview of the components of a business plan and the strategic planning process, and addresses when a written business or strategic plan is required by the Department.
The Department considers a business plan to be primarily an externally focused document that provides detailed information on the proposed development of an organization. A strategic plan is an ongoing and internally focused plan which guides an organization's board of directors and employees on achieving the goals and objectives of the entity while adhering to its overarching mission.
Business Plans and Strategic Planning
Business Plans
The Department of Banking believes that a clearly defined business plan is an important ingredient to the initial success of any commercial enterprise. A business plan serves several purposes, specifically it: assists organizers and the board of directors to focus on their overall mission and goals; provides a means for the board of directors to communicate their objectives and strategies to management and staff; provides guidance to management in setting specific targets and business objectives; serves as a reference point for measuring performance; and assists potential investors and regulators in evaluating the organization's prospects.
A business plan is considered especially important when a new bank or trust company is being organized or when significant changes are contemplated or occurring. A detailed and comprehensive business plan should address the following:
• Marketing Plan
• planned products and services;
• market analysis;
• economic analysis; and
• competitive analysis;
• Management Plan
• board of directors, senior executive officers and committee structure
• Operations Plan
• risk management
• policies, procedures and internal controls;
• internal and external audit;
• compliance management;
• use of technology and electronic processing systems; and
• use of vendors;
• Financial Objectives and Projections; and
• Monitoring and Revising the Plan.
The plan must reflect sound business principals and demonstrate a realistic assessment of risk given the economic and competitive conditions in the market to be served. A strong business plan can be achieved with in-depth planning by the institution's organizers and management.
Business plans submitted with corporate applications should provide at least three years' operating projections and should contain sufficient information to demonstrate a reasonable likelihood of success. The plan should identify the proposed markets to be served, products and services to be offered, projected profitability and capital adequacy, information technology infrastructure requirements, and managerial resources and capabilities. Pro-forma statements should include a detailed breakdown of all assumptions utilized in preparation of the data.
Generally, the business plan guidelines and financial projections and balance sheet format included in the Interagency Charter and Federal Deposit Insurance Application will be accepted in transactions involving a bank. Trust applicants should utilize the Proforma Financial Statements form found on the Department's website under the Trust Company section of the Forms page to support projections.
Strategic Planning
An on-going strategic planning process is important to all institutions for setting direction, goals, and objectives and establishing strategies for reaching goals and objectives. At the core of sound strategic planning are four basic components which should be addressed:
1. Where are we now?
2. Where do we want to be?
3. How do we get there?
4. How do we measure our progress?
Sound strategic decisions are essential for an institution to compete and be profitable. Well executed strategic planning provides management with the tools needed to confirm goals and assess progress toward a desired outcome (such as asset and capital growth), evaluate what is effective and what is not, and adjust strategies to improve performance especially when adding new business lines or products. An effective strategic planning process is dynamic and allows management to adapt to changing market, business and technology needs. Thus, the Department strongly recommends that all banks and trust companies engage in regular, formal strategic planning sessions on at least an annual basis as a means of ensuring that the institution's actions are in alignment with its mission and goals.
Applications Requiring a Business or Strategic Plan
Business Plans
A business plan is critical to the Department's decision of whether to approve the organizer's charter proposal. A well-defined business plan including financial projections, analysis of risk, and planned risk management systems and controls enables chartering authorities to more effectively gauge the probability of success of a proposed entity. Business plans are required for certain types of corporate applications submitted to the Department, and may be requested with other types of applications.
A business plan is required by the Department on all new charters, including:
• De novo applications; or
• Applications to change from exempt to nonexempt status or vice versa for a trust company.
If an institution encounters difficulties, a business plan provides a means for regulators and boards of directors to coordinate an effective improvement program. Thus, a business plan also may be required as part of administrative actions or enforcement orders involving troubled institutions.
Strategic Plan
Depending on the significance of the proposed change for the entity, the Department may also require a strategic plan be submitted with applications involving:
• Bank/Trust Company conversions;
• New branches;
• Change of control;
• Change of home office:
• Mergers; or
• Purchase and assumption transactions.
March 1, 2017
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Bank-Owned Life Insurance (BOLI) |
PURPOSE
This Texas Department of Banking (the Department) supervisory memorandum establishes guidelines and best practices1 for Texas state banks that purchase or hold life insurance products. It is designed to aid state banks in making informed decisions consistent with safe and sound banking practices as they relate to bank-owned life insurance (BOLI).
As set out in the guidelines of this memorandum, a bank’s management and board should acquire a thorough understanding of the nature and characteristics of any BOLI product before committing bank resources. A central theme to these guidelines is that BOLI should only be regarded as a method to control risks and not as an investment substitute or a method to fund insider incentives.
This revision and replacement of former Policy Memorandum 1010 (February 24, 2004) is similar to the interagency statement issued jointly by the federal bank regulatory agencies on December 7, 2004, see, e.g., FDIC Financial Institution Letter (FIL) 127-2004, Interagency Statement on the Purchase and Risk Management of Life Insurance.
IMPLEMENTATION
This memorandum provides for a bank management’s initial and ongoing assessment of its ownership of life insurance products. Appendixes A and B should be completed by a state bank before its initial purchase of life insurance on employees or directors, and annually thereafter.
BACKGROUND
Most banks find their guidance regarding BOLI purchases from the federal Interagency Statement on the Purchase and Risk Management of Life Insurance (e.g., FIL 127-2004 (FDIC) or SR 04-19 (FRB)). The Interagency Statement also addresses the risk weighting of BOLI assets. With the adoption of Basel III and the passage of Dodd Frank, banks may no longer rely solely on the major rating agencies to determine the risk weighting of their BOLI assets. The purpose of the next section of the document, Types of BOLI, is to explain the differences in the products and identify how to assign risk weighting to BOLI assets under the New Basel III Capital Rules.
TYPES OF BOLI
The different types of products available to banks interested in purchasing BOLI include General Account, Separate Account and Hybrid Separate Account products, and each is subject to differences is how risk weighting is assigned.
General Account
General Account BOLI assumes the general assets of the insurance company issuing the BOLI policy will support the policy’s cash values. Accordingly, the credit risk of the portfolio is borne by the carrier and typically a minimum interest crediting rate is provided. General Account BOLI is recognized at a risk weighting at 100%.
General Account BOLI policies invest a significant portion in fixed income investments such as corporate bonds, government bonds, private placements, mortgages, asset backed securities, etc., with a smaller percentage invested in equities.
The advantage of a well-diversified traditional General Account product is that it incorporates a long-term investment strategy that is actively managed, well-diversified, and contains a long-term investment horizon. The key disadvantage is that the assets backing the BOLI policyholder are generally subject to claims from other creditors of the insurance company.
Separate Account
In a Separate Account, the policy cash values are backed by assets segregated from the general assets of the insurance company, and are not subject to claims from other creditors of the insurance company. Under this approach the insurance company segregates the holdings from their general account into bank eligible investments managed by fund managers. The bank selects the investment style but does not control the investments. Investments must be bank qualified. Assets are segregated by state law and protected from general creditors. Fund managers provide detailed reporting of the assets within the portfolio. The crediting rate is determined by the insurance company using a yield-to-worst ratio. However there is no guaranteed minimum crediting rate. A stable value insurance rider can be purchased in order to smooth out the mark to market performance and provide downside protection. Cash surrender value fluctuates depending upon the returns from the underlying investments supporting the policies. The cash value potentially could be zero.
Separate Account BOLI under the New Basel III Capital Rules is considered to be an equity exposure to the underlying investment fund(s). There are three approaches for determining the risk weighting of Separate Account assets under the new rule. In the past, some Separate Account products have enjoyed a minimum risk weighting of 20% following one of these three approaches. This may or may not be the case under the New Basel III Capital Rules. The risk weighting will depend largely on the approach selected as well as pertinent terms of the underlying investment funds.
Hybrid Separate Account
In a Hybrid Separate Account policy, like Separate Accounts, the policy cash values are backed by assets segregated from the general assets of the insurance company, and are not subject to claims from other creditors of the insurance company. Under the Hybrid Separate Account structure, policy owners have the choice between investing in the Separate Account options offered within the product. One of those options is usually an investment portfolio that is similar to or a clone of the insurance company’s General Account. There may be a minimum interest rate that is credited to guarantee against investment losses. Typically, there are restrictions on how and when assets can be moved from the “General Account” portfolio to one or more of the other Separate Account portfolios.
Under the New Basel III Capital Rules, Hybrid Separate Account products may be treated as either General Account or Separate Account, if the Hybrid account meets the definition of a Separate Account for risk weighting purposes. It is the responsibility of the bank to determine the risk weighting of its Hybrid portfolio. In making this determination, the bank may wish to contact the insurance company offering the Hybrid Account to obtain its position as to whether the insurer’s Hybrid Account meets the definition of a Separate Account. If the Hybrid Account meets the definition of a Separate Account, then the bank can elect to follow either a more conservative or more aggressive risk weighting approach. If the Hybrid Account does not meet the definition of a Separate Account, then the bank should risk weight its assets at 100% like a General Account.
To qualify for a Separate Account, the following conditions have to be met:
1. The account must be legally recognized under applicable law.
2. The assets in the account must be insulated from the general liabilities of the insurance company under applicable law and protected from the insurance company’s general creditors in the event of the insurer’s solvency
3. The insurance company must invest the fund within the account as directed by the contract holder in the investment alternatives designated or in accordance with specific investment objectives or policies.
4. All investment performance, net of fees and assessments, must be passed through to the contract holder, provided that contracts may specify conditions under which there may be a minimum guarantee but not a ceiling.
It is unlikely that Hybrid Separate Account policies will meet the definition of a Separate Account outlined in point number four above. As a result, it will be difficult for banks to take advantage of the lower risk weighting available with such a product due to the classification rules.
LEGAL AUTHORITY
The purchase of life insurance will be subject to supervisory review and must be consistent with safe and sound banking practices. Generally, Texas state banks may purchase BOLI as an exercise of incidental powers under Texas Finance Code § 32.001(b). The Department views the following purchases of life insurance to be incidental to banking:
• Key-person insurance;
• Life insurance on borrowers (this memorandum does not address disability insurance or debt waiver coverage);
• Life insurance purchased in direct connection with and to support the funding needs of employee2 compensation and benefit plans; and
• Insurance taken as security for loans.
In addition, the Department may approve other uses of BOLI on a case-by-case basis subject to a finding that the purchases address a legitimate need of the bank.3 Generally, life insurance may not be purchased as an investment alternative to generate funds for a bank’s normal operations, for speculation, or for primarily providing estate-planning benefits for bank insiders such as an executive officer, director, or principal shareholder of the bank.
Texas law requires an employer to have an insurable interest in an employee’s life before purchasing life insurance beneficial to the employer on an employee. Employment alone does not give an employer an insurable interest. State banks considering life insurance purchases are encouraged to review Texas Insurance Code Chapter 1103 Subchapters A and B, as well as Texas court cases on insurable interests.
SUPERVISORY POLICY
A comprehensive understanding of the nature, characteristics and risks of a BOLI product should be achieved by the board and management before bank resources are committed. This can be partially accomplished by ensuring that all BOLI transactions meet the guidelines set out in this memorandum. The bank may also wish to consult with the Texas Department of Insurance regarding unusual or difficult to understand terms and conditions of a contemplated insurance product.
Cash value life insurance is a long-term, illiquid, non-amortizing asset that may be an unsecured obligation of the insurance carrier if funds are invested in a General Account. Bank transactions of this nature are subject to credit, liquidity, and interest rate risks. Additionally, banks should be aware of several other risks, including: transaction; tax; compliance; and price risks. Therefore, BOLI should only be regarded as a method to manage risks rather than an investment substitute or a method to fund insider incentives. Banks holding life insurance in a manner inconsistent with safe and sound banking practices may be subject to supervisory actions which could include, but are not limited to, partial surrender or divestiture of affected policies. Thus, bank management and the board should complete a thorough analysis and acquire a comprehensive understanding of the contemplated transaction before purchasing material amounts of BOLI.
A. Pre-Purchase Analysis
The safe and sound use of cash value life insurance depends on effective senior management knowledge and board oversight. Regardless of the bank’s financial capacity and risk profile, the board must understand the role BOLI plays in the overall business strategies of the institution. The board’s role in analyzing and overseeing cash value life insurance should be commensurate with the size, complexity, and risk inherent in the transaction. Although the board may delegate decision-making authority related to the purchase of life insurance to management, the board remains responsible for ensuring that such purchases: (i) are consistent with safe and sound banking practices; (ii) are in compliance with applicable laws and regulations; and (iii) are appropriate for the needs of the bank.
The objective of the pre-purchase analysis is to help ensure that bank management and the board understands the risks, rewards, and unique characteristics of BOLI. In most instances, banks should consider both the best and worst case scenarios and the probability of such occurrences during the pre-purchase analysis. At a minimum, the pre-purchase analysis should consider the following guidelines.
1. Determination of the Need for Insurance
A state bank should determine the need for insurance by identifying the specific risk of loss or obligation against which it is insuring. The existence of a risk of loss or an obligation does not necessarily mean that a bank can purchase or hold an interest in life insurance. For example, a bank may not purchase life insurance on a borrower as a mechanism for recovering obligations that the bank has charged off, or expects to charge off, for reasons other than the borrower’s death. Notably, the purchase of insurance to indemnify a bank against a specific risk does not relieve it from other responsibilities related to managing that risk.
A state bank may purchase life insurance to indemnify itself from the loss of a “key-person” whose contributions are indispensable to the institution. However, a bank should not use key- person life insurance in place of, or to diminish the need for, key-person succession planning. To qualify for the tax benefits of investing in BOLI (e.g., death benefits are non-taxable), insureds in the BOLI plan should all be in the top thirty-five percent of the organization’s compensation structure and have provided written permission to purchase/hold the policy with respect to employees that are not key-persons, a bank should avoid the appearance of taking advantage of lesser paid employees. Regardless, lesser paid employees can benefit from policies purchased on employees in the top thirty-five percent if the gains on those policies are applied to pay for the bank’s overall employee benefit costs such as those related to health or retirement plans. A bank may own life insurance to protect itself against the death of an individual (“key person policies”), or provide a reasonable employee benefit (including deferred compensation). It is also permissible for a state bank to retain a policy on an officer who leaves the bank. An individual who is a principal shareholder of the bank, but holds no office (i.e., not an officer or director) is not entitled to compensation and, therefore, should not be a party to this type of arrangement.
The Department has reviewed the merits regarding the practice of a state bank holding life insurance on directors, officers or employees that are no longer employed or associated with the institution, either because of termination or retirement. As a best practice, a state bank should not purchase BOLI on any employee that does not benefit from the purchase, either directly, through a supplemental life insurance plan such as split-dollar, survivor income or death benefit only plans or from their participation in a group benefit or compensation plan. To obtain favorable tax treatment for a BOLI plan, a state bank must obtain written approval from any employee covered by a BOLI policy before it is purchased. The employee’s written consent should acknowledge and grant permission for the BOLI policy to continue after their employment with the bank has ceased in accordance with Internal Revenue Code (IRC) Section 101(j).
A state bank may protect itself against risk of loss from the death of a borrower if the bank has an insurable interest. Texas law generally recognizes that a lender has an insurable interest in the life of a borrower to the extent of the borrower’s obligation to the lender. This protection may take the form of debt cancellation contracts or the purchase of life insurance policies on borrowers. A lender’s insurable interest may equal the borrower’s obligation plus the cost of insurance and time value of money. Holding life insurance in an amount in excess of the bank’s credit risk of loss may constitute an unsafe and unsound practice. Once a credit is repaid, otherwise satisfied in full, or charged off, the risk of loss is eliminated. Therefore, a state bank should surrender or otherwise dispose of life insurance on individual borrowers under these circumstances. For this reason, the economic consequence of terminating the insurance should be considered in selecting the type of insurance and the structure of the policy. Also, a bank should surrender or otherwise liquidate cash value insurance acquired through debts previously contracted within a short time of obtaining control of the policy, generally within 90 days.
2. Quantifying the Amount of Insurance Needed
A state bank contemplating a BOLI purchase should estimate the size of the obligation or the risk of loss to ensure that the bank is not purchasing an excessive amount of insurance. To calculate such estimates, the bank may include the cost of insurance and the time value of money in determining the amount of insurance needed. These estimates should be based on reasonable financial and actuarial assumptions. In situations where a bank purchases life insurance on a group of employees or a homogenous group of borrowers, it can estimate the size of the obligation or the risk of loss for the group on an aggregate basis. The bank can then compare the aggregate obligation or risk of loss to the aggregate amount of insurance purchased.
3. Vendor Selection
While the vast majority of BOLI purchases are made through vendors, BOLI may sometimes be purchased directly from insurance carriers without using a vendor. Regardless of whether a state bank decides to utilize or not to utilize the services of a vendor, the following items should be considered:
• The bank’s knowledge of BOLI;
• The resources the bank can, and is willing to, spend on servicing and administering the BOLI;
• The vendor’s qualifications; and
• The benefits a vendor may provide.
Depending on the vendor’s role, the vendor’s services can be extensive and critical to successful implementation and operation of a BOLI plan; however, management should also demonstrate an understanding of the risks involved in a BOLI purchase and not delegate carrier selection, product choices or product design features to a vendor. If the bank uses a vendor, it should make appropriate inquiries into the vendor’s ability to honor its commitments and the vendor’s general reputation, experience, and financial capacity. The depth of these inquiries should be tailored to the size and complexity of the potential BOLI purchase. Furthermore, the bank should analyze and compare the qualifications and merits of several vendors to enhance the objectivity of the pre-purchase analysis.
Good corporate governance practices should be followed. If a state bank uses a vendor that is associated with the bank in any capacity, such as a director, officer, employee, principal shareholder or an affiliate as defined under sections 23A and 23B of the Federal Reserve Act,4 the board should fully and formally disclose such information along with appropriate analysis and support. The board must ensure that transactions of this nature are in compliance with internal conflicts of interest policies and laws addressing insider and affiliate transactions. For additional information about compliance with applicable laws see section V(D) – Other Considerations.
4. Carrier Selection
BOLI plans are typically of long duration and may represent significant risks for a state bank. Therefore, carrier selection is a critical step in a BOLI purchase. A state bank should review the product design, pricing, exit options, and administrative costs and services of the carrier(s) and compare them with the bank’s needs. In addition, the bank should review the carrier’s ratings (e.g., A.M. Best Company), general reputation, experience in the market place, and past performance. A broker or consultant, if used, may assist the bank in carrier evaluation, and bank management should ascertain the reasonableness of costs charged by the broker or consultant for services rendered.
Before purchasing a life insurance product, the bank should perform a credit analysis on the selected carrier(s) in a manner consistent with safe and sound banking practices for commercial lending. The carrier should exhibit a sound financial position, high level of experience in the BOLI market, and history of safe operations with its supervisory agencies. Not all carriers offer BOLI.
5. Review the Characteristics of the Available Insurance Products
While only a few basic types of life insurance products exist in the market place, insurance professionals can combine and modify these products in many different ways. The resulting final product can be quite complex. A state bank must review the characteristics of the various insurance products available. It should select the product or products with characteristics that match the bank’s objectives and needs. To accomplish this, the bank should thoroughly analyze and understand the products under consideration. The products offered include General Account, Hybrid Separate Account and Separate Account.
General Account: These products typically provide minimum interest rate guarantees. Current interest rates are typically credited on a quarterly or annual basis. The net rates credited reflect the overall earnings of an insurance company’s general account, as well as any expenses associated with the policies. The policies are backed by the general assets of the insurance company. Therefore, the credit quality of a potential carrier is a critical issue to potential buyers.
Hybrid Separate Account: These products combine features of both the General Account and Separate Account products. Often, two or three investment options are available. Like a General Account, a minimum interest and book value guarantee of assets are provided and the general assets of the insurance company stand behind the policies. Like a Separate Account, the BOLI assets are protected from the claims on the insurer.
Separate Account: The returns of these policies reflect assets in a segregated account that are not subject to the general creditors of the insurance company. Multiple investment options are typically available. Plan returns are subject to market fluctuations. With a Separate Account product, the policy owner bears the risk of default of assets in the separate account.
When purchasing insurance on “key persons” and individual borrowers, the bank should consider that the bank’s need for the insurance will likely disappear before the insured individual dies. In such cases, term or declining term insurance is often the most appropriate form of life insurance. Purchasing or holding excessive permanent insurance may be an unsafe and unsound practice if it subjects the bank to unwarranted risk, and BOLI subjects a bank to several risks which may be significant. These risks are further explained below in section V(C) – Risks Associated with BOLI. Purchasing “key person” policies where the bank is not the beneficiary may be considered compensation to the employee.
6. Assess the Benefits
A state bank should analyze the benefits of a contemplated BOLI purchase against the risks enumerated in section V(C) – Risks Associated with BOLI. While the analysis should include an assessment of how the purchase will accomplish the objectives specified in V(A)(1), Determination of the Need for Insurance, the analysis should also consider the potential long-term financial ramifications and requirements to the bank. The analysis should include an assessment of the anticipated financial performance of the insurance product, including the interest-crediting rate and the policy’s net yield.5 While the projected yield on some single-premium life insurance policies may seem attractive, the actual yield may be much lower. Insurance and administrative costs the issuer builds into the policy reduce the yield. Further, life insurance becomes more expensive as the insured person ages. At older ages, insurance costs can greatly reduce the stated credited interest rate on a cash value product. The bank should ascertain yields before and after these costs (i.e., gross yields and net yields). However, the bank should keep in mind that if the policies are held until the death of the insured(s), the bank will receive the death benefit proceeds from the policies.
One of the more common methods used to analyze future benefits and values of an insurance product are “pro forma” analysis. Often this involves assigning projected rates of return, along with expected holding costs and estimated tax benefits, for a proposed BOLI product, as compared to more traditional bank investments. The rationale used in deriving the assumptions of a pro forma analysis should be well documented and supported. Banks should also consider assigning percentages of probability with each pro forma scenario along with forecasting best and worst case scenarios.
7. Determine the Reasonableness of Compensation Provided to the Insured Employee if the Insurance Results in Additional Compensation
Split-dollar insurance arrangements typically provide additional compensation or other benefits to the employee. Before a bank enters into a split-dollar arrangement, it should identify and quantify the compensation objective, and ensure that the arrangement is consistent with the stated objective. Also, the bank should combine the compensation provided by the split-dollar arrangement with all other compensation to ensure that total compensation is not excessive. The Department views excessive compensation as an unsafe and unsound practice. State nonmember banks should refer to Appendix A of 12 CFR part 364 and state member banks should refer to Appendix D-1 of 12 CFR part 208 for guidelines on determining excessive compensation.
8. Analyze the Associated Risks and the Bank’s Ability to Monitor and Respond to those Risks
Ownership of or beneficial interests in BOLI may subject a bank to several types of risk, including: transaction; credit; interest rate; liquidity; compliance; and price risk.. A state bank’s pre-purchase analysis should include a thorough evaluation of these risks. Furthermore, the pre- purchase analysis should allow a bank to determine whether the transaction is consistent with safe and sound banking practices. In making this determination, a bank should consider, among other things, the:
• Complexity of the transaction;
• Size of the transaction relative to the bank’s capital;
• Diversification of the credit risk;
• Financial capacity of the bank, including the ability to hold BOLI for the anticipated period of time;
• Financial capacity of the insurance carrier(s); and
• The bank’s ability to identify, measure, monitor, and control the associated risks.
9. Volume Limitations
In assessing the size of the transaction, bank management should consider the cash surrender value (CSV)6 relative to its capital levels at the time of purchase. The state bank should also consider projected increases in the CSV and projected changes in capital levels for the duration of the contract. Consistent with prudent risk management practices, a bank should establish internal quantitative guidelines. These guidelines should generally limit the aggregate CSV of policies from any one insurance company and the aggregate CSV of policies from all insurance companies. Note: The actual amount received may be substantially affected by the tax considerations. Banks should know these implications prior to a policy’s acquisition.
The Finance Commission of Texas has adopted a maximum investment limit for BOLI carried on the books of a state bank from a single insurance issuer.
• Individual Limit to a Single Insurance Issuer: Pursuant to Title 7 of the Texas Administrative Code (7 TAC) § 12.3(a)(9) a state bank must limit its investment in the CSV of life insurance from any one issuer to 25% of Tier 1 Capital.
In conjunction, this memorandum establishes an aggregate concentration limit for all BOLI policies carried on the books of a state bank.
• Concentration Limit to All Insurance Issuers: A bank should limit its aggregate investment in the CSV of life insurance to all issuers to 25% of Tier 1 Capital. A state bank, however, should not automatically assume that a concentration level as high as 25% is acceptable, as any investment level must be justified and supported as discussed in this policy statement.
A state bank that desires to exceed the concentration limit should receive the prior written approval of the Commissioner to do so. The request should enumerate what steps the bank has taken to mitigate the risks involved.
Application of Limits to Separate Account BOLI: The above maximum investment and concentration limits apply to all BOLI, including Separate Account BOLI, even when the insurance carrier identifies such investments as Separate Accounts made up solely of high quality investments. This is because control over the investment and lack of liquidity associated with BOLI apply to Separate Account, Hybrid Separate Account and General Account products.
10. Evaluate Alternatives
Some BOLI purchases involve indemnifying the bank against a specific risk. For example, a state bank may purchase BOLI to indemnify the bank against the potential for loss arising from the untimely death of a “key person.” As an alternative to purchasing BOLI, a state bank could choose to self-insure against this risk. Another potential use of BOLI is to recover costs of or provide for an employee benefit plan. Instead of purchasing BOLI, a bank could choose to invest the money in other assets. Regardless of the purpose for a BOLI purchase, a complete pre- purchase analysis should include an assessment of the alternatives.
11. Exit Strategy
An important part of a state bank’s pre-planning and decision making process is the development of a well-evaluated exit strategy in the event that the bank needs to prematurely divest its ownership interest in the BOLI product. The board should fully analyze the financial ramifications to the bank were divesture to become a requirement or an option. Further, the exit strategy should describe the methods and means with which divestiture would occur in order to minimize possible asset value loss or liability recognition, including income tax consequences. The exit strategy should be updated annually with each performance review of the BOLI program.
Generally, BOLI policies can be surrendered at any time, and the full amount of the cash surrender value withdrawn. There are no financial penalties imposed by the insurance company.
However, before surrendering a BOLI policy, a state bank should obtain competent legal and accounting advice regarding any adverse tax consequences.
A state bank should be cautious about the practice of replacing one BOLI product with another, especially in the absence of a legitimate need to address material risk concerns. Transferring assets from one BOLI product to another BOLI product at a different insurance company is called a 1035 exchange (IRC Section 1035). The insurance company is likely to impose surrender charges or other restrictions if the replacement is done before the expiration of the surrender charge or restriction period provided in the policy contract. In some cases, insurance vendors may promote such practices as a means to increase their commission income, usually to the detriment of the bank. Regardless, the bank should consider the practice of replacing one or more BOLI product as a material event requiring comprehensive pre-purchase analysis and evaluation as discussed in this policy.
12. Approval and Documentation
The board of directors of a state bank should approve the initial BOLI program and any subsequent changes, and should maintain adequate documentation to show that the bank made an informed decision. For additional information about the ongoing review of a BOLI program, see section V(E) – Post-Purchase Monitoring.
B. Financial Considerations
Bank management should understand and analyze how BOLI will affect the bank’s financial condition. Management should analyze the effect the anticipated performance of the insurance will have on the bank’s earnings, capital, cash flows, and liquidity. Management should also consider the impact that surrender of the insurance (before maturity at the death of the insured) would have on the bank’s earnings and capital. This might occur if the bank had a credit quality concern relating to the issuer, if the tax treatment changed, or if the bank had other needs or uses for the invested funds.
C. Risks Associated With BOLI
Examiners will assess risk relative to its effect on capital and earnings. The key risks associated with BOLI are: transaction; credit; interest rate; liquidity; compliance; and price. An analysis of each of these risks is set forth in the following paragraphs.
1. Transaction Risk (including tax)
The degree of transaction risk associated with BOLI is a function of a bank not fully understanding or properly implementing a transaction. In addition to following the other guidelines included in this memorandum, a state bank should take two additional steps to help reduce transaction risk.
First, management should develop a thorough understanding of how the insurance product works and the variables that dictate the product’s performance. The variables most likely to affect product performance are the policy’s interest-crediting rate, mortality cost,7 and other expense charges. Typically, the most significant variable is the interest-crediting rate, followed by the mortality cost. Therefore, before purchasing BOLI, a bank should analyze projected policy values (CSV and death benefits) from multiple illustration scenarios provided by the carrier which utilize varying interest-crediting rates and mortality costs assumptions for each illustration.
Second, bank management should understand and analyze how BOLI will affect the bank’s financial condition. Given the anticipated performance of the insurance, management should analyze the effect on the bank’s earnings, capital, and liquidity. Management should consider the impact on the bank’s earnings and capital should the bank, for any reason, surrender the insurance before maturity. Other administrative costs related to legal, accounting, and tax issues, as discussed in V(D) – Other Considerations, should also be considered.
2. Credit Risk
All life insurance policyholders are exposed to credit risk, which is primarily a function of the insurance carrier’s financial ability and willingness to pay death benefits as contractually obligated. The credit quality of the insurance company and duration of the investment portfolio(s) are key variables in evaluating the level of credit risk. Additionally, policy design features are able to affect how credit risk exposure arises in BOLI. For example, with any life insurance policy, including BOLI, the expected time for collection of death benefits may be extremely long; additionally, the CSV is an unsecured, long-term, and non-amortizing obligation of the insurance carrier, if the funds are invested in a General Account.
To adequately minimize risk, before purchasing BOLI, bank management should evaluate the financial condition of the insurance company and continue to monitor its condition on an ongoing basis. In addition to reviewing the insurance carrier’s ratings, the bank should conduct an independent financial analysis consistent with safe and sound banking practices for commercial lending. As with lending, the depth and frequency of the analysis should be a function of the relative size and complexity of the transaction.
3. Interest Rate Risk
General Account8 and most Hybrid Separate Account products expose the policyholder to interest rate risk. The interest rate risk of these products is primarily a function of the policy’s interest-crediting rate. The insurance carrier establishes interest-crediting rates. Over the long term, interest-crediting rates are primarily a function of the carrier’s investment portfolio performance. The policy’s CSV grows at a slower rate with a declining interest-crediting rate. Because a bank’s investment in permanent life insurance is recorded as the policy’s CSV, the bank’s earnings decline as the policy’s interest-crediting rate declines. Due to the interest rate risk inherent in these products, it is particularly important that management fully understand this risk before purchasing the policy. Before purchasing permanent life insurance, management should:
• Review the policy’s past performance over various business cycles;
• Analyze projected policy values (CSV and death benefits); and
• Consider having the carrier use a different interest-crediting rate for each set of policy projections.
Variable or Separate Account9 products may also expose the bank to interest rate risk depending on the types of assets held in the separate account. For example, if the Separate Account assets consist solely of Treasury securities, the bank is exposed to interest rate risk in the same way as holding Treasury securities directly in its investment portfolio. However, because the bank does not control the Separate Account assets, it is more difficult for the bank to control this risk. Therefore, before purchasing a Separate Account product, management should thoroughly review and understand the instruments governing the investment policy and management of the Separate Account. Management should understand the risk inherent within the separate account and ensure that the risk is appropriate for the bank. Also, the bank should establish monitoring and reporting systems that will enable the bank to monitor and respond to price fluctuations.
4. Liquidity Risk
Liquidity risk stems from a bank’s inability to meet its obligations as they become due. In general, surrender proceeds are paid within thirty (30) days of policy surrender and by law must be paid within 6 months. It’s the tax ramifications that generally “limit” the liquidity since an excise tax of 10% must be paid on top of the usual tax on the gains. Although a secondary market for life insurance exists, typical BOLI policies are not attractive to buyers because of their high cash values relative to death benefits. Therefore, a bank should ensure that there is sufficient long-term financial flexibility to allow holding the asset in accordance with its expected use before purchasing. The inability of a bank to hold the life insurance until maturity may compromise the success of the BOLI plan. Part of this risk can be mitigated through the pre-purchase analysis of an exit strategy that minimizes the tax risk should premature disposal of BOLI becomes necessary. However, it should be recognized that the risk due to the lack of liquidity in BOLI is magnified given that a bank typically purchases life insurance policies through a conversion of a liquid asset (e.g. cash or marketable securities).
While the CSV of policies can be accessed quickly, via loan, withdrawal and surrender, loan charges and/or tax penalties may be imposed. To access the CSV, the bank must withdraw from or borrow against the policy. This borrowing may subject the bank to loan interest charges. In addition, distributions from most BOLI policies, whether via loan, withdrawal or surrender, will subject the bank to taxes on the gain, and a 10% excise tax penalty. The extent of potential expenses, including interest, taxes, and penalties in the liquidation of BOLI should be examined and understood by management pre-purchase, as various features of a policy could increase the cost and further increase liquidity risk.
5. Compliance Risk
Failure to comply with applicable laws, rules, regulations, and prescribed practices (including this memorandum) could compromise the success of a BOLI program and result in significant losses for the state bank as a result of fines, penalties, or loss of tax benefits. For this reason, a thorough compliance review is needed before BOLI products are purchased. Consideration should be given to any formal or informal contracts with the executives for deferred compensation or other benefit payments linked to the insurance arrangements. Any other bank contracts that may be related to BOLI products should also be reviewed. Care should be taken if a subsidiary or associated entity of the bank receives any commissions from the purchase of BOLI by the bank to avoid violation of rebating statutes. Additional legal and regulatory considerations are more fully discussed in section V(D) – Other Considerations in this memorandum.
6. Price Risk
Typically, price risk is associated with Separate Account BOLI. The policyholder selects an asset or group of assets to invest in and assumes all of the price risk associated with the investments within the Separate Account. In general, neither the CSV nor the interest-crediting rate on Separate Account products is guaranteed by the carrier. The level of price risk is dependent upon the type of asset(s) held within the Separate Account. The owner of Separate Account BOLI may elect to invest in very high quality assets or low quality assets. However, a state bank may only invest in Separate Account BOLI investments that the bank may invest in directly.
Because the bank does not have direct control of the Separate Account assets, it is more difficult for the bank to control price or other risks. Therefore, before purchasing a Separate Account life insurance product, management should thoroughly review and understand the instruments governing the investment policy and management of the Separate Account. Management should understand the risk inherent in the Separate Account and ensure that the risk is appropriate for the bank. Also, bank management should establish monitoring and reporting systems that will enable them to monitor and respond to price fluctuations.
A state bank may purchase Separate Account insurance products that hold equity securities only for the purpose of hedging its obligations under an employee compensation or benefit plan.10 This lessens the effect of price risk on the bank’s financial statements because changes in the amount of the bank’s liability will be hedged by changes in the value of the Separate Account assets. An example of such a relationship would be where the amount of the bank’s deferred compensation obligation is measured by the value of a stock market index, and the Separate Account contains a stock mutual fund that mirrors the performance of that index. If the insurance cannot be characterized as an effective hedging transaction, the presence of equity securities in a Separate Account is impermissible.
In addition to the general considerations discussed above, which are applicable to any Separate Account product, further analysis should be performed when purchasing a Separate Account product involving equity securities. At a minimum, a state bank should:
• Analyze the bank liability being hedged (e.g., deferred compensation) and the equity securities to be held as a hedge in the Separate Account. Such an analysis usually documents the correlation between the liability and the equity securities, expected returns for the securities (including standard deviation of returns), and current and projected asset and liability balances.
• Determine a target hedge effectiveness ratio and establish a method for measuring hedge effectiveness. Establish a process for altering the program if hedge effectiveness drops below acceptable levels. Consideration should be given to the potential costs of program changes.
• Establish a process for analyzing and reporting the effect of the hedge on the bank’s income statement and capital ratios. Such an analysis usually shows results both with and without the hedging transaction.
D. Other Considerations
Before BOLI is purchased, bank management must fully analyze and understand the legal, accounting, Call Report and tax implications of these significant purchases. Due to the complexity of these issues, outside advice and counsel may be needed. This guidance addresses many of the issues that are involved in BOLI purchases, but it is certainly not all-inclusive. Unusual circumstances and variations of standard BOLI products will require additional research and specialized assistance.
1. Accounting and Call Report
Banks should follow generally accepted accounting principles (GAAP) for financial reporting purposes. Accounting Standards Codification ASC 325-30 Investments in Life Insurance (ASC 325-30) discusses how to account for investments in life insurance.
Under ASC 325-30 and via Call Reports, a state bank should record its interest in the policy’s cash surrender value as an “other asset.” The increase in the cash value over time should be recorded as “other noninterest income.” In accordance with Call Report requirements, the bank should update its interest in cash value at least quarterly.
Sometimes the bank receives all the benefits, but separately agrees to provide those benefits to an employee as deferred compensation or split dollar life insurance. In this case, the bank should account for any cash surrender value in accordance with ASC 325-30. Also, the bank should record a deferred liability for any deferred compensation or split dollar arrangements in accordance with either Accounting Standards Codification 710 (ASC 710) or 715 (ASC 715), as appropriate.
Split-Dollar Arrangements: Under employee benefit split-dollar policies, the bank and the employee agree to share in the policy’s cash surrender value and/or death benefits .If such arrangements provide for post-retirement benefits, then the liability should be accounted for in accordance with ASC 715-60 Post-Retirement Benefits Other Than Pensions – Split Dollar Life Insurance Arrangements.
APB Opinion No. 12 requires that an employer’s obligation under a deferred compensation agreement be accrued according to the terms of the individual contract over the required service period to the date the employee is fully eligible to receive the benefits, i.e., the “full eligibility date.” Depending on the individual contract, the full eligibility date may be the employee’s expected retirement date, the date the employee entered into the contract, or a date between these two dates. APB Opinion No.12 does not prescribe a specific accrual method for the benefits under deferred compensation contracts, stating only that the “cost of those benefits shall be accrued over that period of the employee’s service in a systematic and rational manner.” The amounts to be accrued each period should result in a deferred compensation liability at the full eligibility date that equals the then present value of the estimated benefit payments to be made under the individual contract.
For each IRP, a bank should calculate the present value of the expected future benefit payments under the IRP at the employee’s full eligibility date. The expected future benefit payments can be reasonably estimated, should be based on reasonable and supportable assumptions, and should include both the primary benefit and, if the employee is entitled to excess earnings that are earned after retirement, the secondary benefit. The estimated amount of these benefit payments should be discounted because the benefits will be paid in periodic installments after the employee retires. The number of periods the primary and any secondary benefit payments should be discounted may differ because the discount period for each type of benefit payment should be based upon the length of time during which each type of benefit will be paid as specified in the IRP.
After the present value of the expected future benefit payments has been determined, the bank should accrue an amount of compensation expense and a liability each year from the date the employee enters into the IRP until the full eligibility date. The amount of these annual accruals should be sufficient to ensure that a deferred compensation liability equal to the present value of the expected benefit payments is recorded by the full eligibility date. Any method of deferred compensation accounting that does not recognize some expense for the primary benefit and any secondary benefit in each year from the date the employee enters into the IRP until the full eligibility date is not systematic and rational.
Technical Bulletin 85-4 addresses the accounting for BOLI. Only the amount that could be realized under the insurance contract as of the balance sheet date (i.e., the cash surrender value reported to the bank by the insurance carrier less any applicable surrender charges not reflected by the insurance carrier in the reported cash surrender value) is reported as an asset. Because there is no right of offset, an investment in BOLI should be reported as an asset separately from the deferred compensation liability.
State banks should follow Accounting Principles Board Opinion No. 20, Accounting Changes (APB 20), if a change in their accounting for deferred compensation agreements, including IRPs, is necessary. APB 20 defines various types of accounting changes and addresses the reporting of corrections of errors in previously issued financial statements. APB 20 states that “[e]rrors in financial statements result from mathematical mistakes, mistakes in the application of accounting principles, or oversight or misuse of facts that existed at the time the financial statements were prepared.”
For Call Report purposes, a state bank must determine whether the reason for a change in its accounting for deferred compensation agreements meets the APB 20 definition of an accounting error. If the reason for the change meets this definition, the error should be reported as a prior period adjustment in the Call Report if the amount is material. Otherwise, the effect of the correction of the error should be reported in current earnings. For more detailed information about IRPs, refer to FDIC FIL-16-2004, Interagency Advisory on Accounting for Deferred Compensation Agreements and Bank-owned Life Insurance.
2. Legal and Regulatory
Banks must ensure that BOLI programs comply with all laws, rules, regulations, and prescribed practices (including those discussed in this memorandum). A compliance review should be performed before purchase and annually thereafter to ensure continued conformity. The Department will evaluate all significant holdings and future purchases of life insurance by banks in light of these guidelines.
The bank should ensure execution of the appropriate policy endorsements, assignments, and related agreements. The bank should also determine if the policy provides adequate safeguards and controls to protect its interest in the policy. Lastly, management should ensure that the bank’s share of any cash surrender value and death benefits are appropriately endorsed or assigned to the bank.
Due to the complexity of this review, advice of qualified counsel may be necessary. In particular, the following areas should be reviewed:
• Affiliate transactions: Sections 23A and 23B of the Federal Reserve Act (12 USC 371c and 371c-1), also see 12 USC 1828(j) and 12 CFR part 223 (Regulation W);
• Insider transactions: 12 CFR part 215 (Regulation O) and Section 402 of the Sarbanes-Oxley Act of 2002 (15 USC 78m(k));
• Insider compensation: Appendix A of 12 CFR part 364 for nonmember banks, and Appendix D-1 of 12 CFR part 208 (Regulation H) for member banks.
• Employee retirement plans: Employee Retirement Income Security Act of 1974 (ERISA) (29 USC 1001 et seq.);
Affiliate Transactions: Banks should determine the applicability of, and ensure compliance with sections 23A and 23B of the Federal Reserve Act. For example, split-dollar life insurance arrangements may be subject to Section 23A of the Federal Reserve Act when a bank purchases an insurance policy, and the beneficiary is its holding company or a management official of the holding company. This will be considered an unsecured extension of credit because the bank pays the holding company’s portion of the premium, and the holding company will not fully reimburse the bank for its payment until sometime in the future. State banks may not make unsecured loans to affiliates.
In other cases, the parent holding company may actually own the insurance policy and pay the entire premium. A subsidiary bank may make annual loans to the holding company in an amount equal to the premiums paid or equal to the annual increase in the cash surrender value of the policy, with the insurance policy serving as collateral for the loan. The holding company repays the loans upon either the termination of employment or death of the insured employee. These loans are subject to the quantitative restrictions of section 23A, including the collateral requirements—130 percent of the amount of the loan in this case. The transactions must also comply with the provisions of section 23B of the Federal Reserve Act.
Insider Transactions: Certain insurance arrangements may be subject to Regulation O. In cases where the bank purchases the insurance to provide a fringe benefit to an executive officer of the bank and the bank pays the cost of the policy, the officer should either:
• Reimburse the bank for the amount of the premiums; or
• Report the economic value of the insurance benefit to the IRS as additional taxable income.
If the officer is responsible to reimburse all or a portion of the value of the insurance benefit, the obligation represents a loan by the bank to the executive officer and may be subject to Regulation O. In addition, certain insider loans may be restricted by the Sarbanes-Oxley Act of 2002 which amended Section 13 of the Securities and Exchange Act of 1934 (15 USC 78m).
Tax Treatment: Since the tax benefits are critical to the success of most BOLI programs, management should ensure that BOLI plans comply with all applicable tax law. Changes in tax law may influence management’s determination to continue or expand the bank’s BOLI program. Consequently, an initial and ongoing assessment of the tax implications is a necessary part of effective administration of a BOLI program.
E. Post-Purchase Monitoring
The state bank’s board of directors, with the assistance of management, should continue to monitor ownership and purchases of BOLI, at least annually, based upon the standards set forth in this memorandum.
1. Monitoring of Each Policy
With respect to individual BOLI policies purchased, the board should receive an annual report detailing the:
• Face and cash surrender values of policies purchased for each insured;
• Aggregate amount of all compensation, including purchases of BOLI policies, for each insured; and
• Continued designation of the insured person as a key employee, if applicable.
Appendix A provides an example to assist state banks in complying with this section.
2. Monitoring of Aggregate BOLI
With respect to the aggregate of all BOLI policies purchased, the board should approve no less than annually a report detailing the:
• Continued ability of BOLI to meet the bank’s goals and objectives;
• Material changes in policies or coverage;
• Adequacy of documentation, including written authorization from employees consenting to the BOLI purchase;
• Aggregate face and cash surrender values of policies purchased;
• Relationship of the face and surrender values to bank capital;
• Before and after tax rate of return of the policies;
• Liquidity and surrender value aspects of the policies;
• Changes in law and regulatory guidelines, including tax law;
• Financial condition of each insurance company and its continued ability to honor claims;
• Rating of each insurance company; and
• If separate account products are held, the price risk of the underlying investments.
Appendix B provides an example to assist a state bank in complying with this section.
CONTACT INFORMATION
For further information about this memorandum, contact the Regional Director assigned to your bank or a member of the Bank and Trust Supervision’s review staff in Austin (512-475-1300).
APPENDIX - A
Banks may purchase BOLI to protect the bank from the loss of a key officer or to provide compensation to employees, officers, or directors as part of a reasonable compensation package. It is important that board members know how much BOLI is purchased on each employee and how purchases relate to the employee’s overall compensation. The following table is provided to assist banks in the Post-Purchase Monitoring of BOLI programs. This table provides a reminder of some of the issues that banks should consider on an annual basis.

APPENDIX - B
Banks must monitor BOLI products after purchase. It is important that board members know how much BOLI is purchased from each insurance company and whether the investments are within the allowed limits. It is also important to assess the continued ability of BOLI to meet the bank´s needs and whether there have been any significant changes in laws and regulatory guidance. The following table is provided to assist banks in the Postpurchase Monitoring of BOLI programs.
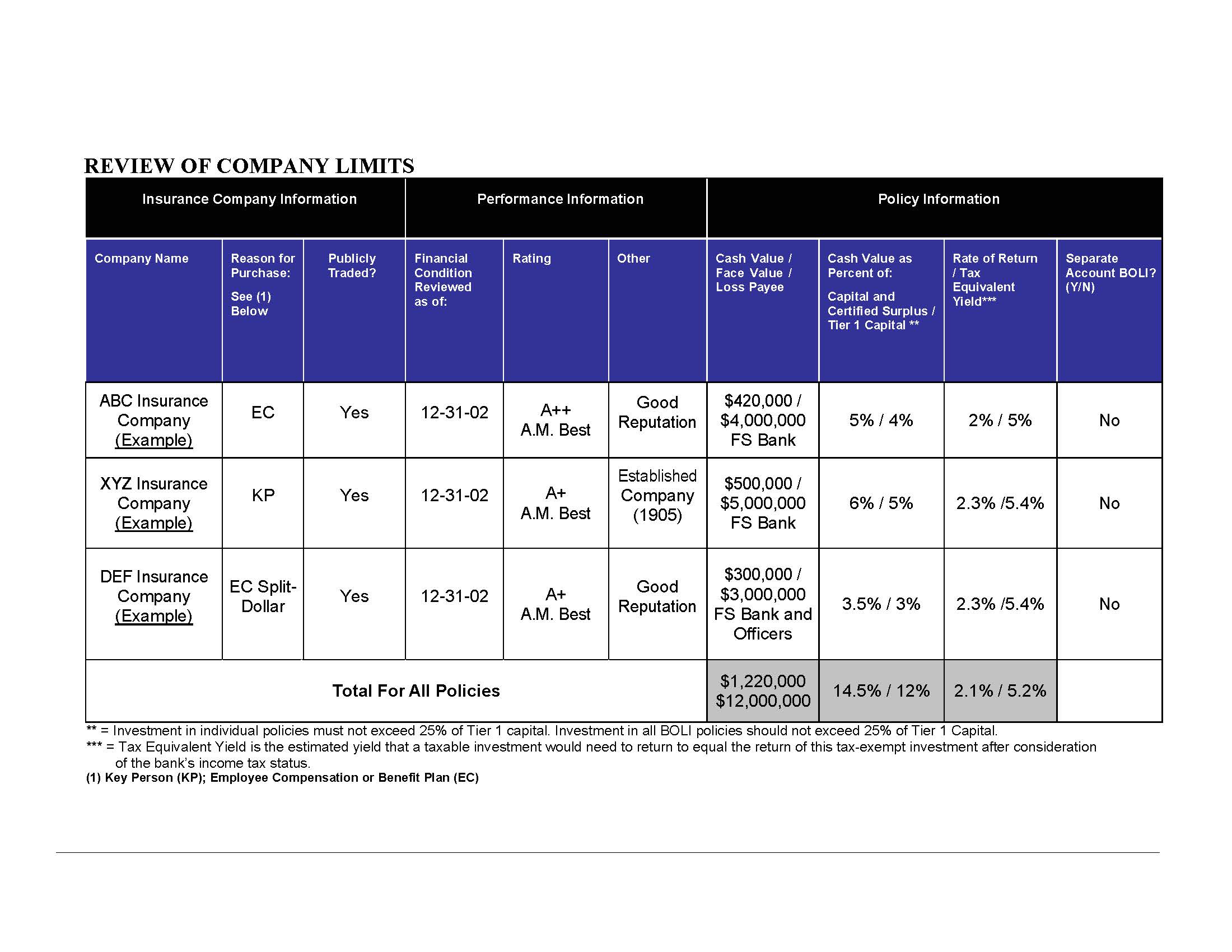
July 31, 1996
| TO: | All State-Chartered Banks |
| FROM: | Catherine A. Ghiglieri, Commissioner |
| SUBJECT: | Policy for Temporary Mortgage Purchase Programs |
Background
This Policy Memorandum revises and supersedes Numbered Memorandum 94-04. Numbered Memorandum 94-04 has been under review by the Department since August 1994, at which time its enforcement was temporarily suspended. In February 1996, the Finance Commission revised the legal lending limit rule (7 TAC 12) to incorporate guidelines for determining the difference between a loan purchase versus a loan financing transaction. Therefore, the revised policy does not address legal lending limit issues, but instead expands upon the significant safety and soundness issues arising from this activity. The policy parallels new examination procedures issued by the Department for examiner review of Temporary Mortgage Purchase Programs.
Purpose
A growing number of banks have become involved in the temporary funding of residential mortgage loans awaiting sale to the secondary market. This may be done through a traditional line of credit to the originating mortgage company, or the temporary purchase of the loans from the mortgage company. This Memorandum is only directed toward the latter activity, for which limited industry guidance currently is available. Temporary purchase programs generally present greater risk to the bank than a warehouse line due to the more direct loss exposure and higher volume of activity. This latter element, when combined with an otherwise minor deficiency or control weakness, can represent a substantial threat to bank capital if left undetected or uncorrected. Therefore, the board of directors of any bank operating a temporary purchase program must demonstrate heightened awareness and supervision to avoid undue risks to capital.
This Memorandum covers the following topics as they apply to temporary purchase programs: (1) an overview of the activity; (2) the potential risks; and, (3) minimum standards for a well-run program.
Overview of Activity
"Temporary mortgage purchase program" is the name given to activity whereby banks purchase single family residential mortgages originated by mortgage companies, while the loans are awaiting resale to investors in the secondary market. In practice, much of the activity parallels traditional warehousing arrangements. However, an essential element of the program is that the bank takes an ownership position in the loan, thus avoiding aggregation of the individual loans under an extension of credit to the originator. While temporary purchase programs may be employed in a variety of circumstances, they are most frequently associated with lower tier originators who do not qualify for warehouse lines of sufficient size to handle the volume of their activity.
In most temporary purchase programs, the bank's purchase occurs simultaneous with the loan's funding and loan documents are closed in the mortgage company's name. Ownership is assigned to the bank at closing, as is the purchase commitment from the secondary market investor which has been arranged by the originator.
A loan is normally owned less than 60 days pending the investor's final review. During this period, loan documents may be held by a variety of parties depending on the specific agreement between the bank and the originating mortgage company. However, a true purchase cannot legally occur unless documents evidencing ownership are within the bank's possession or control, either directly or through some type of bailee or custodial agreement with an independent third party. During the time a loan is owned by the bank, any payments on the note are likely to be collected by a third party and remitted to the bank, or held by an agent on the bank's behalf. The bank normally receives interest at the face rate on the mortgage loan purchased as well as a flat fee, which varies widely.
When the investor purchases a loan, the bank recovers the principal, plus interest and fees. Any excess over the purchase price is forwarded to the originator as compensation for their services. If an investor rejects a loan or fails to honor its purchase commitment, the bank owning the mortgage is responsible for regaining the original loan documents, carrying the loan, correcting any deficiencies, and reselling the asset if possible.
Potential Risks
Due to the success reported by many institutions engaged in temporary mortgage purchase programs, bankers and boards of directors may incorrectly believe that there is little risk in the activity. In fact, however, there are numerous incidents of banks sustaining high losses when temporary mortgage purchasing programs are not prudently controlled. Due to the fact that much of the profit is derived from high volume, even minor deficiencies may represent a significant threat to bank capital if left undetected and allowed to compound. Banks that attempt to operate temporary purchase programs without sufficient expertise and controls may be cited for unsafe and unsound activity by the Department of Banking, and risk the imposition of administrative action.
Risk of Fraud
Fraud in a temporary mortgage purchase program presents the largest risk to capital. This is particularly true to the extent that concentrations exist with any one mortgage originator. While the vast majority of mortgage companies perform their business legitimately, the ease of entry into the mortgage business and the emphasis on volume and quick inventory turnover make the industry susceptible to unscrupulous individuals. The weaker the financial condition of the mortgage company and the less effective a bank's controls, the greater the likelihood of fraud occurring through: (1) multiple sales of the same loan to several parties; (2) alteration or misrepresentation of the credit quality of a borrower; (3) use of fictitious borrowers; or (4) misapplication of funds from the sale or amortization of the loan. Permanent investors do not have to honor commitments on fraudulent credits, and VA and FHA guarantees would not be enforceable. Therefore, any fraud is usually a total loss to the bank.
Credit Risk
The nature of the temporary purchase program is such that a bank will have exposure to credit risk in a number of forms. In the ordinary course of the transaction, credit exposure to the mortgage borrower is limited due to the fact that the bank's period of ownership is confined. However, this exposure increases dramatically when a bank is forced to repurchase or retain a loan due to early payment default or documentation deficiencies, since the bank has acquired a longer term exposure in the face of mounting credit and market risk.
A bank also must evaluate the credit and reputation of the originating mortgage company due to its reliance on that entity to underwrite and document the purchased loans. If a mortgage company is experiencing financial difficulties, cutbacks in personnel and controls may materially affect the quality of the loans being originated, as well as contribute to a failure to meet prescribed due dates. Also, the possibility of fraud increases in desperate financial situations.
Finally, another source of credit risk is that resulting from reliance on the secondary market investor to buy out the bank's position. Investors under financial stress or experiencing liquidity problems may default on their purchase commitments, particularly if they have failed to hedge their purchase commitments.
Concentrations
The high volume nature of temporary purchase programs often creates asset concentrations many times the level of capital, which amplifies all other risk aspects discussed in this section. Concentrations in loans from one originator, sold to any one investor, or from any geographic region should be closely monitored and controlled. Banks also should control the volume of mortgages and outstanding funding commitments from a liquidity and balance sheet management perspective.
Out-of-Area Lending
In order to achieve a sizable volume of mortgage loan activity, a temporary mortgage purchase program may rely on a large volume of out-of-area loans, which by their very nature, increase the risks associated with the general program. The fact that a mortgage company is unable to obtain favorable financing within its own market may signal concern. A bank that purchases loans from a mortgage company which is out of its area is also more susceptible to fraud due to the lack of local market knowledge of the company and its principals, and the absence of day-to-day contact. In addition, a bank purchasing mortgage loans outside of the state may be not familiar with any particular disclosure or usury laws which would be applicable to the mortgage and possibly render it defective. Finally, should the ultimate sale of a purchased loan fall through and result in the bank holding a long-term asset, there may be substantial difficulty and expense in holding a loan on property outside of its standard lending area.
Funding
Ideally, banks should fund assets with deposits. However, many banks engaged in temporary purchase programs approach a volume and cyclical demand for funding which exceeds their capacity to generate from local deposits. Such banks may be tempted to reach out to higher cost and more volatile funding sources, which may adversely impact earnings and liquidity. Also, banks which rely on more expensive funds are more likely to compromise prudent standards of underwriting or controls in an effort to compensate for the higher priced funding. To the extent that maturities or repricing intervals are not aligned between the assets and underlying funding, the bank also may be susceptible to interest rate risk.
Interest Rate Risk
Direct interest rate risk is minimal in a well-run temporary purchase program under which loans are pre-sold to a strong investor, who in turn has hedged their position. However, any bank which purchases loans that have not been pre-sold is effectively speculating on interest rate movements. This could have a dramatic impact on capital through required mark to market accounting in an adverse environment. Indirect interest rate risk is also evident to the extent that investors are more likely to renege on a commitment in a rising rate environment. Finally, because fee income and the value of servicing rights swing widely based on interest rates, the effect of a changing rate environment on the financial condition of mortgage companies should not be ignored.
Documentation/Market Risk
The structure of most temporary purchase programs is such that the bank will not have direct control of the loan documents for much of the ownership period. This leaves the bank highly reliant upon third parties to recognize and protect its ownership rights. Failure to adequately control this aspect of the transaction can subject the bank to either a complete loss of a negotiable asset through misappropriation, or partial loss of value if only a portion of the original documents can be assembled in the case where the asset must be re-sold.
Documentation risk also arises through poor underwriting, or lost or defective supporting documents. These loans are likely to be rejected by the secondary market investor. In that case, the bank must either hold the defective loan as a permanent investment, or attempt to correct deficiencies and resale it. Unless a bank has "designated endorser" status or independent market contacts, it is likely to realize less than the full market price of the loan if forced to sell. In other instances, a bank may not be in a position to permanently own any volume of mortgage loans due to the potential strain on its balance sheet and loan servicing personnel.
Funds Transmittal Risk
Funds are transmitted twice during the typical life cycle of a temporarily purchased loan: from the bank to the closing agent at the time the loan is originated; and from the investor to the bank when the loan is purchased. If a bank does not sufficiently control these transmittals, it runs the risk of the funds being misappropriated by either the originator or the closing agent. There are instances when closing agents have colluded with mortgage originators and used loan proceeds in a manner other than represented to the bank, or allowed a loan to be sold to multiple purchasers. Also, mortgage originators may have the ability to override a bank's wiring instructions to an investor, especially if the investor is a government-sponsored agency which provides the originator access to a portion of their data base. Therefore, unless precautions are exercised, the originator could directly receive purchase proceeds from the investor and not notify the bank of loan sales.
Minimum Standards for a Well-Run Program
The following criteria are outlined to provide a set of standards which should be employed by bank management and the board of directors in establishing and/or reviewing a temporary purchase program. Due to the nature of risk, strong oversight should be evident for any bank engaging in a temporary purchase program. Above all, it is essential that the board ensure that adequate and competent staffing has been employed to oversee mortgage purchasing operations. Policies, comprehensive management information systems, quality control programs, and strategic and contingency planning are also essential to adequately protect capital.
Written Policy
A formal policy with specific limitations and control procedures is important to a well-run program. Components which should be included in such a policy include investment limitations, authorized loan products, maintenance of a list of approved mortgage companies and investors, limits on the purchase of loans which have not been pre-sold, and requirements for periodic reports to the board. Minimum requirements for participating originators, underwriting standards for loans purchased, and controls over the loan funding and sale transactions should also be addressed in a comprehensive policy.
Credit Approval Standards
A bank should review and approve each loan prior to its purchase. The review should be sufficient to document the bank's determination that the prospective borrower qualifies for the requested mortgage, and that debt service and collateral coverage are sufficient for bank and investor requirements. Beyond a credit analysis of the borrower and a check of the accuracy of calculations, the documents should be subjected to some limited verification to determine their accuracy and authenticity. This could include a call to the borrower's employer, and contact with the appraiser to verify the estimated value of the property. The extent and scope of verification will depend on the strength of, and the bank's experience with, a particular originator.
A thorough credit review should be performed at least annually on each mortgage company selling to the bank, along with periodic monitoring through interim reports. In reviewing and approving mortgage companies, consideration should be given to: site visits by bank officers; analysis of both audited and interim financial statements; review of credit reports on the company and its owners; verification of fidelity bond and errors and omissions insurance coverage; verification of state license; review of the "master sales commitment" agreements between the mortgage company and secondary market investors; verification of HUD/FNMA/FHLMC investor status; and review of HUD/FNMA/FHLMC quality control audits if applicable. To the extent that historic performance and rejection information may be available, this would also provide an important insight into a company's capacity to perform.
An analysis of the permanent investors to whom loans are sold is also prudent. Considerations appropriate to this review could include a review of a company's ratings under third party rating services; an analysis of audited annual financial statements; and/or the company's performance under past purchase commitments. The investor's willingness or ability to honor the bank's bailee letters and comply with prudent sale closing standards (such as responding to verification requests and direct wiring of remittance funds), also should be strongly weighed.
Written Agreements with the Mortgage Company
In order to specifically define the rights and responsibilities between the bank and selling mortgage companies, a board approved written agreement should be in place for each company selling loans to the bank. The agreement should address items such as: minimum standards for participating in the program (licensing, bonding, etc.); procedures for handling mortgage loan deficiencies; provisions for acquiring copies of important agreements between the mortgage company and other third parties; procedures for timing and submission of documents to the bank to facilitate pre-purchase review; and the responsibilities of each party in regard to mortgage loan defaults.
Mortgage Closing Standards
Most closings under a temporary purchase program are "table funded" by the bank at an independent title company or title attorney's office. Internal control over the closing process is very important to safeguard the bank's interests. Steps which should be taken include: direct (telephonic) confirmation with the investor of the purchase commitment; direct or indirect receipt of the original endorsed note and assignment, and certified copies of other documents prior to funding; receipt of an insured closing protection letter verifying fidelity and errors and omissions coverage on the closing agent; acknowledged wiring instructions to the closing agent; and limitation of disbursement at closing to less than the full secondary market price (to avoid pre-paying the originator's and closing agent's fees). Temporary purchase programs which fund loans from outside of the state must exercise special caution due to the differences in state laws. Certain states allow "wet funding," wherein document execution and loan disbursement occur simultaneously. This increases the bank's risk in the transaction. In "wet funding" states, documents should be received by facsimile prior to disbursement, with original/copies sent by overnight mail after funding.
Sale Closing Standards
Banks should insist that they receive direct payment of sale proceeds by the investor. To ensure against stale inventory or potential misappropriation of sales proceeds, banks also should carefully monitor any loan on the books for over sixty days, and follow up on any sales which do not occur on or before the target purchase date.
Quality Control Program
Banks engaging in a temporary purchase program should have a system of quality control which provides a means to identify potential weaknesses and risks in the program. Included in the system would be an independent audit of a portion of loans purchased, the scope and extent of which would vary depending on: the types of loans being purchased; the bank's knowledge of the loan originator; and the financial condition and historical performance of the originator. An audit of up to 10-15% of the loans purchased is an industry norm, with a larger sample employed for a new originator, or one experiencing financial difficulties. The audit should verify that all elements of the transaction complied with the bank's policies and procedures, as well as re-verify elements of the purchased loan.
Originators participating in government-sponsored programs already undergo a quality control audit to meet the specifications of the sponsoring entity. The audits typically include independent re-underwriting and reverification of at least 10% of the originations, as well as reappraisal of properties on 10% of the sample (10% of 10%). A case may therefore be made for a lower sample on mortgage companies engaging in these programs when the bank has a copy of the external quality control audit.
Management Information Systems
Comprehensive management information systems are essential to the smooth operation of a temporary purchase program. Bank management should have detailed and timely reports for supervising daily activity, while the board of directors should receive periodic summary reports on the volume of activity, exceptions, and profitability. It is also important to track: historic data on failed sales; the number and dollar volume of loans rejected by investors; and, documentation/underwriting exceptions by loan production source.
Contingency Planning
Board-approved contingency plans are strongly recommended for programs of any material size to provide a basis for responding to potential interruptions in the program. The "temporary" ownership may become long-term should loans be rejected by investors. Any legal or implied recourse from the investor to the bank should be considered as well. The bank's ability to retain some portion of the loans awaiting resale should be evaluated based on a reasonable "worst case" scenario (such as maximum exposure to any one investor). To the extent any actual recourse exists, the bank should identify funding mechanisms and liquidity sources to buy ineligible loans back from the secondary market if necessary.
Reserve Standards
The Allowance for Loan and Lease Losses should provide coverage for any risk of credit loss from the mortgages owned by the bank. In determining how much should be allocated, historic loss experience may be one consideration. Other items which may be assessed include: the risk of investor default; the impact of interest rates on borrowers' repayment capacity on adjustable rate mortgages; and the level of government-sponsored loans. If any loans are sold with recourse to the bank, separate recourse reserves should be established.
Accounting Standards
The bank should ensure that accounting techniques comply with generally accepted accounting principles and that activity is correctly reported in regulatory reports. Formal systems should be in place to: document the proposed disposition of each loan at the time of purchase; ensure that loans are recorded as "held for sale" and reported at the lower of cost or market in accordance with Financial Accounting Statement (FAS) 65 (Accounting for Certain Mortgage Banking Activities); and, defer loan fees in excess of cost in accordance with FAS 91 (Accounting for Non-refundable Fees and Costs Associated with Originating or Acquiring Loans and Initial Direct Costs of Leases).
Conclusion
The Banking Department supports state bank involvement in the mortgage lending process. Not only does the public benefit from increased credit availability, but banks operating with sufficient controls are able to acquire relatively low-risk assets at favorable yields. Temporary mortgage purchase programs allow banks to participate in the mortgage market without having to develop and staff internal origination operations. However, because of the high volume of most programs and a substantial element of risk involved, strong board and management oversight is essential.
July 31, 1996
| TO: | All State-Chartered Banks and Trust Companies |
| FROM: | Catherine A. Ghiglieri, Commissioner |
| SUBJECT: | Communication with External Auditors |
Background
This Policy Memorandum revises and supersedes Numbered Memorandum 87-11. The revision clarifies that the policy applies to trust companies, and formalizes the Department's request that Regional Offices be copied with external audit reports when they are received by the regulated institution.
Policy to Communicate and Coordinate Examination Work with Auditors
It is the policy of the Department of Banking to foster open and ongoing communications between its examining staff and the external auditors of the entities under its supervision. The Department recognizes that the cooperative efforts of examiners, banking and fiduciary officers, and external auditors are essential to conducting a thorough examination. The sharing of information and discussions of the methodologies used enable examiners and auditors alike to develop a more complete understanding of the condition of an individual entity. Further, this cooperation allows both parties to maximize the effectiveness of their resources by utilizing each other's work. This is particularly important since the Department is seeking to reduce regulatory burden by tailoring the scope of examinations to avoid unnecessary duplication of the work of external auditors.
Role of Regulated Entities
The Department encourages state banks and trust companies to contact their external auditors when an examination begins, advising them that any and all dialogue between the examiners and the auditors is both welcomed and encouraged. The auditors should also be invited to attend wrap-up exit meetings with the board and management. Finally, it is important that the Department receive a copy of any audit, directors' examination, or other special report, including especially a copy of the "management letter," upon completion of an audit engagement. This information should be copied to the appropriate Regional Office upon its receipt by the regulated entity. This facilitates the examination planning process and enhances the Department's ability to monitor the condition of regulated entities between examinations.
Policy on Audit Requirements
In 1993, the FDIC adopted a rule (12 CFR 363) which requires independent outside audits for all insured institutions having total assets greater than $500 million. The FDIC has a separate policy statement which advocates an external audit program for all banks.
The Texas Department of Banking similarly encourages banks and trust companies to consider the benefits that an external audit provides. The examination function has evolved to focus on safety and soundness matters, and does not consistently include a detailed verification of account balances or internal controls. The Department may require an independent external audit in instances where: (i) significant internal operating deficiencies are noted; (ii) the fidelity bond has expired or been canceled; or, (iii) where other circumstances are involved which necessitate verification and review by a qualified accounting firm.
May 3, 2016
| TO: | Texas State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Providing Consumer Complaint Notices |
PURPOSE
This Memorandum clarifies certain circumstances under which a bank, trust company, or other entity subject to Texas Administrative Code, Title 7, §11.37 is not required to provide to consumers information regarding filing a complaint with the Texas Department of Banking.
OVERVIEW
Texas Administrative Code Title 7, §11.37, "How Do I Provide Information to Consumers on How to File a Complaint?" (TAC §11.37) requires a bank, foreign bank, bank holding company, or trust company (collectively, an entity) chartered, licensed, or registered by the Texas Department of Banking (Department) to provide notice to a consumer of how to file a complaint with the Department. The rule was adopted to ensure that consumers are aware that contacting the Department is one available method of helping to resolve an issue they have with an entity.
Entities as Financial Agents
Entities occasionally enter into agreements with government agencies to act as the government´s financial agent or fiduciary in order for the government agency to carry out its goal of providing certain financial services or benefits to the public. How these joint entity-government programs are to operate is largely dictated by the contracting government agency overseeing the program. The Department is not a party to these agreements and the terms are established by the entity and the government agency, not the Department.
When the Department receives a question or concern from a consumer regarding a government program being operated by an entity as the government´s financial agent, the Department does not have the authority or the knowledge of the details of the program necessary to assist the consumer. This results in the Department only being able to direct the consumer to the appropriate government agency providing the program, rather than providing substantive assistance.
Who is a "consumer"?
TAC §11.37 requires that complaint notices be given to a "consumer" of an entity, which is defined as "an individual who obtains or has obtained a product or service from [an entity] that is to be used primarily for personal, family, or household purposes." In the situation described above, the individual obtains the product or service from the government agency, not from the fiduciary agent or entity. Therefore, an individual receiving a product or service from a government´s financial agent or fiduciary is not a "consumer" within the meaning of TAC §11.37.
CONCLUSION
An entity acting as a financial agent or fiduciary on behalf of a government agency is not required to provide information regarding filing a complaint with the Department with all privacy statements issued to those individuals, but the entity is encouraged to provide information regarding filing a complaint with the appropriate government agency overseeing the program.
April 11, 2024 (rev.)
| TO: | All State-Chartered Banks, Trust Companies, and Technology Service Providers; and |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Information Technology Examination Frequency and Ratings1 |
PURPOSE
This Supervisory Memorandum sets forth the Information Technology (IT) examination ratings and frequency guidelines for banks, trust companies, and technology service providers. The three types of examination scopes utilized by the Department for IT reviews are also defined in this policy.
IT EXAMINATION RATINGS
Banks and Trust Companies
The Department will issue component and composite ratings at each full scope examination for banks and trust companies. The overall rating is determined based on a review of IT risk-focused examination work procedures centered on managerial oversight including: establishment of policies and procedures; assessment of IT risks; testing of key controls; providing for business continuity after a disaster; and safeguarding of customer information. Component ratings are assigned for Audit, Management, Development & Acquisition, and Support & Delivery. Financial institutions under the continuous supervision examination program have component ratings issued along with the composite rating. The component and composite rating practices are addressed in Supervisory Memorandum 1001.
Technology Service Providers (TSPs)
The Department issues component and composite ratings for TSPs. The focus for the review is on four functional IT component areas: Audit, Management, Development & Acquisition, and Support & Delivery. The component and composite rating practices, as established in Supervisory Memorandum 1001, apply to TSPs.
SCOPE OF EXAMINATIONS
The scope or depth of each IT review will be determined based on the assessed IT risks of each institution as directed by the Director of IT Security Examinations (DITSE) or the Chief IT Security Examiner (CITSE). The Department utilizes three types of examination scopes for IT reviews: Full Scope, Visitation, and Continuous.
• A Full Scope Examination (Full Scope) is the most comprehensive. Examiners complete procedures that are designed to assess the entity's IT risks and controls. Component ratings and an overall composite rating will be issued and included in a Report of Examination produced for the entity.
• A Visitation is a narrowly scoped examination which may focus on one or more specific risk areas. The results of a Visitation will be documented with a Letter of Findings to the entity.
• A Continuous Examination Program (CEP) is primarily utilized in larger institutions, generally $10 billion and greater or as determined by the Commissioner or Deputy Commissioner, and includes a series of targeted reviews conducted over an examination cycle generally covering a 12-month period. The targeted reviews focus on one or more specific areas of the institution's IT operations. The results of targeted reviews are documented in a Letter of Findings. The results of the IT targeted reviews performed during the examination cycle are utilized to assign a composite CAMELS rating for the institution which is documented in a Report of Examination.
The Full Scope and CEP examinations meet the examination priorities of the Department and federal regulators. As with any functional area of a financial institution, if there are supervisory concerns about IT related risks, then interim examinations, on-site visits, and off-site monitoring may be performed as recommended by the DITSE or CITSE in collaboration with the applicable Regional Director (RD) or Chief Trust Examiner (CTE). These reviews and scope determinations will be performed under the direction of the DITSE or CITSE who can expand the scope of the examination when necessary.
The findings of the IT examinations may be embedded into the safety and soundness Report of Examination for the institution or delivered under separate cover as an independent Report of Examination or Letter of Findings as determined by the DITSE or CITSE and applicable RD or CTE.
EXAMINATION FREQUENCY
State-Chartered Banks
The frequency of an IT examination generally follows the frequency of safety and soundness examinations for state-chartered banks. IT examinations generally will be scheduled within 120 days prior to, or on the same day as, the start date of the safety and soundness examination. In certain circumstances, the examination may be delayed up to 60 days after the safety and soundness examination start date, with the concurrence of the Director of Bank and Trust Supervision. The frequency of safety and soundness examinations for state-chartered banks is addressed in Supervisory Memorandum 1003.
In situations where the most recent composite IT rating is 3, 4 or 5, the IT examination frequency will continue to coincide with the safety and soundness examination frequency; however, during the interim, a Full Scope examination, Visitation, or an Off-site review will be performed 90 days before or 90 days after the mid-point in the safety and soundness examination cycle. The scope and timing of the interim examination will be determined by the DITSE or CITSE based on factors such as severity of weaknesses, management's capability, and information in progress reports. Component and composite IT ratings will be assigned at a Full Scope examination and a Report of Examination will be provided to the bank. If a Visitation or Off-site review is performed, then no rating will be assigned, and a Letter of Findings will be provided to the bank.
Exceptions to the IT Examination Frequency for State-Chartered Banks
Change in Scope of Safety and Soundness Examination:
If the safety and soundness Interim Risk Examination and Assessment (IREAP)2 examination is converted to a Full Scope examination and the Bank Composite Rating is subsequently upgraded to allow for an 18-month examination cycle, then:
• If the IT Rating is a 1 or 2:
• A Full Scope IT exam will be performed approximately 6 months after the converted Full Scope safety and soundness exam. The IT examination frequency will then follow the 18-month cycle; or
• If the IT Rating is a 3, 4, or 5:
• A Full Scope IT examination will be performed approximately 6 months after the converted Full Scope safety and soundness examination followed by a Full Scope IT examination, Visitation, or Off-site review in 12 months. The IT examination frequency will then follow the 18-month cycle with a Full Scope examination, Visitation, or an Off-site review performed 90 days before or 90 days after the mid-point in the safety and soundness examination cycle.
Change in Frequency of Safety and Soundness Examination
• In the event the financial institution's safety and soundness examination frequency increases, if the most recent IT composite risk rating is a 1 or 2, then the IT examination may be delayed up to 6 months after the safety and soundness examination due date.
• If the safety and soundness examination is delayed for any reason, the IT examination may be delayed as well with the goal of beginning the IT examination no later than during the safety and soundness examination. The flexible due date allows coordination with the bank to reduce regulatory burden, to preclude conflicts with safety and soundness examination procedures, and to provide the option for the IT examination information to be collected closer to the date of the safety and soundness examination.
Trust Companies
The frequency of an IT examination generally follows the frequency of safety and soundness examinations for trust companies, with the IT examination due within 120 days prior to or on the same day as the start date of the trust company examination. In certain circumstances, the examination may be delayed up to 60 days after the safety and soundness examination start date, with concurrence by the Director of Bank and Trust Supervision. Trust companies exempt under Texas Finance Code §182.011, do not receive an IT examination. The frequency of safety and soundness examinations for trust companies is addressed in Supervisory Memorandum 1004.
In situations where the most recent composite IT rating is 3, 4 or 5, the IT examination frequency will continue to coincide with the safety and soundness examination frequency; however, during the interim, a Full Scope examination, Visitation, or an Off-site review will be performed 90 days before or 90 days after the mid-point in the safety and soundness examination cycle. The scope and timing of the interim examination will be determined by the DITSE OR CITSE based on factors such as severity of weaknesses, management's capability, and information in progress reports. Component and composite IT ratings will be assigned at a Full Scope examination and a Report of Examination will be provided to the trust company. If a Visitation or Off-site review is performed, then no rating will be assigned, and a Letter of Findings will be provided to the trust company.
Exceptions to the IT Examination Frequency for Trust Companies
Change in Frequency of Safety and Soundness Examination
• In the event the trust companies' safety and soundness examination frequency increases, if the most recent IT composite risk rating is a 1 or 2, then the IT examination may be delayed up to 6 months after the safety and soundness examination due date.
• If the safety and soundness examination is delayed for any reason, the IT examination may be delayed also, with a goal of beginning the IT examination no later than during the safety and soundness examination. The flexible due date allows coordination with the trust company to reduce the regulatory burden, to preclude conflicts with safety and soundness examination procedures, and to provide the option for the IT examination information to be collected closer to the date of the safety and soundness examination.
Technology Service Providers (TSPs)
TSPs are assigned to one of three examination frequency tiers by the DITSE or CITSE. The tier assigned to each TSP will be based on a variety of factors including complexity of the TSP, the number of state-chartered banks and trust companies that they service, the type of information technology service they provide, their affiliation with state-chartered institutions, and if they are subject to examination by other regulatory agencies.
The three tiers are defined as follows:
Tier 1
These TSPs are generally owned, controlled, or otherwise affiliated with a bank that provides critical data processing and/or managed services for affiliated banks. Tier 1 TSPs will be examined on a frequency as determined by the FFIEC Risk-Based Examination Priority Ranking in the Federal Regulatory Agencies' Administrative Guidelines: Implementation of Interagency Programs for the Supervision of Technology Service Providers. The FFIEC Risk-Based Examination Priority Ranking form will be completed at the conclusion of each IT examination of a TSP. For 1 and 2 rated Tier 1 TSPs, the DITSE or CITSE may establish more frequent examinations than as determined by the Examination Priority Ranking as long as the frequency is not more often than the safety and soundness examination of the lead affiliated bank. (Often TSPs and their affiliated banks share IT control policies and procedures. Conducting an IT examination of the TSP that coincides with IT examinations of the affiliated banks can result in a substantial reduction in regulatory burden.)
In situations where the most recent composite IT rating is 3, 4 or 5, the examination frequency will follow the FFIEC examination frequency; however, during the interim, a Full Scope or Visitation examination may be performed. The scope and timing of the interim examination will be determined by the DITSE or CITSE based on factors such as severity of weaknesses, management's capability, and information in progress reports.
The findings of TSP examinations will be conveyed through an IT Report of Examination.
Tier 2
These TSPs are generally companies such as large national data processing companies that are included in the FFIEC's Significant Service Providers (SSP) Program, formerly referred to as the Multi-Regional Data Processing Servicers (MDPS) Program. Tier 2 TSPs are examined by FFIEC member agencies under a prescribed frequency and are not subject to routine examination by the Department, although staff may participate in the examination of these entities with federal agencies. Due to the type of service they provide and number of banks they service, the Department monitors examination data received from the FFIEC member agencies.
Tier 3
These TSPs are often small regional technology services companies or companies that primarily provide secondary technology services to state-chartered financial institutions. Secondary technology services are primarily non-core data processing services such as document imaging, item processing, credit reporting, statement rendering, and compliance reporting. Tier 3 TSPs are generally examined by FFIEC member agencies. Department staff may participate in the examination of these entities with federal agencies, elect to conduct an independent examination based on the risk profile of the TSP, or defer to the FFIEC agencies. The Department monitors examination data received from the FFIEC member agencies on Tier 3 TSPs.
COOPERATIVE EXAMINATION PROGRAM - BANKS AND TECHNOLOGY SERVICE PROVIDERS
The Department of Banking in cooperation with the Federal Reserve Bank of Dallas (FRB) and the Federal Deposit Insurance Corporation (FDIC), has committed to coordinating examination efforts to reduce regulatory burden. As a result, the general practice of the agencies is to alternate examinations between the Department and the FDIC or, if the institution is a member bank, with the FRB. However, the Department will conduct a separate examination, or a joint examination with the appropriate federal supervisory agency, whenever deemed appropriate. IT examinations of commercial banks performed by federal banking agencies will be accepted in meeting the Department's examination priority guidelines.
CONTACT INFORMATION
Questions about this policy may be directed to either Jared Whitson, Director of Bank and Trust Supervision, at (512) 474-1300, or the Department's Director of IT Security Examinations, Ruth Norris, at (713) 932-6146.
September 30, 2019
| TO: | Chief Executive Officers of State-Chartered Banks and |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Risk Managment of Account Takeovers |
Purpose
This Supervisory Memorandum was originally issued on January 9, 2012 to address the minimum standards needed to minimize the risks of Corporate Account Takeovers. Since then, cyber thieves have expanded their targets to include both businesses and individuals. The account takeover form of theft continues to evolve and has become more sophisticated. Today, business e-mail compromise (BEC) is a type of account takeover which is growing rapidly. This type of cyber-enabled financial crime can cause significant financial harm to its victims and impact entire communities and financial institutions. Texas banks and their customers, municipalities, school districts, churches, non-profit organizations, corporate businesses, and all customers that perform electronic transfers are at risk of account takeovers. All banks should be aware of and address the risks of electronic financial crimes and identify, develop, and implement appropriate risk management measures. This Supervisory Memorandum has been revised to include other forms of account takeover crimes.
Background
Account Takeover is a form of identity theft where cyber thieves gain control of a business’ or individual’s bank account by stealing Internet banking passwords and other valid credentials. Thieves can then initiate fraudulent wire and ACH transactions to accounts they control. Businesses and individuals with limited or no internal computer safeguards and disbursement controls are especially vulnerable to theft when cyber thieves gain access to their computer systems, typically through malicious software (malware). Malware infects a computer system not just through ‘infected’ documents attached to an email but also simply when an infected website is visited. BEC is a type of account takeover that can take many forms but is based on deception when an employee with access to company finances is tricked into making a wire transfer he/she thinks is a legitimate transaction but is actually initiated by thieves impersonating the CEO or other senior level employee.
Large financial losses have occurred from electronic crimes through the banking system. In Texas, electronic thefts through banks have ranged from a few thousand to several million dollars1. Nationwide, the BEC scam has resulted in losses of over $3 billion since 2015 2. Account takeover thefts have occurred in banks of all sizes and locations, and losses may not be covered by the bank’s insurance. Along with the financial impact, there is also a very high level of reputation risk for financial institutions.
Overview
In 2010, due to the increasing volume of financial losses from electronic crimes occurring through the banking system, the Department, in cooperation with the United States Secret Service, formed the Texas Bankers Electronic Crimes Task Force (Task Force) to develop recommended practices to mitigate the risks of electronic crimes such as Corporate Account Takeover. This Task Force was composed of operational executives from a diverse group of banks in terms of size, complexity, and market environment. Members also included the Independent Bankers Association of Texas, the Texas Bankers Association, and SWACHA (now ePayResources). The Department’s Director of IT Security Examinations served as a liaison member.
The Task Force developed a list of recommended processes and controls which expanded on a three-part risk management framework of: 1) Protect; 2) Detect; and 3) Respond developed by the United States Secret Service, the Federal Bureau of Investigation, the Internet Crime Complaint Center (IC3), and the Financial Services Information Sharing and Analysis Center (FS-ISAC)3 . The Task Force also developed Best Practices for Reducing the Risks of Corporate Account Takeovers (Best Practices) to help banks establish specific practices to implement the recommended processes and controls. The Best Practices document is a valuable resource to effectively reduce risk.
As the Task Force was concluding its work related to Corporate Account Takeover, the Federal Financial Institutions Examination Council (FFIEC) released a document titled Supplement to Authentication in an Internet Banking Environment (FFIEC Supplemental Guidance). The FFIEC Supplemental Guidance, issued on June 28, 2011, reinforces previous FFIEC guidance related to risk management of online transactions and updates regulatory expectations regarding customer authentication, layered security, and other controls related to online activity. The Task Forces' recommended three-part Corporate Account Takeover risk management framework and related controls are similar to controls in the FFIEC Supplemental Guidance and include the minimum expectations conveyed in the FFIEC guidance. The Task Force guidance differs from the FFIEC Supplemental Guidance in that it has a more specific focus on reducing the risk of Corporate Account Takeovers and therefore provides additional steps to implement.
The account takeover form of theft has shifted since it was first used by criminals and addressed by the Task Force. BEC shares many of the controls needed to protect against account takeover and the practices developed by the Task Force reduces the risk of both. Banks are encouraged to evaluate account takeover risk reduction practices with BEC in mind as a possible hybrid theft that could be attempted on customers.
Risk Management Standards
There are nineteen processes and controls (components) to support the three-part risk management framework of Protect, Detect, and Respond. Bank management and the board of directors must address each of these nineteen components in a risk management program to mitigate the risk of an account takeover. Since the Task Force included both small and large bank representatives, the required components are broad enough to accommodate the unique needs of every bank and its customers utilizing online banking services. Banks may adopt any practices to implement the components of Protect, Detect, and Respond. Although the use of the Best Practices developed by the Task Force is optional, using these practices as a starting point will greatly assist most banks in implementing appropriate practices. The Best Practices are cross referenced to each of the components listed below and are attached. If your bank does not have any business customers that send electronic instructions to transfer funds, you would only need to complete the risk assessment mentioned in P1 below.
The minimum standards for a risk management program to mitigate the risk of Account Takeover are as follows:
PROTECT
Implement processes and controls to protect the financial institution and corporate customers.
P1. Expand the risk assessment to include corporate account takeover.
P2. Rate each customer (or type of customer) that performs online transactions.
P3. Outline to the Board of Directors the Corporate Account Takeover issues.
P4. Communicate basic online security practices for corporate online banking customers.
P5. Implement/Enhance customer security awareness education for retail and high risk business account holders.
P6. Establish bank controls to mitigate risks of corporate accounts being taken over.
P7. Review customer agreements.
P8. Contact your vendors to regularly receive information regarding reducing the risk of Corporate Account Takeovers.
DETECT
Establish monitoring systems to detect electronic theft and educate employees and customers on how to detect a theft in progress.
D1. Establish automated or manual monitoring systems.
D2. Educate bank employees of warning signs that a theft may be in progress.
D3. Educate account holders of warning signs of potentially compromised computer systems.
RESPOND
Prepare to respond to an incident as quickly as possible (measured in minutes, not hours) to increase the chance of recovering the money for your customer.
R1. Update incident response plans to include Corporate Account Takeover.
R2. Immediately verify if a suspicious transaction is fraudulent.
R3. Immediately attempt to reverse all suspected fraudulent transactions.
R4. Immediately notify NACHA of the incident.
R5. Immediately notify the receiving bank(s) of the fraudulent transactions and ask them to hold or return the funds.
R6. Implement a contingency plan to recover or suspend any systems suspected of being compromised.
R7. Contact law enforcement and regulatory agencies once the initial recovery efforts have concluded.
R8. Implement procedures for customer relations and documentation of recovery efforts.
The Department has adopted the above components supporting the Protect, Detect, and Respond framework in setting the minimum standards for a risk management program to mitigate the risks of an account takeover. The Department's Information Technology Security Examiners have implemented examination procedures which focus on the nineteen components in this Memorandum as well as the FFIEC Supplemental Guidance.
For further information about this memorandum, contact Phillip Hinkle, Chief IT Security Examiner at (972) 241-1426.
Attachment
ATTACHMENT
TEXAS BANKERS ELECTRONIC CRIMES TASK FORCE
Best Practices: Reducing the Risks of Corporate Account Takeovers
Updated September 30, 2019 1
The Texas Bankers Electronic Crimes Task Force (Task Force) was formed by the Texas Banking Commissioner in cooperation with the United States Secret Service to develop recommended practices to mitigate the risks of electronic crimes such as Corporate Account Takeover. The Task Force developed a list of nineteen recommended processes and controls for reducing the risks of Corporate Account Takeovers. These processes and controls expand upon a three-part risk management framework developed by the United States Secret Service, the Federal Bureau of Investigation, the Internet Crime Complaint Center (IC3), and the Financial Services Information Sharing and Analysis Center (FS-ISAC)2 . Fundamentally, a bank should develop processes and controls centered on these three core elements:
1. Protect
2. Detect
3. Respond
A set of best practices has been compiled for each of the recommended processes and controls under the Protect, Detect, and Respond framework. These best practices are not an all-inclusive list and are provided as guidance to assist in implementing the nineteen processes and controls needed to reduce the risk of Corporate Account Takeover thefts. The Federal Financial Institutions Examination Council's (FFIEC) Supplement to Authentication in an Internet Banking Environment (FFIEC Supplemental Guidance)2 issued on June 28, 2011, conveys minimum expectations which are noted within this document. It is important to remember that electronic crimes are dynamic as cyber criminals continually change their techniques. Additional changes in risk management processes and controls will be necessary as this type of theft continues to evolve.
I. PROTECT
P1. Expand the risk assessment to incorporate Corporate Account Takeover.
The risk assessment should include risks of Corporate Account Takeovers and be reviewed and updated at least annually for threats and risks related to online payment services. After the risk assessment is updated, an analysis should be made to identify the bank’s existing controls that need to be updated or controls that need to be implemented to achieve compliance with regulatory guidance. A sample Corporate Account Takeover risk assessment is available electronically on the Corporate Account Takeover page on the Texas Department of Banking website.
An effective risk management assessment should:
1. Define the scope and complexity of the institution's payment and online banking services, noting any changes since the prior risk assessment;
2. Identify what functionality is offered or has changed regarding:
a. Online wire transfers;
b. Online ACH origination;
c. Online bill payments;
d. Delivery channels (such as mobile banking or remote deposit capture);
3. Assess if transaction limits have been set within the automated system and if those limits are appropriate;
4. Present a clear understanding of the bank's:
a. Customer segmentation (e.g., number of business customers or types of customers adopting online banking) and any changes that have occurred;
b. Customer utilization of online banking services - type and extent; and
c. Expected electronic payment volumes (size and frequency of wires and ACH origination files - both the average and peak volumes);
5. Assess reliance on third-party service providers for electronic payment processing and delivery of online banking services3 ;
6. Determine and assess on-going customer education and training practices;
7. Identify and assess all "automated pass-through" payment processing activities (e.g. online, real-time instructions for wire/ACH transactions that are automatically passed to the payment system operator, usually the Federal Reserve Bank, for processing or that are automatically passed to a bill payment system) and assess practices for reviewing automated anomaly detection alerts;
8. Identify and assess manual controls (and/or any automated anomaly detection) used to evaluate transactions that are not automatically sent to processor;
9. Determine the ability of corporate customers to correct, update, or change ("uninitiate") a transaction without further confirmation/authentication of the final transaction's instruction;
10. Assess the training and awareness of bank employees that process incoming transfer instructions, as well as the adequacy of staffing for these activities;
11. Assess the competency of bank staff responsible for sustaining adequate risk management practices related to ever evolving electronic payment risks, which includes considering available resources such as service providers and security and audit vendors;
12. Identify the most significant types of fraud being experienced by the industry and the emerging threats;
13. Evaluate the degree to which Information Technology (IT) security training is provided to all employees including bank managers and front-line customer contact employees. (Is there a strong corporate culture of security?); and
14. Assess the need for electronic theft insurance. If this type of insurance has been purchased, contact insurance carrier to determine if there are any required controls. Evaluate compliance with those controls.
P2. Rate each customer (or type of customer) that performs online transactions.
It is important to know the level of risk associated with customers using online banking services and once identified, to know those customers that are high risk. While the focus of these best practices is on corporate accounts that perform online wire and ACH transactions, any customer with any online transaction capability (including bill payments) should be evaluated for risk. Additionally, the FFIEC Supplemental Guidance applies to both business and consumer accounts. Reviews for risk rating customers should be conducted at least annually and documented. There are many different methods and formats that can be used based on the bank's size and resources. A bank may choose to simply rate all consumer customers using bill payment services with low transaction amounts and a low volume limit at a lower risk category than corporate customers. Another option would be to rate as high risk all corporate customers with certain online capabilities. In this case, "individually documented" reviews to determine the risk rating of each customer would not be necessary. However, banks with a moderate or small number of corporate customers may choose to rate their customers individually.
The following criteria could be used for risk rating a customer:
1. Type of business:
a. Domestic versus International; and
b. Retail versus wholesale;
2. Average Account Balances (loans and deposits);
3. Services Utilized:
a. Wire transfer;
b. ACH debit origination files 4 ;
c. ACH credit origination files; and
d. Bill payment;
4. Standard Entry Class (SEC) codes assigned to customer's transactions 5;
5. Volume of transactions 6;
6. File Limits/Frequency 7;
7. Security measures the business account holders utilize (see section P4 below); and
8. Business account holder's administrative controls over their users and system configurations.8
P3. Outline to the Board of Directors the Corporate Account Takeover issues.
The Board of Directors should be informed of the risks and controls related to Corporate Account Takeovers and provided with examples of the highest risk customers. This can be accomplished through the following actions.
1. Provide a general description of this crime, how it occurs, and losses experienced in Texas and the United States 9.
2. Provide a list of high-risk business account holders with their estimated exposure.
a. If all account holders have not been risk rated when the report to the Board is made, specify a few of the business customers at greatest risk or list an approximate number of business account customers in the bank's highest category of risk.
b. If the list of applicable account holders is large, provide summary information and a few examples.
3. Describe the primary measures the bank will be implementing, or has already implemented within the Protect, Detect, and Respond framework.
4. Discuss the action plan and time frames for fully implementing each portion of the Protect, Detect, and Respond framework and for implementing the controls that are needed to meet the minimum expectations in the FFIEC Supplemental Guidance.
P4. Communicate basic online security practices for corporate online banking customers.
The vast majority of cyber thefts begin with the thieves compromising the computer(s) of the business account holders. Perpetrators often monitor the customer's email messages and other activities for days or weeks prior to committing the crime. The corporate customer is most vulnerable just before a holiday when key employees are on vacation. Another risk period is on a day the business office is relocating or installing new computer equipment. Employees may be distracted and think a problem conducting online banking is due to a new network or equipment. Therefore it is important and necessary for the corporate customer's employees to follow established security practices. The bank should periodically communicate to the business account holders some or all of the following security practices that the business can implement to reduce their risks of theft. Basic practices to implement include:
1. Provide continuous communication and education to employees using online banking systems. Providing enhanced security awareness training will help ensure employees understand the security risks related to their duties;
2. Update anti-virus and anti-malware programs frequently;
3. Update, on a regular basis, all computer software to protect against new security vulnerabilities (patch management practices);
4. Communicate to employees that passwords should be strong and should not be stored on the device used to access online banking;
5. Adhere to dual control procedures;
6. Use separate devices to originate and transmit wire/ACH instructions;
7. Transmit wire transfer and ACH instructions via a dedicated and isolated device10;
8. Practice ongoing account monitoring and reconciliation, especially near the end of the day;
9. Adopt advanced security measures by working with consultants or dedicated IT staff; and
10. Utilize resources provided by trade organizations and agencies that specialize in helping small businesses. See Appendix A for a list of resources.
P5. Implement/Enhance customer security awareness education for retail and high-risk business account holders.
The FFIEC Supplemental Guidance states that security awareness education should address both business and retail account holders. The effectiveness of the education program and the need for updates due to changes in technology products and security threats should be evaluated at least annually, if not more frequently due to the ever-evolving nature of cyber-crime. The extent of security awareness education may vary between customers with different risk ratings. Options for contacting customers include one-on-one or small group meetings, postal mail, email, notices on the bank's website, and telephone calls. Presentations at civic organizations will also be beneficial. Several security and audit vendors as well as trade associations in Texas have already developed presentation programs. Additionally, a sample presentation developed by the Task Force for educating account holders is available on the Texas Department of Banking website.
In addition to the basic online security practices mentioned in section P4 above, security awareness education for both retail and business customers could include:
1. Procedures or user guidelines for using the bank's corporate internet banking service;
2. System security features that are available and/or that have been implemented;
3. Procedures to alert bank staff (including specific phone numbers and departments) when the account holder suspects a problem;
4. Bank policy regarding when, why and how the bank will contact online banking customers11;
5. Protections provided and applicability of Regulation E to electronic funds transfers and the types of accounts with Internet access12;
6. Common security threats and actions to take in order to prevent, detect, and respond to those cyber threats (See Appendix B for examples);
7. Security education resources for the customer (See Appendix A) and resources that help customers keep abreast of new and emerging issues, such as online security magazines and security vendor websites;
8. Developing an incident response plan (See Appendix C); and
9. Applicability of laws and regulations to business owners to safeguard information. (See Appendix D).
Additionally, high risk customers should be specifically contacted and made aware of their exposure to electronic theft. In particular, they should be made aware of:
1. Account takeovers and cyber thieves;
2. Exposure risks;
3. Recommended minimum security measures to implement (See P4 above);
4. Benefits of the business performing a risk assessment regarding online payment services;
5. Insurance coverage needs related to electronic thefts; and
6. Other resources available on this topic are found in Appendix A.
P6. Establish bank controls to mitigate risks of corporate account takeovers.
It is important to remember that no single control is effective. The FFIEC Supplemental Guidance establishes expectations for layered security controls which should include, at a minimum, the following two elements for both business and consumer accounts.
1. Processes to detect anomalies and respond to suspicious activity13 related to:
a. Initial login and authentication for access to online banking; and
b. Initiation of transactions to transfer funds to other parties.
2. Enhanced controls for system administrators who can change access privileges, add users, change or reset passwords, add new payees, change transaction limits, change time of day access, register new access devices, etc.
Banks will need to work with their IT vendors to ensure that these two elements are in place or will be within a satisfactory time period.
Layered security consists of multiple controls, which may include:
1. Enhanced controls over account administration (an FFIEC minimum expectation) may include:
a. Requiring an additional authentication prior to implementing the change;
b. Requiring verification/confirmation of changes prior to implementing them;
c. Providing automatic customer notification (such as a text message or automated voice call to a cell phone) immediately after implementing an administrative change;
d. Preventing account holders from creating administrative users without bank approval; and
e. Eliminating all self-administration if the corporate customer doesn't meet minimum security standards established by the bank.
2. Screen display that shows customers the number of failed logins since the prior successful login and the date and time of their last login;
3. Fraud-detection and monitoring systems;
4. Dual customer authorization through different access devices;
5. Out-of-band verification of transactions (to/from a different access device);
6. Techniques to restrict transactions such as debit blocks, and debit filters;
7. Restrictions on account activity such as reasonable limits (based on historic activity) on transaction values, daily limits, who may receive funds, and time of day (and day of week) that high risk transactions such as wires and ACH originations may be initiated;
8. Tools that block connection from IP addresses known or suspected to be associated with fraudulent activities;
9. Policies to address potentially compromised customer equipment;
10. Enhanced controls (similar to those in #1 above) over account maintenance activities such as changes to postal and email addresses, phone numbers, and passwords, regardless if they are performed online, by mail, or by phone;
11. Customer security awareness education;
12. Use of USB devices that are read only and which function independently of the customer's computer's operating system, ensuring a secure connection to the bank's network; and
13. Enhanced challenge questions14 which would:
a. Use sophisticated questions ("out of wallet" information that isn't publicly available);
b. Require more than one question be answered correctly;
c. Include "trap" questions which the customer would recognize as nonsensical and clearly know the answer but a thief could easily guess a wrong answer15;
d. Establish a large pool of challenge questions; and
e. Prohibit the exposure of all challenge questions during one session.
For internal protection, the bank should ensure, at a minimum, the following controls:
1. An effective firewall and a process to evaluate, monitor, and validate firewall settings (and revise if necessary) on an appropriate schedule;
2. An effective patch management program that assesses patch effectiveness and implementation at least monthly; and
3. Additional security measures for computers used internally to access or manage the cash management system should include many of the controls recommended for customers that are listed in section P4.
P7. Review customer agreements.
Signed written agreements should be maintained with corporate customers using online banking services. Given the growing risks of corporate account takeovers, banks should have legal counsel that is familiar with corporate account takeover risks review their written agreements and consider including the following:
1. Roles and responsibilities for processing transaction requests and dispute resolution;
2. Minimum security standards that the bank requires the corporate account holder to use16;
3. A disclaimer and acknowledgement that no list of security practices can be all inclusive and foolproof for preventing theft;
4. The establishment of exposure limits through transaction limits, transaction frequencies, and types of payments that can be processed during the customer's normal course of business. Also consider:
a. Including the process for changing limits;
b. Including a provision authorizing the bank to not honor a transaction request if the bank in its sole discretion believes not processing it will protect the account holder from fraud (include examples that might indicate a transaction is fraudulent); and
c. Making an annual disclosure of the account agreement terms, mentioning any changes, and including a pamphlet on security awareness;
5. A disclaimer (absent any warranty or indemnification) that the risk of loss resides with the account holder if a fraudulent payment order is received by the bank in compliance with the bank's normal security procedures;
6. Requirement that the customer provide a list of the employees that are authorized to initiate files, or if the account holder is controlling account administration and accessibility then an acknowledgement from the customer of their responsibility and liability; and
7. Provisions for settling contract disputes. Consider requiring arbitration to settle contract disputes, or include a provision that provides the account holder with warranties or indemnification against corporate account takeover thefts, providing the account holder has followed specific practices.
P8. Contact your vendors to regularly receive information regarding reducing the risk of corporate account takeovers.
Corporate account takeovers are a persistent threat and the techniques to commit this crime will continue to be modified. Annually ask your vendors what controls they offer to reduce account takeover risks. Document this as part of the bank's annual risk assessment.
II. DETECT
Detection primarily occurs through:
1. Automated or manual monitoring systems;
2. Bank employee awareness; and
3. Notification from customers (that are aware of symptoms of computer breaches).
Management should evaluate all detection options to implement those which are most practical. Detection is closely associated with protection, as some measures to protect against electronic theft will also be an indication that a theft is being attempted.
D1. Establish automated or manual monitoring systems.
Account monitoring can help detect a theft before money is transferred. The most effective automated monitoring systems implement behavior-based transaction monitoring, sometimes called pattern recognition. As outlined in P6 above, the FFIEC Supplemental Guidance expects banks to implement, at a minimum, processes to detect anomalies related to initial login to online banking and initiation of transactions to transfer funds to other parties.
Things to evaluate:
1. Is the volume of corporate online banking transactions low enough for manual reviews?
a. If so, are there enough personnel (both as primary and as backup) available?
b. Can bank personnel develop manual procedures in a reasonable time period that evaluates key red flags listed in section D2 below?
2. Do current vendors offer or plan to offer automated transaction monitoring?
a. If so, will the monitoring detect the possible red flags listed in section D2 below?
b. What additional features or benefits do the vendors provide?
c. Can services be implemented within a reasonable time period?
d. How long does it take for the system to build a reliable pattern (predictive analytics) of activity to identify an anomaly?
e. Although less reliable than predictive analytics, is rule based fraud analysis available until a behavior pattern of data is established?
f. Does any behavior pattern analysis include monitoring account holder online behavior, such as keystroke speed, in addition to time of day activity or transaction-based factors?
g. Is potential structuring of transactions above preset limits detected as well as unusual frequency of transactions and abnormal time of activity (day of week and time of day)?
3. If current vendors do not offer automated monitoring, are there third-party vendor systems that will integrate with the bank's current systems?
4. How are bank personnel notified if an automated system detects an anomaly?
a. Are "suspicious" transactions blocked until an employee releases them?
b. Do employees receive notification in a timely manner?
Transaction monitoring for large transactions is one of the most effective techniques for detecting fraudulent transactions. Banks with a limited number of corporate account holders can implement manual reviews and block suspicious transactions (or obtain further confirmation from their customer). A checklist of characteristics to review, such as those in D2, should be part of any manual review procedures to help ensure consistent evaluations.
D2. Educate bank employees of warning signs that a theft may be in progress.
Employee awareness is essential in the detection of fraudulent account activity. Employees are generally the first and last line of defense. Employees with corporate account holder contact and especially those that process ACH and wire transactions need to know the types of customer inquiries and other warning signs that could indicate a theft is underway. They should be aware that any problems customers are having accessing or contacting the bank electronically might be a multi-prong attack to either divert the bank's attention from a theft in progress or to disrupt communications between the customer and the bank while the theft is occurring. Reviewing transaction security reports for unusual volume and dollar amounts is helpful and should be performed at least daily as some thefts occur over multiple days. However, this method only identifies a fraud after funds have left the bank.
A sample presentation to aid in educating bank employees was developed by the Task Force and is available on on the Texas Department of Banking website.
Red flags visible to the bank of a possible takeover of a business account include:
1. Configuration changes to cash management/online banking profiles:
a. New user accounts added;
b. New ACH batches or wire templates with new payees;
c. Changes to personal information;
d. Disabling or changing notifications; and
e. Changes to the online account access profile;
2. Unusual customer activity17:
a. Unfamiliar IP log-on address (especially if a foreign IP address);
b. Device ID not recognized during any previous log-on;
c. Log-on and/or viewing of balance or transaction history during unusual times of days;
d. Unusually small transaction amounts (example: $1.00 ACH, bill pay, or other transactions - especially if made at unusual time of day);
e. Unusual non-monetary request from customer via fax, email, or cash management system.
f. Unusual (non-typical) transfer of funds, especially if out of the bank. One-time bill pay to new payees;
g. ACH or wires to new payees or receivers and/or with unusual amounts.
h. Changes to the account and routing numbers of existing payees, not just a new payee name;
i. Unusual timing of transactions (based on the established transaction schedule of the corporate customer or random transactions submitted between traditional transactions);
j. Larger than usual transactions; and
k. Overseas transfers;
3. Compromised internal systems used by bank employees resulting in:
a. Inability to log into online banking system (thieves could be blocking the bank's access while they are making modifications to account settings);
b. Dramatic loss of computer speed;
c. Changes in the way web pages, graphics, text or icons appear;
d. Computer lock up so the user is unable to perform any functions;
e. Unexpected rebooting or restarting of computer;
f. Unexpected request for a one-time password (or token) in the middle of an online session;
g. Unusual pop-up messages, such as "try back later" or "system is undergoing maintenance";
h. New or unexpected toolbars and/or icons; and
i. Inability to shut down or restart.
In the event that any of the above items are noted, the bank's network administrator and/or the online banking system operator should be contacted for further investigation.
D3. Educate account holders of warning signs of potentially compromised computer systems. (This is similar to educating bank employees.)
Account holders should be the most vigilant in monitoring account activity. They have the ability to detect anomalies or potential fraud prior to or early into an electronic robbery. If your bank offers some of the automated notification features mentioned in P6, remind your customers those are designed as flags for them to notify you if they think they may have been compromised. Business account holders should be alert for the same red flags related to computer and network anomalies as bank employees.
Warning signs visible to a business or consumer customer that their system/network may have compromised include:
1. Inability to log into online banking (thieves could be blocking customer access so the customer won't see the theft until the criminals have control of the money);
2. Dramatic loss of computer speed;
3. Changes in the way things appear on the screen;
4. Computer locks up so the user is unable to perform any functions;
5. Unexpected rebooting or restarting of the computer;
6. Unexpected request for a one time password (or token) in the middle of an online session;
7. Unusual pop-up messages, especially a message in the middle of a session that says the connection to the bank system is not working (system unavailable, down for maintenance, etc.);
8. New or unexpected toolbars and/or icons; and
9. Inability to shut down or restart the computer.
III. RESPOND
R1. Update incident response plans to include corporate account takeover.
An incident response plan should include actions for stopping a corporate account takeover and should be reviewed at least annually. Update the plan to include the following:
1. Designate a fraud response committee with a specific member as the central point of contact for cyber threats. Ensure that:
a. All bank employees know that any phone calls from customers that might be about a corporate account takeover must be transferred to the designated employee as soon as possible;
b. The designated employee knows to convene the fraud response committee to evaluate the situation and take appropriate action;
c. The designated employee has been given authority to take immediate action and reverse or block suspected transactions;
d. Multiple backup personnel are in place in the event that the designated employee is unavailable. (These thefts exploit reduced staffing of holiday and vacation periods.); and
e. Account holders have provided a primary and secondary contact person along with after-hours phone numbers that the bank can call to confirm activity that appears suspicious;
2. Identify the recovery time frame and resources needed, including:
a. Number of employees available and trained to attempt to recover the money;
b. Resources/skills needed by the designated central point of contact at the bank; and
c. Resources needed by the recovery team;
3. Address customer relations/communication during an incident. Include these steps:
a. Identify the bank staff permitted to speak to the customer.
b. Script the initial employee communication with the customer;
c. Confirm account holder is aware that the bank is not automatically accepting liability; and
d. Identify the bank staff permitted to speak to the media;
4. Include criteria for contacting computer forensic specialists to review appropriate equipment as well as contact information; and
5. Include and maintain contact information for regulatory agencies, the United States Secret Service and other law enforcement agencies. They should be contacted as early as possible but without diverting resources from the initial recovery effort.
R2. "Immediately" verify if a suspicious transaction is fraudulent.
Bank employees should know how to contact account holder immediately. The customer's primary and secondary contact information including after-hours phone numbers are critical, not email addresses.
R3. "Immediately" attempt to reverse all suspected fraudulent transactions.
A bank's ability to recovery funds is reduced over time, measured in minutes, not hours. Thefts often include both wire transfer and ACH transfers, and could include other forms of transfers in the future. Be prepared to address all types. Have software available for immediate use to edit ACH files either onsite or through your correspondent or online banking vendor.18 Be aware that the Federal Reserve Bank (FRB) has different "processing times" for transactions and reversals. Reversals are sometimes not processed until hours or days after a transaction has already been sent and it is too late to recover the funds. No fraudulent transactions should be sent for processing along with a reversing entry under the presumption that the "reversal" will cancel the processing instruction.
R4. Immediately notify NACHA of the incident.
If an originating depository financial institution (ODFI) suspects that there has been an ACH data breach of consumer-level data, the NACHA Interim Policy on ACH Data Breach Requirements requires that:
To report an ACH data breach, use the ACH Data Breach Reporting Form located on the NACHA website. A NACHA representative will confirm receipt of your submitted information within 24 hours.
R5. "Immediately" notify the receiving bank(s) of the fraudulent transactions and ask them to hold or return the funds.
Once cyber thieves have transferred the stolen money to another bank, the thieves will attempt to move the money out as rapidly as possible. A process/plan must be in place for notifying the bank(s) that has received the stolen money and requesting a hold on those funds. The following steps should be taken:
1. Locate the phone number of the receiving bank(s) and contact their fraud department / fraud staff. If the fraud staff is unavailable, contact the bank’s ACH/funds transfer department;
2. Distribute the list of fraudulent transactions to a group of bank employees with calling assignments and instructions to call on the largest items first. Distribute the largest transactions among several employees to facilitate the quickest call-back on the largest transactions;
3. Remind bank employees making the phone calls that the employee at the receiving bank is crucial to recovery. If recovery effort is occurring after normal business hours or extends beyond normal business hours, ask the employee at the receiving bank for an after-hours phone number in case a call back is needed;
4. Document all calls with names, dates, and times;
5. Send a notice of fraudulent activity to the receiving bank(s). A sample form is available on the Texas Department of Banking website. This sample form is not endorsed, recommended or required by the Texas Department of Banking or the United States Secret Service. It is provided because it may be useful as a starting point in drafting an appropriate notice of fraudulent activity, with the assistance of bank counsel; and
6. If the receiving bank employee is reluctant to hold the funds, remind them that this is a theft and minutes are crucial in preventing the theft from being successful. Request to speak to a supervisor. If unable to resolve the issue, contact a law enforcement agency with whom you have already established contact. (All banks should already have contact information and should have introduced themselves to their local/area USSS and FBI representatives. If you do not have a working relationship with the USSS and/or FBI, you might want to ask your local law enforcement agency to place a call on your behalf to the USSS / FBI.) Explain the situation and ask if they will contact the receiving bank and request the funds be held as part of a fraud investigation. See R7 regarding contacting Law Enforcement.
R6. Implement a contingency plan to recover or suspend any systems suspected of being compromised.
When a system is suspected of being compromised, it is important to close off the method being used to commit the crime.
1. If it appears that user credentials of your customer have been compromised, consider immediately disabling your account holder's access to the online banking system.
2. If it appears that the bank's network was compromised, consider shutting down all online corporate banking activity (if that is feasible).
3. Depending on the size of the theft and potential losses, consider having forensic analysis performed on all suspected compromised systems as soon as possible to determine where, when and how the compromise occurred19. Consider paying for the analysis of your account holder's system to help in the bank's discovery of how the crime was committed.
R7. Contact law enforcement and regulatory agencies once the initial recovery efforts have concluded.
Law enforcement and regulatory agencies should be contacted once initial recovery efforts are complete. Have contact numbers for these agencies readily available in advance. In addition, a Suspicious Activity Report must be filed with the Financial Crimes Enforcement Network (FinCEN). Agencies to contact include:
1. United States Secret Service (or other federal law enforcement agency)20;
2. State and local law enforcement; and
3. State and federal bank regulatory agencies.
R8. Implement procedures for customer relations and documentation of recovery efforts.
Since the account holder can be the victim of a large theft, proper handling of the incident is important for customer relations, financial liability, and potentially public relations. Procedures should be in place regarding contacting customers and documenting all discussions. It is important to keep in mind that when an electronic theft is initially discovered, the source of the compromise is sometimes unknown.
1. Designate one employee in the bank as the central point of contact for communicating with the account holder and have a prepared script of the actions the bank is taking to retrieve their funds.
2. Document account holder discussions (note names, date, and times), especially how and when the account holder believes the compromise began.
3. Reassure account holders that the bank is diligently working towards a full recovery of the funds; however, there is no guarantee that a full recovery will be achieved.
RELATED ISSUES
Money Mules
Identifying Potential Money Mule Activity21
While it is important to prevent and detect thefts from your own corporate customers' accounts, it is also important to monitor for thefts that might be passing through your bank through a money mule account.
Warning signs that a bank customer could potentially be a money mule include:
1. New accounts opened with small deposit followed shortly by larger transfers via ACH or wire;
2. J-1 Visa student accounts receiving (unusually) large transfers;
3. New/unusual sources of transferred funds;
4. An existing account with a sudden increase in the number and dollar amount of deposits by ACH credit or wire transfer; and
5. An account that receives a large deposit followed by an immediate withdrawal, or around 10% less than the original deposit.
6. Destination of the monetary transfer that is not typical for the customer.
Internal Controls
Certain internal controls can be implemented should your bank be used to move stolen money through a money mule account. Consider the following controls:
1. Establish a central point of contact (and backup) for working with other banks that have account holders that have been victimized;
2. Determine how holds, returns and withdrawals/transfers will be allowed;
3. Determine what documentation will be required before holding or returning funds;
4. Evaluate the history of the account holder that is receiving the potentially stolen funds to determine if the incoming transactions are consistent with prior banking history; and
5. Identify any red flags indicating that the account is or has become a "money mule" account (see above).
APPENDIX A
Resources for Business Account Holders
1. The Better Business Bureau's 5 Steps to Better Business Cybersecurity;
2. The Small Business Administration's (SBA) 7 Ways to Protect Your Small Business from Fraud and Cybercrime;;
3. The Federal Trade Commission's (FTC) Tips & Advice: Data Security;
4. The National Institute of Standards and Technology's (NIST) Computer Security Resource Center;
5. The jointly issued “Fraud Advisory for Businesses: Corporate Account Takeover”from the U.S. Secret Service, FBI, IC3, and FS-ISAC available on the IC3 website; and
6. NACHA - The Electronic Payments Association's website has numerous articles regarding Current Threats for both financial institutions and banking customers.
APPENDIX B
Examples of Deceptive Ways Criminals Contact Account Holders
1. The FDIC does not directly contact bank customers (especially related to ACH and Wire transactions, account suspension, or security alerts), nor does the FDIC request bank customers to install software upgrades. Such messages should be treated as fraudulent and the account holder should permanently delete them and not click on any links.
2. Messages or inquiries from the Internal Revenue Service, Better Business Bureau, NACHA, and almost any other organization asking the customer to install software, provide account information or access credentials is probably fraudulent and should be verified before any files are opened, software is installed, or information is provided.
3. Phone calls and text messages requesting sensitive information are likely fraudulent. If in doubt, account holders should contact the organization at the phone number the customer obtained from a different source (such as the number they have on file, that is on their most recent statement, or that is from the organization's website). Account holders should not call phone numbers (even with local prefixes) that are listed in the suspicious email or text message.
APPENDIX C
Incident Response Plans
Since each business is unique, customers should write their own incident response plan. A general template would include:
1. The direct contact numbers of key bank employees (including after hour numbers);
2. Steps the account holder should consider to limit further unauthorized transactions, such as:
a. Changing passwords;
b. Disconnecting computers used for Internet banking; and
c. Requesting a temporary hold on all other transactions until out-of-band confirmations can be made;
3. Information the account holder will provide to assist the bank in recovering their money;
4. Contacting their insurance carrier; and
5. Working with computer forensic specialists and law enforcement to review appropriate equipment.
APPENDIX D
Information Security Laws and Standards Affecting Business Owners
Although banks are not responsible for ensuring their account holders comply with information security laws, making business owners aware of consequences for non-compliance if the information is breached can reinforce the message that they need to maintain stronger security. Breaches of credit and debit card information from retail businesses are common. Loss of that information or sensitive personal information can create financial and reputational risks for the business.
When providing security awareness education to corporate customers, banks may want to also alert business owners of the need to safeguard their own customers' sensitive information. Texas statutes related to safeguarding customer information include:
1. Chapter 521 of the Texas Business and Commerce Code, which is known as Identity Theft Enforcement and Protection Act, provides that penalties of up to $50,000 may be imposed for violations. See §521.053 Notification Required Following Breach of Security of Computerized Data; and
2. Chapter 72 of the Texas Business and Commerce Code relates to disposal of certain business records. This statute addresses paper and electronic records/information, including information stored on photocopy machines and printers.
The Payment Card Industry Security Standards Council was launched in 2006 to manage security standards related to card processing. Any merchant that accepts credit or debit cards for payment is required to secure their data based on the standards developed by the council. The PCI Security Standards Council's website notes that noncompliance may lead to lawsuits, cancelled accounts, and monetary fines. The website provides information for small business compliance.
October 25, 2023
| TO: | Chief Executive Officers of State-Chartered Trust Companies and |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Policy on Enforcement Actions for State-Chartered Trust Companies1 |
Overview
The purpose of this Memorandum is to set forth the circumstances under which enforcement actions are used by the Department of Banking (Department) with regard to the trust companies under its regulation, and to specify the general methodology which is followed. An enforcement action is designed to address and correct specific problems identified within the financial and operational affairs of a trust institution and is an essential element of effective regulation.
Public Disclosure of Enforcement Actions
Other than final Prohibition or Removal Orders, Department enforcement actions, whether informal or formal, are confidential. The Banking Commissioner (Commissioner) has discretion to publicize final Cease and Desist Orders, final Administrative Penalty Orders, Orders of Supervision, and Orders of Conservatorship if the Commissioner concludes that the release would enhance effective enforcement of the order.
Definitions
"Management" includes trust company officers as well as trust company directors.
"Regulatory responses" are actions taken by the Department in response to particular conditions at a trust company. They include informal communications as well as enforcement actions.
Policy for Implementing Enforcement Actions
Regulatory responses are initiated whenever the Department becomes aware of situations or issues that weaken the safety and soundness of an institution, or that arise from noncompliance with policies, procedures, regulations, or laws. To assure uniformity of action and to ensure that supervisory efforts are directed to trust companies exhibiting elevated risk profiles or other major deficiencies, the general policy of the Department is to initiate enforcement actions on trust companies with composite CAMEL ratings of "3," "4," or "5," and on trust companies with composite modified Uniform Interagency Trust Rating System (UITRS) ratings of "3," "4," or "5." (See the definition of trust company CAMEL ratings and UTRIS ratings in Supervisory Memorandum 1002.) Trust companies rated "1" or "2" generally do not warrant an enforcement action, although the Department may initiate an action depending on the specific circumstances of the institution. In particular, trust companies have Information Technology examinations and Bank Secrecy Act examinations that may reveal the need for an enforcement action even though the trust company has a composite rating of "1" or "2."
Enforcement actions often set forth the practices, conditions, and violations giving rise to the particular problems or weaknesses identified. The actions also outline specific corrective measures, often including appropriate time frames and goals for achievement. Specific types of enforcement actions available to the Department are outlined below in the section "Types of Enforcement Actions."
The Department's enforcement actions are not part of a hierarchy; they are not designed to build on one another. On a case by case basis, the Department thoroughly analyzes the situation at the trust company and designs the action it believes to be the most effective in curing the trust company's adverse conditions.
Trust Company Ratings
1-Rated Trust Companies
A composite "1" rating implies that a trust company is sound in all respects and that any weaknesses or deficiencies are so insignificant or immaterial that they pose no supervisory concern. Regulatory responses are generally limited to informal requests for future plans and/or a written response from the trust company regarding the examiner's findings as indicated in the report of examination.
2-Rated Trust Companies
Trust companies having a composite rating of "2" are fundamentally sound. Identified weaknesses or deficiencies are generally of a moderate nature and correction is attainable in the normal course of business. Regulatory responses are the same as for 1-rated trust companies; however, a Board Resolution may be initiated depending on specific circumstances encountered. In instances of repeated or willful law violations and/or continuing unsound trust company practices, the issuance of a stronger enforcement action may be warranted.
3-Rated Trust Companies
A composite "3" rating implies that a trust company has weaknesses which, if not corrected, could worsen into a more severe situation. Regulatory responses will most likely be enforcement actions which require remedial action.
4 and 5-Rated Trust Companies
Trust companies with composite ratings of "4" or "5," by definition, have problems of sufficient severity to warrant a strong regulatory response. An enforcement action such as a Cease and Desist Order is issued when there is evidence of unsafe and unsound practices or conditions. Exceptions to this policy are considered only when the condition of the trust company clearly reflects significant improvement resulting from an effective correction program or where individual circumstances militate against the appropriateness or feasibility of strong enforcement actions.
Types of Enforcement Actions
Enforcement actions are either formal or informal. With the exception of Determination Letters, informal enforcement actions are voluntary commitments made by trust company management designed to correct identified deficiencies and ensure compliance. Formal enforcement actions are generally more severe and result in an order issued by the Commissioner. Trust companies have a statutory right of appeal from formal enforcement actions to which they have not agreed.
A. Informal Enforcement Actions
Board Resolutions:
A Board Resolution is a statement adopted by the board of directors of a trust company that specifies corrective actions the board of directors will take. It is issued either on management's own volition or at the request of the Department. Board Resolutions are accepted from trust companies that exhibit only modest regulatory concerns.
Memorandum of Understanding:
A Memorandum of Understanding is an agreement between a trust company and the Commissioner that sets forth specific corrective actions to be undertaken by the board of directors of a trust company. This action is normally pursued with trust companies where management does not pose a significant regulatory concern, and where the Department believes management has the ability and the willingness to correct noted deficiencies. A Memorandum of Understanding is an agreement within the meaning of Texas Finance Code (TFC) Sections 181.002(a)(22)(B) and 185.002. Therefore, violation of a Memorandum of Understanding is grounds for issuance of a Cease and Desist Order, and, if other conditions are met, an Order of Supervision or Conservatorship. A Memorandum of Understanding may occasionally have a different title.
Determination Letter:
A Determination Letter is a warning issued pursuant to Section 185.001 of the TFC that the practices or condition of a trust company need immediate attention to avoid the issuance of an enforcement order under the TFC. A Determination Letter includes a listing of the requirements to abate the Commissioner's determination. A Determination Letter is normally used in a trust company where problems are of a serious nature, but the Commissioner believes that a more formal enforcement action may not be necessary to achieve correction.
B. Formal Enforcement Actions
Cease and Desist Order:
A Cease and Desist Order is issued pursuant to Section 185.002 of the TFC, demanding that an officer, employee, director, or manager of a trust company, or the trust company itself discontinue violations and/or unsafe and unsound practices, and take certain affirmative action as may be necessary to correct the conditions resulting from such violations or practices. A Cease and Desist Order is deemed necessary and appropriate for serious violations and unsafe practices. Management of a trust company subject to such an order would normally have demonstrated a disregard for safe and sound trust company practices and/or the lack of willingness or ability to correct deficiencies on their own. If a trust company agrees to enter into such an order, the order is called a Consent Order. The Commissioner may publish a final Cease and Desist Order or Consent Order pursuant to TFC Section 185.012.
Order of Removal or Prohibition:
A Removal or Prohibition Order is issued pursuant to Section 185.003 of the TFC if the Commissioner finds that a present or former officer, director, manager, managing participant, or employee, controlling shareholder or participant, or other person participating in the affairs of a state trust company has committed or participated in violations of law or agreements, and/or unsafe and unsound trust company practices, or made false entries, which caused certain effects, and which were done in other than an inadvertent or unintentional manner. Such orders have the effect of removing a person from office or employment or prohibiting a person from office, employment, or any further participation in the affairs of a state trust company or any other entity chartered, registered, permitted, or licensed by the Commissioner. The Commissioner must publish all final Removal and Prohibition Orders.
Order of Supervision:
Pursuant to Section 185.101 of the TFC, upon determining that a trust company is in hazardous condition as defined by TFC Section 181.002(a)(22), the Commissioner may issue an Order of Supervision without prior notice to appoint an individual as a supervisor of the trust company. Supervision is generally used in situations where the Commissioner has little confidence in the ability or willingness of the management of the trust company to follow safe and sound trust company practices. The authority of a supervisor, (enumerated under TFC Section 185.106), includes acting as the Commissioner's on-site observer and agent to assure, through veto authority and/or moral suasion, that the trust company is operated properly and in accordance with law and the enforcement action.
Order of Conservatorship:
A Conservatorship Order may be issued by the Commissioner pursuant to Section 185.102 of the TFC when it is determined that a trust company is in hazardous condition and immediate and irreparable harm is threatened to the trust company, its depositors, creditors, clients, shareholders or participants, or the public. Under TFC Section 185.107, the board of directors may not direct or participate in the affairs of the trust company during conservatorship. An appointed conservator immediately takes charge of the trust company, its property, books and records, and affairs on behalf of and at the direction and control of the Commissioner.
Administrative Penalties:
If a trust company or person commits applicable violations of law or a Commissioner's order (see TFC Section 185.009), the Commissioner may seek to assess monetary fines or penalties. The trust company or person is notified that a hearing will be held to determine whether administrative penalties will be assessed. Unless the violation is of a Commissioner's order, the trust company or person will be given an opportunity to correct the action and reduce or avoid the penalty. TFC Section 185.010(b) sets out factors the Commissioner must consider when setting the penalty and Section 185.010(c) sets out minimum and maximum penalty amounts.
Procedure for Implementing Enforcement Actions
Board Resolutions, Memorandums of Understanding, and Determination Letters are normally handled through written correspondence with the board of directors of a trust company. Nevertheless, they may require a special meeting of the board of directors. Other enforcement actions usually require a special meeting of the directorate of the trust company and generally such meetings are conducted by senior Department officials, including a member of the legal staff, at the Austin headquarters office.
Follow-up by examining personnel on enforcement actions is conducted in accordance with the Department's examination priorities unless variance from policy is deemed necessary. A trust company that is placed under Supervision or Conservatorship will have the appointed supervisor or conservator assist in monitoring compliance with enforcement orders.
November 1, 2021
| TO: | All State-Chartered Trust Companies |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Policy for Other Real Estate Owned (OREO) for State-Chartered Trust Companies 1 |
OVERVIEW
This policy statement interprets the state statutes and rules governing other real estate and defines the Department's classification policy for OREO for state-chartered trust companies.
Section 184.003-(a) of the Texas Finance Code (TFC) authorizes a state trust company to hold real estate other than its trust company premises with its restricted capital in limited circumstances. Title 7, Section 19.51 of the Texas Administrative Code (7 TAC §19.51) defines other real estate; describes the limited circumstances under which it can be lawfully acquired by a trust company using restricted capital; outlines the appraisal/evaluation requirements; establishes a procedure whereby additional expenditures may be made; defines a maximum holding period for each parcel; and outlines the minimum criteria for disposition efforts by a trust company.
It is important to note that 7 TAC §19.51 applies specifically to other real estate held with restricted capital, rather than secondary capital. However, trust company managers should follow safety and soundness by exercising sound judgement and prudence in holding OREO with secondary capital in accordance with TFC §184.003(e). Examiners will evaluate and consider the requirements of TFC §184.101(e) to determine the prudent standards, which may include acquiring initial and periodic valuations of the property.
OREO is considered held with restricted capital if at any time during the holding period, secondary capital is less than total book value of all OREO held by the trust company. Therefore, the trust company should reevaluate the capital structure quarterly to determine which type of capital is used to hold the property to determine which sections of 7 TAC §19.51 shall apply.
ACCOUNTING FOR OREO
Under 7 TAC §19.51, OREO, whether held with restricted capital or secondary capital, must be accounted for in accordance with regulatory accounting principles, defined in the TFC as generally accepted accounting principles (GAAP) as modified by rules adopted under the TFC or an applicable federal statute or regulation. In general, the accounting and reporting standards for foreclosed real estate are set forth in Financial Accounting Standards Board (FASB) Accounting Standards Codification (ASC) Topic 310-40, Troubled Debt Restructurings by Creditors, and ASC Topic 360-10-35, Impairment or Disposal of Long-Lived Assets.
APPRAISALS AND EVALUATIONS
Appraisals and Evaluations at Acquisition
As provided in 7 TAC §19.51(e), when OREO is acquired with restricted capital, a state trust company must substantiate the market value by obtaining an appraisal within 90 days from the date of the property’s acquisition by the trust company, unless extended by the banking commissioner. An evaluation may be substituted for an appraisal if the recorded book value of the OREO is $500,000 or less.
If the trust company has already obtained an appraisal or appropriate evaluation within the year prior to foreclosure, as provided in 7 TAC §19.51(e)(2), then a new valuation is not yet required.
If OREO is held with secondary capital, trust company management should evaluate and consider the prudent standards set forth in TFC §184.101(e) to determine if an appraisal or evaluation is necessary, and examiners will review the appropriateness of the trust company’s determination.
Subsequent Appraisal and Evaluation Requirements
An evaluation of the value of OREO held with restricted capital must be made at least once a year. An appraisal is required at least once every three years unless extended by the banking commissioner. An evaluation may be substituted for an appraisal if the recorded book value of OREO is $500,000 or less. The one-year period is measured from the date of the last appraisal or evaluation.
If any subsequent appraisal or evaluation indicates a reduction in the value of a property below the current book value, FASB ASC 360 requires the trust company to recognize the deficiency as a valuation allowance against the asset, which is created through a charge to expense. For reporting purposes, the reserve account should be netted against the book value of the OREO and is not considered as part of the trust company’s capital structure. The valuation allowance should thereafter be increased or decreased (but not below zero) through charges or credits to expense for changes in the asset’s value or estimated selling costs. In no event, however, should the carrying value of the property be increased to an amount greater than the original book value at the time of acquisition or transfer to the other real estate category.
Maintenance of a general reserve for losses on the sale of OREO and write-downs below appraised value are not consistent with generally accepted accounting principles. Write-downs below appraised value should be supported by reasonable documentation.
If upon a quarterly evaluation of its capital, a trust company determines that OREO ceases to be held with secondary capital and is held in any part with restricted capital, then the appraisal and evaluation rules of this section will apply.
If OREO is held with secondary capital, trust company management should evaluate and consider the prudent standards set forth in TFC §184.101(e) to determine if an appraisal or evaluation is necessary, and examiners will review the appropriateness of the trust company’s determination.
Obtaining an Appraisal Extension
The banking commissioner may extend the deadline for when an appraisal is required on OREO property per 7 TAC §19.51(e)(1) and (3). Requests for an extension of the deadline for obtaining an appraisal within 90 days of acquisition of OREO or the deadline to obtain an appraisal of OREO property every three years must be submitted to the commissioner in writing. Extension requests must include information necessary to support the reason(s) for the extension. The required form for submitting an extension request, “Application to Extend Appraisal Deadline,” is available under the Applications & Forms section of the Department’s website.
Decisions to approve or deny requests for the extension of a deadline to obtain an appraisal will be made on a case-by-case basis after considering all relevant factors of the transaction. Reasons for granting an extension vary but may include a pending written sales agreement that is expected to close within the next 90 days.
HOLDING PERIOD FOR OREO
Holding Period Limit
Texas statutes require that if OREO is held with restricted capital, a state-chartered trust company must dispose of the OREO within five years from the date the real property:
• is originally acquired or transferred to that asset category;
• ceases to be used as a trust company facility; or
• ceases to be considered future expansion property as a trust company facility as provided in §184.002(b) of the TFC2.
When a state chartered trust company acquires OREO held in restricted capital as the result of a merger with or an acquisition of another institution, the holding period of the newly acquired OREO commences on the date of merger or acquisition. If an entity converts to a state-chartered trust company, the OREO property held by the entity at the time of conversion will be considered acquired or transferred to OREO as of the conversion date.
The banking commissioner may grant an extension of time for disposing of an OREO property if, in the commissioner's opinion, the trust company has made a good faith effort to dispose of the property, or if the commissioner determines that disposal of the property within the initial five-year period would be detrimental to the trust company. Should the extension request be denied, failure to dispose of the property may result in citing a violation of 7 TAC §19.51 at the next examination. Examining personnel will review the trust company's efforts to dispose of each property and evaluate compliance with the regulation. Continued noncompliance and/or absence of good faith efforts to dispose of the property may result in the issuance of an enforcement action to effect correction.
If upon a quarterly evaluation of its capital, a trust company determines that OREO ceases to be held with secondary capital and is held with restricted capital, then the holding period limit of this section applies from the date the restricted capital was utilized for holding.
Holding Period Extensions
All requests for extensions of holding periods must be in writing. The required form for submitting an extension request, "Application to Extend Holding Period for OREO," is available under the Trust Companies section of Applications & Forms on the Department's website.
Extensions for future expansion will be handled on a case-by-case basis. Primary factors that are considered by the Department in evaluating compliance with the law and in deciding whether to approve requests for extensions of holding periods include the following:
• Carrying value of the property in relation to current market value, asking price, and purchase offers received;
• Length of time the property has been held and reason(s) why it has not been sold;
• Income and expenses associated with ownership and maintenance of the property for: (i) all prior years; (ii) the current year; and (iii) an estimate of next two years; and
• Potential or known contingent liabilities (e.g., environmental concerns, litigation, etc.) relative to the holding of the property.
Extensions for holding property, other than future expansion, are not normally granted if the extended time exceeds ten years from the original date of acquisition (or the date a former trust company facility was reclassified as OREO).
DISPOSAL OF OREO
Minimum Documentation Requirements
Under 7 TAC §19.51(h), trust companies are expected to maintain documentation showing compliance with the regulation and good faith efforts to dispose of each parcel of OREO held with restricted capital. Required minimum documentation includes:
• Specific action plans for disposal of each parcel of OREO showing review and approval by the trust company's board of directors or a designated committee thereof. Such action plans and reviews should be recorded in the official records of the board or committee meetings;
• Listing agreements executed with real estate agents/brokers detailing the asking price and terms of sale. If a property is not listed, adequate documentation showing the trust company's own marketing efforts must be maintained;
• Documented reasonableness of the asking price relative to the appraised market value of the property;
• Records of all verbal and/or written inquiries and offers received for each property;
• Decisions made and actions taken by the board, or designated committee, on all verbal or written offers received; and
• Files of all advertising media employed, e.g., signs, publications, and broadcast media.
Accounting for Disposition of OREO
FASB issued Accounting Standards Update (ASU) 2014-09 in May of 2014 which created ASC Topic 606, Revenue from Contracts with Customers, and amended ASC Topic 610, Other Income.3 Per ASU 2014-09, sales of OREO should be accounted for in accordance with ASC Subtopic 610-20 Other Income – Gains and Losses from the Derecognition of Nonfinancial Assets.4
Exchange, Acceptance or Additional Purchases
With the prior written approval of the banking commissioner, a trust company may exchange or acquire real estate or personal property in order to avoid or minimize loss potential on OREO. Alternate or additional real estate so acquired should be accounted for on the trust company's books as OREO, if acquired with restricted capital, and the initial holding period for such properties will be measured from the date legal title to the original OREO was first acquired by the trust company. Disposal of personal property should be within 90 days of acquisition.
Criteria for Exchanging or Acquiring Additional OREO
The commissioner's decision to approve or deny requests for the exchange or acquisition of real estate held with restricted capital will be made after considering all relevant factors of the transaction, particularly the following:
• Has the trust company demonstrated good faith efforts to dispose of the original OREO?
• Has the trust company reduced its loss exposure as evidenced by current market value appraisals of the properties involved?
• Does the trust company have specific plans to market the newly acquired property?
• What is the amount of cash to be received by the trust company in connection with a transaction where the trust company is accepting an alternate parcel of real estate as partial consideration in the sale of existing OREO?
• Will the nature of the original OREO be changed?
• What is the trust company's aggregate investment in the existing OREO plus the property to be acquired in relation to equity capital?
Transfer of OREO to Affiliate
7 TAC §19.51(i) of the TAC addresses the various options for disposition of OREO.
Under 7 TAC §19.51(i)(4), a trust company may dispose of real estate by transferring the real estate for market value to an affiliate. This is subject toTFC §183.109. In addition, if the trust company is a bank subsidiary or affiliate, then the transfer may also be subject to applicable federal law, including 12 U.S.C. §§371c, 371c-1, and 1828(j) (relating to transactions among banks, bank affiliates, and bank subsidiaries). Section 183.109 of the TFC requires that a trust company may not directly or indirectly sell or lease an asset of the trust company to an officer, director, manager, managing participant, or principal shareholder or participant of the trust company or of an affiliate of the trust company without the prior approval of a disinterested majority of the board. If a disinterested majority cannot be obtained, the prior written approval of the banking commissioner is required.
CLASSIFICATION STANDARDS
The Department evaluates OREO held with restricted capital in the same manner as any other trust company-owned asset, utilizing the same criteria for assessing quality and propriety. As warranted, adverse criticism is assigned in a manner consistent with the uniform classification standards used by state and federal bank regulatory agencies.
Income producing properties may be excluded from classification provided the annual net cash flow from the property yields a market rate of return on the entire book amount. "Net cash flow" is defined by GAAP as gross cash receipts less the cost of insurance, taxes, management fees, and other operating costs. For purposes of the classification treatment outlined below, the market rate of return must equal or exceed the average yield on real estate loans as reflected in the trust company's most recent reports of condition and income plus 100 basis points. If book value is materially less than the market value of the property due to previous unsubstantiated write downs, for classification purposes the rate of return is calculated using the market value of the asset.
Suggested classification treatments for OREO properties held with restricted capital are shown below and assume that the examiner has no material reservations with the validity of the appraisal or its assumptions. In the case of income producing properties, the assumption is also made that there are no significant reservations about the quality and continued viability of the future cash flow stream of the property. However, if an examiner has reasonable cause to question the appraisal, its assumptions, or the future cash flow stream, more severe classifications than those shown may be assigned.
Income Producing Properties
Pass - Consider income and expenses generated by the property and any other factors affecting the probability of loss exposure.
Substandard - Consider income and expenses generated by the property and any other factors affecting the probability of loss exposure.
Doubtful - N.A. (this classification is generally not appropriate).
Loss - Excess of book value over current appraised value.
Non-income Producing Properties
Substandard - Current appraised value.
Doubtful - N.A. (this classification is generally not appropriate).
Loss - Excess of book value over current appraised value.
May 11, 2015
| TO: | All State-Chartered Banks |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Bargain Purchases and Assisted Acquisitions |
Purpose
The Texas Department of Banking generally agrees with the federal Interagency Supervisory Guidance on Bargain Purchases and FDIC- and NCUA-Assisted Acquisitions, issued June 7, 2010 1 (Federal Guidance). Since its issuance, the Department has been applying the Federal Guidance in approval of state bank acquisitions but with certain differences. This Supervisory Memorandum clarifies the differences between the Department´s treatment of bargain purchases and that described in the Federal Guidance.
Supervisory Considerations
The Federal Guidance addresses supervisory considerations related to business combinations that result in bargain purchase gains and the impact such gains have on the acquisition approval process. The Federal Guidance indicates that an acquiring bank´s primary federal regulator shall have the authority to approve applications for acquisitions and business combinations and apply conditions of approval regarding capital preservation, dividend limitations, auditing requirements, independent valuations, and lending limit requirements. Such guidance does not diminish the Department´s separate authority under state law to establish conditions for approval of, and to approve, state bank acquisitions and business combinations.
Neither this Supervisory Memorandum nor the Federal Guidance add to or modify existing regulatory reporting requirements issued by the Department, the federal bank regulatory agencies, other regulatory agencies, or current accounting requirements under generally accepted accounting principles (GAAP). Institutions and examiners should refer to the relevant GAAP literature and regulatory reporting instructions for appropriate accounting and reporting guidance.
Conditions in Approval of Acquisitions
The Department generally will apply the Federal Guidance in considering state bank applications for Banking Commissioner approval to acquire other financial institutions, substantially all of the assets of other financial institutions, or other business combinations, except as identified below. This Supervisory Memorandum uses the same defined terms as used by the Federal Guidance unless otherwise noted.
The Commissioner will impose the following conditions in approval of any acquisition by a state bank involving bargain purchase gains. Prior to the end of the conditional period and validation of the bargain purchase gain as set forth in the Federal Guidance, an acquiring state bank will be required to exclude such bargain purchase gain from calculation of its capital for purposes of its:
(1) dividend-paying capacity;
(2) legal lending limit under:
a. Chapter 34, Subchapter C, of the Texas Finance Code (TFC); and
b. the legal lending limit rules in Chapter 12, Title 7 of the Texas Administrative Code (TAC); and
(3) all investment limits established in TFC Chapter 34, Subchapters A and B, and the investment limit rules in 7 TAC Chapter 12, including the limits on:
a. investments in bank facilities and other real estate;
b. securities investments; and
c. investments in bank subsidiaries.
The Commissioner therefore will impose the dividend limitations and legal lending limit conditions that the Federal Guidance states federal bank regulatory agencies may impose in their approvals of acquisitions by state banks.
An acquiring state bank must seek approval from the Commissioner, in its acquisition application, if it wishes to include some or all of the bargain purchase gain in calculation of its capital prior to the end of the conditional period for purposes of its dividend-paying capacity, its legal lending limit or its investment limits. The Commissioner will consider the following factors in determining whether to approve such request:
(1) The quality and extent of the acquiring bank's due diligence review of the assets to be acquired from the other financial institution, including:
a. The percentage of the loan portfolio reviewed; and
b. Whether the acquiring bank employed a qualified third party to assist in its due diligence review;
(2) The competence and expertise of the acquiring bank;
(3) The relationship of the total value of assets to be acquired to the original capital of the acquiring bank; and
(4) Any other factors that the Commissioner determines to be relevant.
In addition, in its acquisition application, an acquiring state bank must address certain post-acquisition legal lending limit issues as follows:
(1) Provide assurances to the Department that the bank has specifically considered and identified the impact of the assets to be acquired on its legal lending limit following the acquisition.
(2) If the bank to be acquired, or whose assets are to be acquired, is chartered by another state or is a national bank, then, when determining the impact referred to in the previous sentence, consider the differences in any legal lending limit law applicable to the acquired institution, or the loans to be acquired. For example, the acquiring bank should consider whether another state's law, or the law applicable to a national bank, differs from the Texas legal lending limit law governing attribution of loans of related persons or entities to a particular borrower and aggregation of such loans to that same borrower.
(3) Determine, to the extent possible, whether the institution to be acquired has, or any of its loans have, borrowers in common with the acquiring bank, and identify such borrowers and their loans, which, if aggregated, might exceed the legal lending limit for the bank following the acquisition.
Within 90 days after consummation of an acquisition, the acquiring bank must provide a report to the Board of Directors identifying all loans purchased in the acquisition that are non-conforming under 7 TAC §12.10(a)(3).
Regulatory Reporting
Although the Department will not consider the purchase money gain in calculating various investment limits, management remains responsible for filing regulatory reports in accordance with the requirements in effect as of the filing date. Updates to the Financial Account Standards Board (FASB) Accounting Standards Codification topics discussed in the Federal Guidance as well as updates to instructions for preparing Consolidated Reports of Condition and Income (Call Reports) should be followed.
Questions about this Supervisory Memorandum may be directed to the Director of Bank and Trust Supervision at 512-475-1300.
July 17, 2024
| TO: | All Institutions Regulated by the Texas Department of Banking |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Effect of Criminal Convictions on Licensing1 |
OVERVIEW
Texas Occupations Code §53.021(a) grants the Texas Department of Banking the authority to suspend or revoke a license, disqualify a person from receiving a license, or deny to a person the opportunity to take a licensing examination on the grounds that the person has been convicted of: (1) an offense that directly relates to the duties and responsibilities of the licensed occupation; (2) an offense that does not directly relate to the duties and responsibilities of the licensed occupation and that was committed less than five years before the date the person applies for the license; (3) an offense listed in 42A.054, Code of Criminal Procedure1; or (4) a sexually violent offense, as defined in Article 62.001, Code of Criminal Procedure.
Pursuant to Texas Occupations Code §53.025, the Department is issuing the following guidelines regarding section 53.021(a)(1), stating the reasons a particular crime is considered to directly relate to the duties and responsibilities of a particular license and any other criterion that affects the licensing decisions of the Department. The Department currently charters or issues licenses or permits to the following entities: state-chartered banks and foreign bank agencies, trust companies, money services businesses, sellers of prepaid funeral benefits, and perpetual care cemeteries. As to permits to sell or accept money for prepaid funeral benefits, crimes directly related to the fitness for those permits are set out in 7 Texas Administrative Code §25.31(c).
POLICY
Pursuant to Texas Occupations Code §53.021(a)(1), the Department may suspend or revoke a license, disqualify a person from receiving a license, or deny a person the opportunity to take a licensing examination on the grounds that the person has been convicted of an offense that directly relates to the duties and responsibilities of the licensed occupation. These guidelines are intended to reflect the Department’s overarching duty to regulate the fiduciary and financial responsibilities of its licensees and apply to felony convictions of officers, directors, owners, and the entity itself.
State-Chartered Bank and Foreign Bank Agency
Operating a state-chartered bank or foreign bank agency involves or may involve activities such as receiving money from consumers, remitting money to third parties, maintaining accounts, making representations to consumers regarding the terms of loans, repossessing property without a breach of the peace, maintaining goods that have been repossessed, collecting amounts due in a legal manner, and foreclosing on real property in compliance with state and federal law. Consequently, the following crimes are directly related to the duties and responsibilities of a licensee and may be grounds for denial, suspension, or revocation:
A. any offense involving dishonesty or theft;
B. any offense that involves misrepresentation, deceptive practices, or making a false or misleading statement (including fraud or forgery);
C. any offense that involves breach of trust or other fiduciary duty;
D. any offense that involves drug trafficking, terrorist funding, money laundering or a related financial crime;
E. any violation of the Bank Secrecy Act or USA PATRIOT Act;
F. any criminal violation of a statute governing debt collection;
G. failure to file a government report, filing a false government report, or tampering with a government record;
H. any greater offense that includes an offense described in subparagraphs (A) - (G) of this paragraph as a lesser included offense;
I. any offense that involves intent, attempt, aiding, solicitation, or conspiracy to commit an offense described in subparagraphs (A) - (H) of this paragraph.
Trust Company
Operating a trust company involves or may involve activities such as acting as trustee and performing fiduciary duties per written agreement or by court order, receiving money and other property for investment in real or personal property, acting as executor, administrator, or trustee of the estate of a deceased person, acting as a custodian, guardian, conservator, or trustee for a minor or incapacitated person, receiving for safekeeping personal property, acting as custodian, assignee, transfer agent, escrow agent, registrar, or receiver, acting as investment advisor, agent, or attorney in fact, or engaging in a financial activity or an activity incidental or complementary to a financial activity. Consequently, the following crimes are directly related to the duties and responsibilities of a licensee and may be grounds for denial, suspension, or revocation:
A. any offense involving dishonesty or theft;
B. any offense that involves misrepresentation, deceptive practices, or making a false or misleading statement (including fraud or forgery);
C. any offense that involves breach of trust or other fiduciary duty;
D. any offense that involves drug trafficking, terrorist funding, money laundering or a related financial crime;
E. any violation of the Bank Secrecy Act or USA PATRIOT Act;
F. failure to file a government report, filing a false government report, or tampering with a government record;
G. any greater offense that includes an offense described in subparagraphs (A) - (F) of this paragraph as a lesser included offense;
H. any offense that involves intent, attempt, aiding, solicitation, or conspiracy to commit an offense described in subparagraphs (A) - (G) of this paragraph.
Money Services Business
A. any offense involving dishonesty or theft;
B. any offense that involves misrepresentation, deceptive practices, or making a false or misleading statement (including fraud or forgery);
C. any offense that involves breach of trust or other fiduciary duty;
D. any offense that involves drug trafficking, terrorist financing, money laundering or a related financial crime;
E. any violation of the Bank Secrecy Act of USA PATRIOT Act;
F. failure to file a government report, filing a false government report, or tampering with a government record;
G. any greater offense that includes an offense described in subparagraphs (A) - (F) of this paragraph as a lesser included offense;
H. any offense that involves intent, attempt, aiding, solicitation, or conspiracy to commit an offense described in subparagraphs (A) - (G) of this paragraph.
Seller of Prepaid Funeral Benefits
See 7 Texas Administrative Code §25.31(c).
Perpetual Care Cemetery
Operating a perpetual care cemetery involves or may involve activities such as making representations to prospective purchasers of burial rights, collection and investment of perpetual care trust funds, continuing the general maintenance and care of the cemetery property, and maintaining adequate records as required by 7 Texas Administrative Code §26.2. Consequently, the following crimes are directly related to the duties and responsibilities of a licensee and may be grounds for denial, suspension, or revocation:
A. any offense involving dishonesty or theft;
B. any offense that involves the desecration of a cemetery, abuse of a corpse, or related crime;
C. any offense that involves misrepresentation, deceptive practices, or making a false or misleading statement (including fraud or forgery);
D. any offense that involves breach of trust or other fiduciary duty;
E. failure to file a government report, filing a false government report, or tampering with a government record;
F. any greater offense that includes an offense described in subparagraphs (A) - (E) of this paragraph as a lesser included offense;
G. any offense that involves intent, attempt, aiding, solicitation, or conspiracy to commit an offense described in subparagraphs (A) - (F) of this paragraph.
Additional Factors
In determining whether a criminal offense directly relates to the duties and responsibilities of holding any of the above charters, licenses, or permits, the Department will consider the following factors, as specified in Texas Occupations Code § 53.022:
In determining whether a conviction for a crime renders an applicant or a licensee unfit to be a licensee, the Department will consider the following factors, as specified in Texas Occupations Code §53.023:
The purpose of these guidelines is to give notice to the types of crimes that may result in adverse action. Moreover, these guidelines are not intended to be an exhaustive list nor do they prohibit the Department from considering crimes not listed herein. After due consideration of the factors listed above, the Department may find that a conviction not described herein renders a person unfit to hold a license.
July 17, 2024
| TO: | All State-Chartered Banks and Trust Companies |
| FROM: | Charles G. Cooper, Banking Commissioner |
| SUBJECT: | Permissible Uses of “Bank” and Related Terms in Marketing and Other Limits Related to Marketing Regulated Financial Services1 |
PURPOSE
The Texas Department of Banking (Department) is required to enforce certain Texas laws regarding advertising of regulated financial services. This Supervisory Memorandum (Memorandum) interprets the state statutes governing the marketing of regulated financial services, clarifies the requirements for compliance, and addresses various legal parameters for marketing regulated financial services.2
To prevent deceptive advertising and protect the public, the Texas Finance Code (TFC) limits marketing of regulated financial services by unregulated entities. For instance, companies unauthorized to engage in the business of money transmission may not advertise, solicit, or represent that they engage in the business of money transmission per Section 152.101 of the TFC. Similarly, Section 31.005 of the TFC prohibits the use of “bank,” “banking,” and related terms in marketing by non-banks in a manner indicating those entities are engaged in banking. This Memorandum discusses the extent of these limits and describes certain permissible marketing activities that would not violate these laws.
These laws apply to all persons and entities that are located in Texas, provide services to persons or companies located in Texas, advertise services to persons or companies located in Texas, or otherwise purposefully direct their activities toward, or have substantial connections with, Texas. Legal compliance can be achieved and maintained with reasonable effort, and the Department sincerely appreciates the continued and long-standing voluntary observance of these laws by the vast majority of financial service entities.
This Memorandum is not intended to address the marketing practices of any particular person, company, or case.
The Department regulates banks and money transmitters, as well as other financial service providers. There have been various instances in which unauthorized entities are holding themselves out as banks or money transmitters in violation of the TFC.
In most instances, these vendors provide banks and other regulated entities with information technology services, particularly user interface systems for account access such as websites and mobile phone applications. While such technology outsourcing is not new in the financial services industry, a recent trend has arisen where these non-bank vendors hold themselves out to the public as actual banks or providers of regulated money services without complying with applicable laws on banking and money services. For example, non-bank ABC Corp. will provide XYZ Bank deposit account customers with access to XYZ banking services through ABC’s ABC-branded interface, and ABC will hold itself out as a “bank.” This is illegal—ABC cannot hold itself out as a bank since ABC is not a bank.
The laws of many states, including Texas, prohibit unregulated companies both from providing regulated financial services and from falsely claiming to be regulated financial service providers.3 These marketing laws protect both consumers and lawful providers of regulated financial services by preventing deceptive advertising and enabling users of financial services to make informed decisions.
REVIEW OF APPLICABLE LAW AND REGULATION
The two primary sources of law in question are the Texas Banking Act, Chapters 31 through 59 of the Texas Finance Code and the Money Services Modernization Act, Chapter 152 of the Texas Finance Code. Some of the pertinent requirements of these laws are reviewed below to provide context before providing interpretations. By further explaining these laws, the Department hopes to assist organizations with compliance.
Money Transmission Law and Regulation
Many financial services involve regulated “money transmission.” As defined in the Money Services Modernization Act, “money transmission” means selling or issuing payment instruments and/or stored value to a person located in this state, and recieving money for money transmission services from a person located in this state.4 "Receiving money for money transmission services" has been interpreted to mean (a) the receipt of money or monetary value by any means, and (b) a reciprocal promise to make money or monetary value available at a later time or different location. Money-transmission does not require transmission to a third party; it can be a two-party transaction. Various money management services constitute money transmission if those services involve receiving money from customers and promising to repay those customers that money or value at a later time.
Unless licensed or exempt, a company (or person) may not engage in the business of money transmission in Texas or advertise, solicit, or represent that it engages in the money transmission business.5 The prohibition against advertising money transmission applies regardless of whether actual activities and operations constitute money transmission.
However, an unlicensed company can hold itself out as a money transmitter if an exemption applies. For example, an exemption may apply if the unlicensed company is:
A federally insured depository financial institution (collectively, "banks"); 6
An agent of a federally insured depository financial instituion;7
An authorized delegate appointed by a licensed money transmitter, or an intermediary working on behalf of a licensed money transmitter; 8
A person appointed as an agent of a seller of goods or services, other than money transmission services, to collect and process a payment to that seller,9 or
Another specifically authorized type of regulated entity, such as a Texas-chartered trust company, a registered securities dealer, a licensed attorney, a licensed title company, or a registered debt management service provider.10
Many of these exemptions have reasonable, yet important, conditions and requirements that protect the interests of the public, such as by ensuring customers have recourse against both the exempt service provider and its sponsoring bank, licensed money transmitter, or principal retailer if the exempt service provider misappropriates or mishandles customer funds.11
Bank Law and Regulation
The Texas Banking Act, like the Money Services Modernization Act, states that a non-bank shall neither “conduct the business of banking” nor “represent to the public that it is conducting the business of banking.”12
The Texas Banking Act specifically addresses the use of “bank”, or related terms in the context of financial service marketing. A non-bank may not “use the term ‘bank,’ ‘bank and trust,’ or a similar term” in its advertising “in a manner that would imply to the public that the person is engaged in the business of banking in this state.” 13
However, unlike the Money Services Modernization Act, the Texas Banking Act has no exclusions or exemptions permitting non-bank agents, delegates, or vendors of banks to conduct the business of banking, or to hold themselves out or market themselves as “banks.” Non-bank vendors to banks cannot advertise those vendors’ own “banking” services or falsely represent that such non-bank entities are “banks.”
COMPLIANCE WITH APPLICABLE LAW AND REGULATION
As previously noted, the Department has become aware of various companies, particularly technology companies that are vendors to banks and are violating laws regarding marketing as a “bank” and other financial services. At the same time, other companies manage to accurately and competitively market similar services without violating these financial service marketing laws. To achieve voluntary compliance without litigation or other unnecessary efforts, the Department is issuing this Memorandum relating to marketing restrictions and permissible marketing activities under both the Money Services Modernization Act and the Texas Banking Act.
Relating to Marketing Money Transmission Services
Compliance with the Money Services Modernization Act restrictions on marketing requires adherence to the following basic principles (among others):
“Send your money" service is a regulated money transmission business in Texas. Money transmission occurs where a company receives funds and promises to make those funds available at a later time or different location.
Advertising “send your money" services is regulated in Texas. Since these services are money transmission, and advertising money transmission is regulated, advertising "send your money" is regulated.
“Send your money" is a regulated service even if someone else facilitates the transmission. Advertising for money services is regulated, even if the money services are outsourced to a third-party. (And this third-party may need to be licensed or exempt as well.)
Companies advertising or providing money transmission services without a license must qualify for an exemption or exclusion.
Relating to Permissible Marketing of Banking Services and Use of “Bank,” Banking” or Related Terms in Marketing
As noted above, the Texas Banking Act prohibits all non-banks from holding themselves out as “banks” in a manner indicating that such entities are engaged in banking. The chief concern here is with providers of financial services—blood banks and food banks may continue to use the term “bank” in their non-financial activities.
However, when the goods, services, or products in question relate to finance or financial services, non-banks are prohibited from advertising themselves as banks. While a non-bank agent of a bank may be exempt from the Money Services Modernization Act and therefore permitted to both provide money transmission services and advertise such services, those advertisements still cannot falsely claim that the non-bank is a “bank” or engaged in “banking.”
A non-bank cannot call itself a bank under the Texas Banking Act. For example, ABC Corp., a non-bank, cannot call itself “ABC Bank” or have a website such as www.abc-bank.com. There is no permissible way to offer a “white-labeled14 bank account” or white-labeled banking services under circumstances where a non-bank holds itself out as the entity offering a “bank” account or other banking services.
Likewise, a non-bank’s use of “bank” or “banking” in advertising violates the Texas Banking Act in the following examples:
A television advertisement for ABC Corp., a non-bank, stating that ABC offers “mobile banking” or that ABC “provides a mobile banking account”;
A website for ABC with “banking” tabs or statements that ABC provides “banking made awesome” and that ABC customers are “more than a bank balance”; or
A telemarketing campaign by ABC describing ABC as a “banking platform” that offers “safe banking” or “a better way to bank.”
Non-banks can comply simply by not using words like “bank” or “banking” in marketing in a manner implying that the non-bank is engaged in banking. Non-banks can accurately describe the non-banking services they provide, such as bank account management software. The following “bank”-related marketing statements by non-bank ABC will not be viewed as implying that ABC is a bank as long as all of ABC’s related marketing materials reasonably identify the banks providing the actual banking services:
ABC offers “access to mobile banking” or “provides access to your mobile banking account”;
ABC provides “bank account management made awesome”; and
ABC is a “banking management platform” that offers “safe bank account control” or “a better way to access your bank.”
In addition, the use of “bank” or related terms in non-bank advertising does not imply the non-bank is providing banking services if the sponsoring bank is at least as prominent as the non-bank within the context of those “bank” and related terms. For instance, the examples above will be viewed as compliant if modified to disclose that ABC’s sponsor XYZ bank is providing the banking services:
The television ad can state that ABC offers “mobile banking thru XYZ” or that ABC “is an XYZ mobile banking account”;
A website branded by ABC can have “XYZ banking” tabs or statements that ABC provides “XYZ banking made awesome” and that ABC customers are “more than an XYZ bank balance”; or
A telemarketing campaign by ABC can describe ABC as an “XYZ banking platform” that offers “safe banking with XYZ” or “a better way to bank with XYZ.”
Alternatively, the marketing materials as a whole can be co-branded by XYZ and ABC, so that their names and logos are featured with equal prominence and plural statements such as “we offer mobile banking,” “bank with us,” and “we make banking awesome” are used. Again, all marketing statements relating to regulated financial services should reasonably identify the entity providing the regulated financial services to avoid illegal solicitation of regulated financial services by unauthorized entities.
Relating to Permissible Joint Marketing of Regulated Financial Services by Corporate Affiliates
The Department has noted that regulated financial services are often collectively using tradenames and trademarks common among a family of affiliated corporations. For example, “XYZ Holdings Corp.” may wholly own subsidiary XYZ Money Services Corp. XYZ Holdings is not licensed, excluded, or exempt from money transmission licensing, but XYZ Money Services is. Both entities collectively advertise various financial services, including regulated money transmission services, simply as “XYZ” without explaining which entity provides which services.
In such circumstances, an advertisement that states “XYZ can manage your money and pay your bills” could be construed as XYZ Holdings illegally advertising that this particular entity provides money services.
However, the Department has determined such collective advertising for banking services, money transmission services, or other regulated financial services by affiliated companies under a common trade name or mark will not be considered to constitute illegal advertising of regulated financial services by the non-exempt or unlicensed affiliates as long as all of the following conditions are met:
At least one of the companies in question is licensed or exempt from applicable licensing for any regulated financial services being advertised;
Any actual regulated financial services are only provided by the applicable licensed, excluded, or exempt entities;
All advertising and other representations relating to regulated financial services reasonably identify the entity providing the regulated financial services;
No advertising or other representations state that an unauthorized entity is providing regulated financial services;
All entities using or benefitting from the common tradenames or marks (each, an “applicable entity”) are fully affiliated with each other, meaning that each applicable entity, for all other applicable entities, directly or indirectly controls the other applicable entity, or is directly or indirectly controlled by the other applicable entity, or is otherwise under full common control and ownership with the other applicable entity; and
All advertising, including use of common tradenames and trademarks, is conducted pursuant to written inter-company agreements and permissible under all other applicable law, including but not limited to federal trademark law and federal and state consumer protection law.
CONCLUSION
This memorandum confirms that considerable latitude exists for marketing regulated financial services. However, the Department will continue to enforce compliance with these financial service marketing regulations. State banks and other regulated financial service providers can protect their own brands and industries by requiring all vendors to comply with the laws requiring truth in the advertising of regulated financial services.
Formal determinations regarding exemption claims can be sought from and provided by the Department. Companies concerned with the legality of their operations or advertising can contact the Department’s Legal Division at (877) 276-5554.